Phala Network and NOTAI: Empowering Trustless AI with TEE Technology
Phala Network is proud to announce a partnership with NOTAI, a collaboration that combines Phala’s Trusted Execution Environment (TEE) technology with NOTAI’s innovative approach to AI agents. Together, we’re advancing secure and verifiable computing, enabling trustless, privacy-first AI applications for developers and users alike.
Why This Partnership Matters
As AI applications become more critical across industries, ensuring secure and tamper-proof execution is essential. NOTAI has integrated its NOTAI Agent into the Phala Cloud platform, leveraging Phala’s TEE infrastructure to provide verifiable, confidential AI workloads.
Phala’s TEE technology allows developers to run sensitive computations securely, ensuring zero-trust execution. For AI agents like NOTAI, this means providing provable trust and privacy while maintaining high performance and scalability.
Verifiable Trust: RA Explorer for NOTAI Agent
The execution of the NOTAI Agent is fully verified using Phala’s RA Explorer, a transparency tool that showcases TEE proofs. Developers and users can confirm the integrity of the NOTAI Agent’s execution through the NOTAI Agent TEE Proof. This transparency ensures that every computation is secure and trustworthy.
Integration into Phala Cloud
The partnership has already brought the NOTAI Agent onto the Phala Cloud dashboard, showcasing its deployment within the TEE environment. Developers can view and verify the NOTAI Agent directly in the Phala Cloud interface, further demonstrating the seamless collaboration between the two platforms.
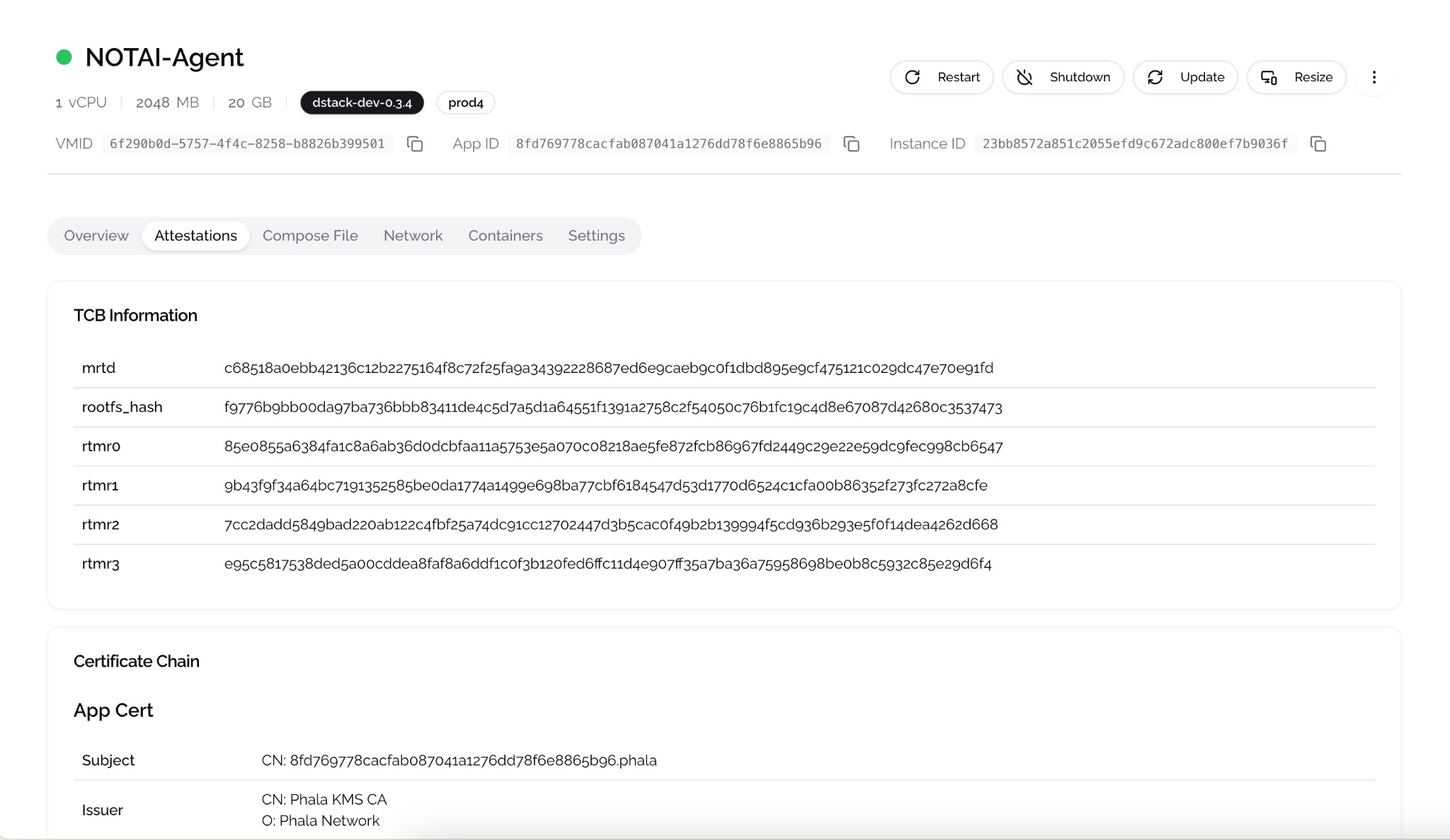
This integration highlights the ease with which developers can leverage Phala’s infrastructure for deploying AI agents and confidential workloads, enabling trustless computation at scale.
A Shared Vision for Trustless Computing
NOTAI and Phala Network share a common goal: making trustless technology accessible and affordable for developers. By combining Phala’s TEE-powered infrastructure with NOTAI’s AI capabilities, this partnership sets the stage for innovative, secure AI-driven applications.
About NOTAI
NOTAI focuses on building AI-driven solutions that prioritize transparency, security, and trust. With its integration into Phala Cloud, NOTAI continues to empower developers to create scalable, privacy-focused applications.
About Phala Network
Phala Network is a decentralized cloud computing platform leveraging Trusted Execution Environments (TEEs) to deliver secure and scalable solutions for AI applications, blockchain infrastructure, and privacy-focused systems.
Together, NOTAI and Phala Network are paving the way for developers to innovate securely and confidently in the trustless tech space. Stay tuned for more updates as this collaboration continues to grow.