Phala Network and Vana Network Join Forces to Usher in New Era for Decentralized Data Privacy
Overview
Phala Network and Vana Network are collaborating to enhance decentralized data privacy and security. This partnership integrates Phala’s Trusted Execution Environment (TEE)-powered solutions with Vana’s user-driven data contribution platform, ensuring robust confidentiality and verifiable data handling throughout its ecosystem.
Vana is the first open and decentralized network for data sovereignty, unlocking user-owned data as a new digital asset class. In an era where AI is driving immense value from user data, Vana ensures that data creators retain ownership of their data and capture a fair share of the value generated while enabling researchers to access unique datasets.
With the collaboration, Vana enables individuals to monetize their data securely while supporting decentralized AI advancements. With Phala’s TEE infrastructure, the validation and attestation processes in Vana’s platform gain additional layers of security and transparency.
Detailed Technical Integration
User-Centric Data Workflow in Vana
Phala’s TEE-based framework enhances Vana's data workflow by ensuring security and transparency at every stage:
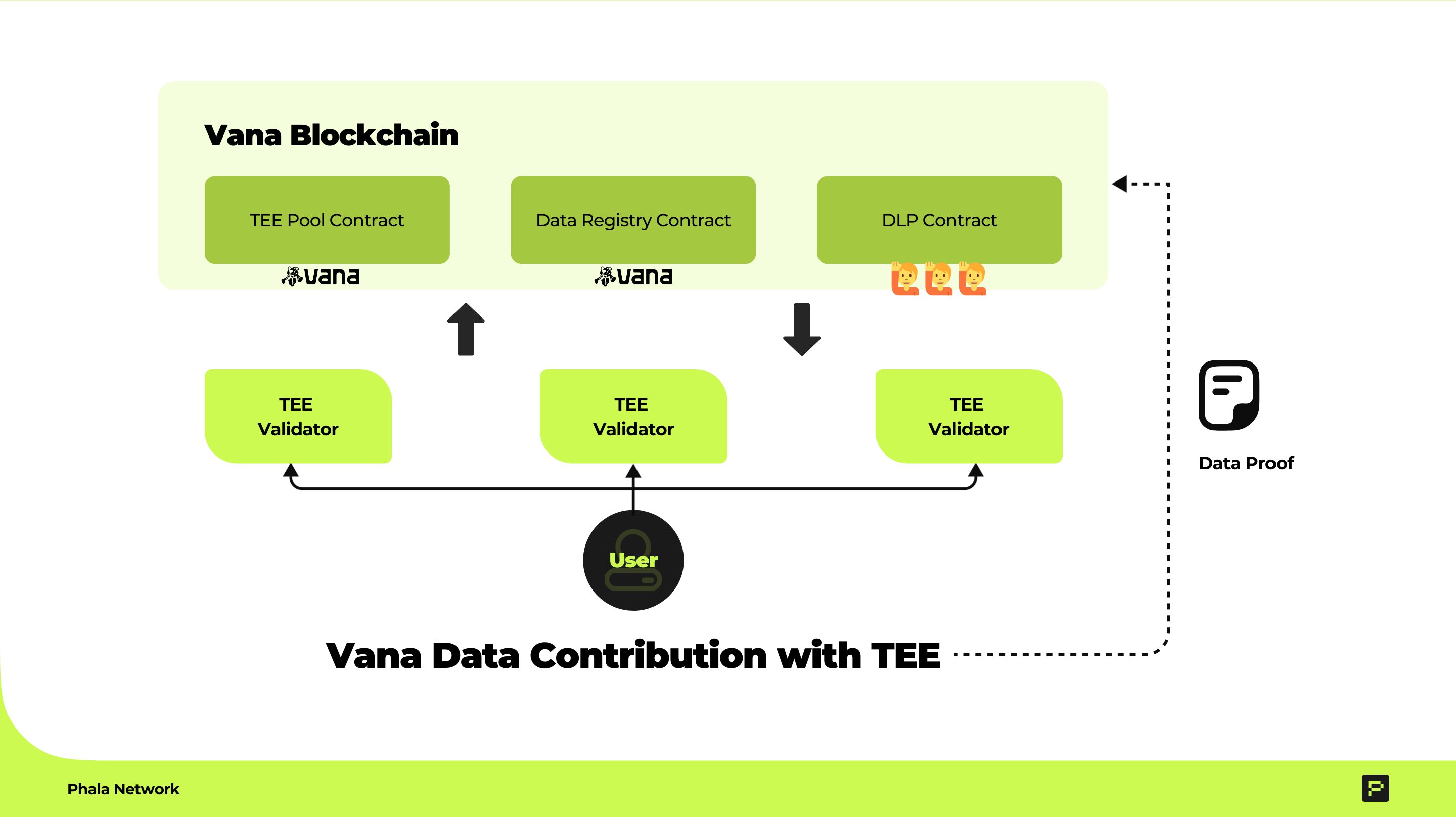
- File Submission to Data Registry Contract: The user begins by uploading their encrypted file to the Data Registry Contract, initiating the process of securing their data. Alongside this upload, the user submits a request for attestation to the TEE Pool Contract, signaling the need for validation and proof generation.
- Attestation by TEE Validator: Upon receiving the user's attestation request, the TEE Validator retrieves the file and follows the specified validation instructions. The validator executes the attestation process within a secure environment, ensuring the file's authenticity, integrity, and compliance with the given parameters. The result is a tamper-proof attestation securely tied to the file.
- Submission of Attestation and Proof to DLP Contract: The user receives the generated attestation and accompanying proof from the TEE Validator. These outputs are then submitted to the Data Liquidity Pool (DLP) contract, where they can be utilized for further operations, such as contribution verification or rewards allocation, ensuring a transparent and trusted workflow.
Enhanced Security with Phala’s TEE Solutions
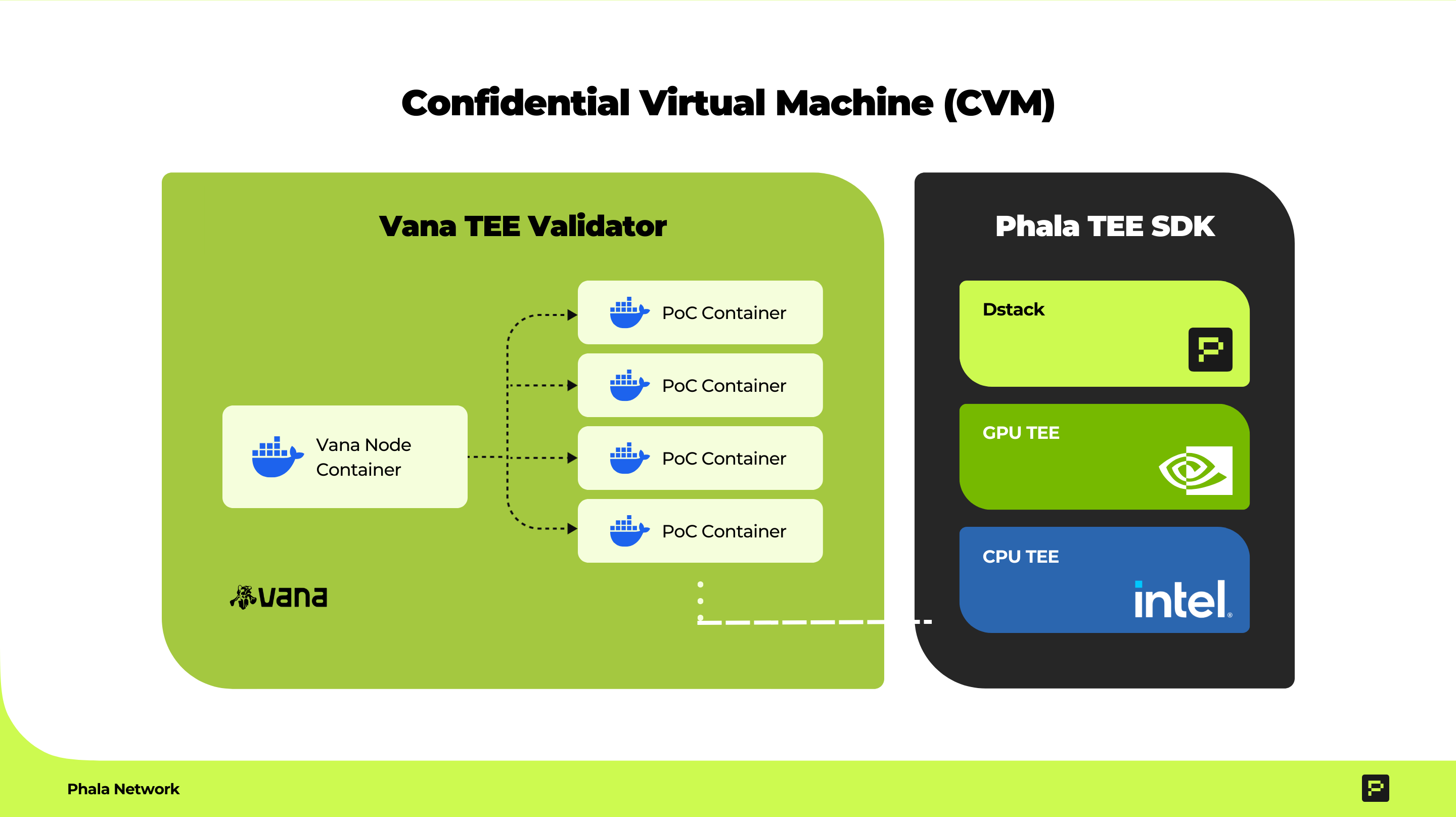
Integration of Vana TEE Validator with Phala
The Vana Network TEE validator utilizes Dstack, an open-source TEE SDK built by Phala, to provide a robust, confidential environment for secure data validation. This integration ensures that data is processed within a hardware-isolated Confidential Virtual Machine (CVM) while adhering to stringent privacy and security standards.
- Confidential Virtual Machine (CVM) Setup: Each Vana TEE node is provisioned within a dedicated CVM created through the Phala’s Dstack. This ensures complete isolation of execution environments and network access, safeguarding against external interference and protecting sensitive operations.
- Secure Data Handling via Blockchain Access: When users request attestations for their submitted data, the Vana TEE node fetches the required data from the Vana blockchain. This process occurs securely within the CVM, utilizing a controlled communication channel to ensure confidentiality and integrity.
- Execution Workflow within Docker Containers
- Dynamic Container Execution: The Vana TEE node dynamically downloads the required Proof of Contribution (PoC) Docker image from a remote repository to local storage.
- Validation and Proof Generation: The node launches the PoC Docker container inside the node container, executing the attestation logic alongside user data. This process generates a cryptographic proof of contribution, ensuring that validation is both accurate and tamper-resistant.
- Resource Cleanup: Upon completion, the PoC container is securely terminated, and all related execution context is cleared to maintain a clean state and prevent unauthorized data persistence.
- End-to-End Proof Delivery: The Vana TEE validator returns the generated proof to the user. The user can then upload this proof to the Vana blockchain, which validates the contribution and processes the appropriate rewards.
By leveraging Phala's TEE solution, Vana ensures a seamless, secure, and efficient attestation workflow, combining confidentiality and performance.
The Power of Dstack
The integration of the Dstack provides significant technical advantages for Vana nodes, ensuring secure, reliable, and efficient operations:
- Dynamic Nested Docker Networking: Each node operates within a Confidential Virtual Machine (CVM), using multiple Docker containers. These containers can dynamically launch new containers within themselves, creating a nested Docker network that enhances modularity and isolation.
- Isolation and Protection with TEE Hardware: Each Vana node runs in a dedicated CVM, ensuring that its execution environment and network access are fully isolated from the host operating system and hypervisor. This isolation is enforced by TEE hardware, providing robust protection.
- Secure Communication Channels: Sensitive node data is transmitted to the TEE through a secure communication channel, effectively preventing data leaks or unauthorized access during transmission.
- Integration via External Key Management Systems (KMS): The integration of node data is managed through an external Key Management System (KMS), ensuring seamless upgrades and migrations without compromising the security or integrity of operations.
- Verifiable Node Execution: The execution of Vana nodes can be validated through the Phala Attestation Service. This can be done on the blockchain or directly via a browser client, adding an extra layer of verifiability to the system. Check the attestation report of Vana Mainnet TEE-Proof-1 and TEE-Proof-2. These features collectively ensure that Vana’s infrastructure remains secure, scalable, and verifiable, meeting the rigorous demands of data privacy and secure computing.
Collaborative Impact on Decentralized Data Ecosystems
Phala and Vana Network’s partnership focuses on empowering users to securely contribute, validate, and monetize their data within decentralized systems. By combining Phala’s robust TEE solutions with Vana’s user-driven data platform, the collaboration sets a higher standard for privacy-focused applications in decentralized AI and data management.
Explore Phala’s approach to confidential computing through the documentation and Dstack Github Repo. For insights into Vana’s decentralized data initiatives, visit their official docs.