Understanding the Role of Root-of-Trust in TEE and Phala’s Decentralized Approach
In today’s digital age, the need for secure computing is more crucial than ever, especially with the rise of AI and blockchain applications. Ensuring that sensitive data, from AI models to financial transactions, remains secure and untampered with is essential. Enter the Root-of-Trust (RoT) — a fundamental concept in the world of Trusted Execution Environments (TEEs), which is at the heart of secure computation. This blog will break down the concept of RoT, explain its challenges, and how Phala Network is transforming it with its decentralized approach.
What is Root-of-Trust (RoT)?
Root-of-Trust (RoT) is the foundational security layer that ensures everything in a computing system can be trusted. It acts as the "lockbox" that holds critical secrets, like encryption keys, and ensures that the hardware or software handling sensitive tasks can be trusted. In computing, especially when it comes to TEEs, the RoT ensures that computations are done in a trusted and secure environment.
How Traditional Hardware-Based RoT Works
In hardware-based RoT, the security secrets are embedded directly into the hardware (like the CPU or GPU). This is great for security since it’s hard to tamper with physical hardware. However, it’s not foolproof. If someone manages to break into the hardware and access the keys stored inside, the entire system’s security collapses. The hardware-based RoT becomes irreparable once it’s breached. It’s like losing your lockbox — once someone has access to it, everything inside is vulnerable.
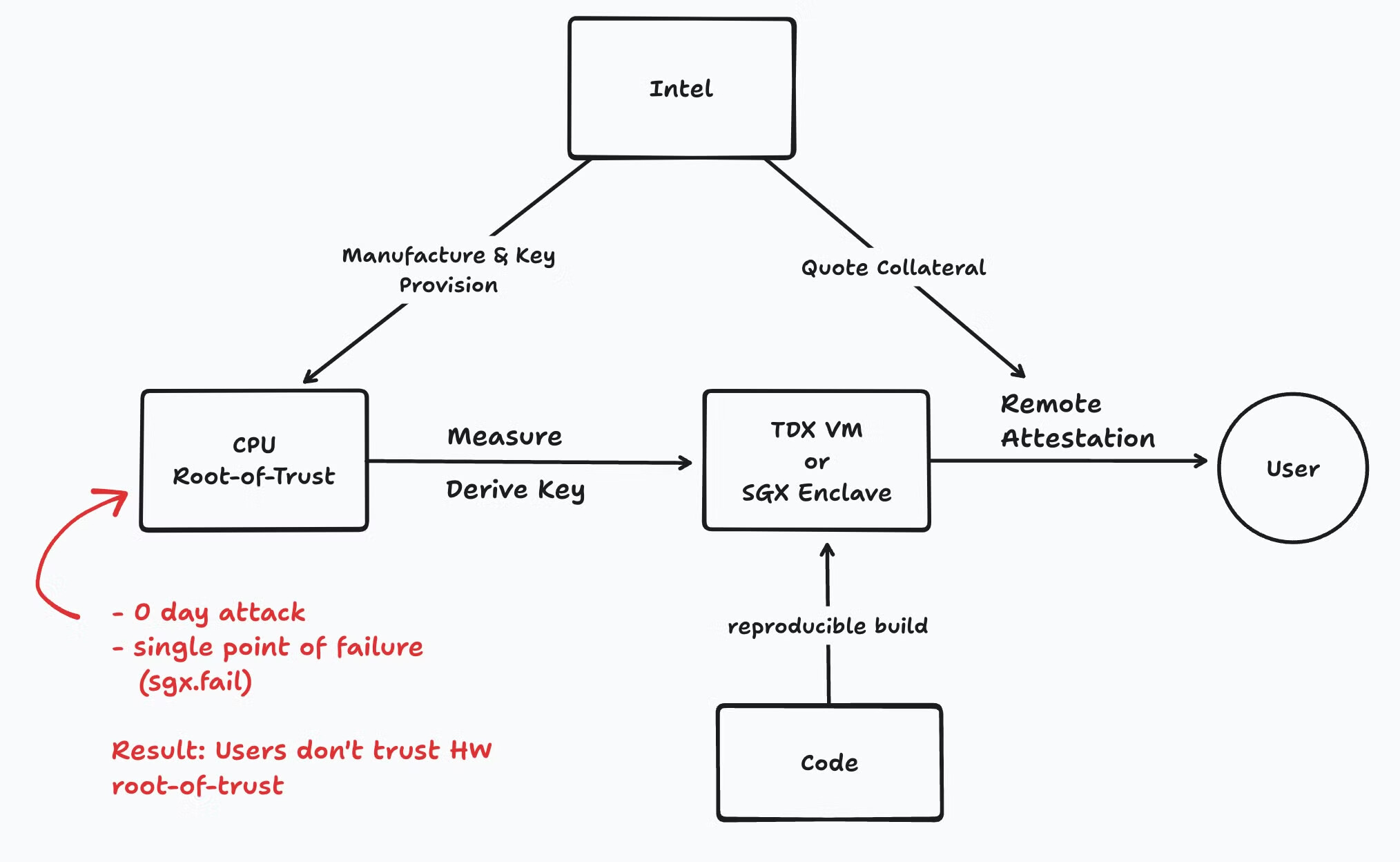
Some common issues with hardware-based RoT include:
- Unrecoverable Trusted Computing Base (TCB): If the hardware is compromised, even fixes through microcode updates may not help.
- Single Point of Failure: If the RoT in one piece of hardware is compromised, all the applications relying on that hardware’s security are affected.
The Move to Software-Based RoT
Recognizing the limitations of hardware RoT, the computing world has begun exploring software-based RoT. In a software RoT, the core security functions—like verifying the hardware’s state and generating encryption keys—are abstracted from the hardware and handled by software. This approach offers more flexibility, as it can bypass hardware failures or breaches.
In a software-based RoT:
- Measurement: The software verifies the authenticity of the hardware environment by checking its integrity before granting access to sensitive data.
- Key Derivation Service: The software generates the encryption keys needed to perform tasks like securing data and signing transactions. These keys are not tied to the hardware, so they can be moved between different machines, providing more flexibility.
Phala’s Decentralized Root-of-Trust: A New Era of Security
While software-based RoT solves many problems associated with hardware, it still faces one major challenge: “centralization.” If the software RoT is controlled by a single entity or system, it can become a target for attacks, and if breached, the security of the entire network is compromised.
This is where Phala Network’s decentralized Root-of-Trust model shines.
Decentralized Root-of-Trust: How it Works
Phala takes the software RoT model and decentralizes it, spreading trust across multiple independent nodes in the network. This way, no single entity can control the entire system, making it significantly more resilient to attacks.
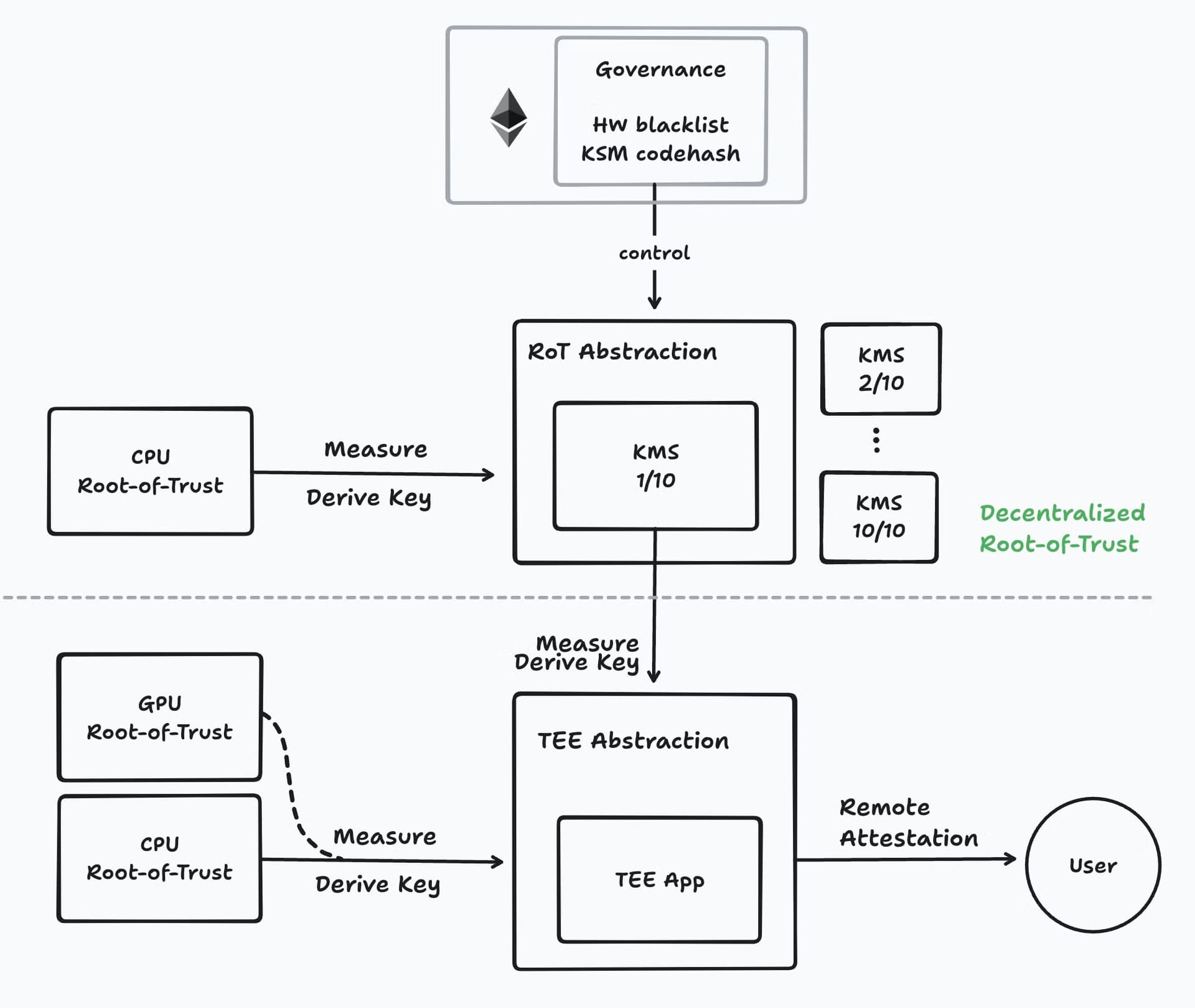
Here’s how Phala’s decentralized RoT works:
- Key Management System (KMS): Phala’s KMS is a distributed system that stores and manages the secrets needed for the network to function. Unlike a traditional centralized system, Phala uses Multi-Party Computation (MPC) to secure the secrets. In MPC, each node in the system only holds a fragment of the secret, and it takes the collaboration of multiple nodes to reassemble the secret and use it.
- TEE Integration: Phala’s RoT integrates with hardware TEEs as well, blending the security of hardware with the flexibility of software. This ensures that even if a single piece of hardware is compromised, the overall system remains secure because of the decentralized nature of the software RoT.
- Blockchain-Based Governance: The decentralized RoT is governed by blockchain-based smart contracts. These smart contracts manage the behavior of the nodes in the system, verifying that they are running the correct code and ensuring that compromised hardware is blacklisted. This removes the need to trust a single hardware manufacturer or provider.
- Economic Incentives: Phala uses cryptoeconomics to ensure that node operators behave honestly. Node operators must stake tokens as collateral, and if they act maliciously, they lose their stake. This incentivizes honest behavior and ensures the network remains secure.
Benefits of Phala’s Decentralized RoT
By decentralizing the Root-of-Trust, Phala addresses many of the vulnerabilities found in traditional RoT models:
- Confidentiality: Since the secrets are distributed across many nodes, attackers need to breach a majority of the nodes to access the full secret. This is much harder to achieve than compromising a single piece of hardware.
- Integrity: The system continuously verifies the code and environment running on the nodes through TEEs and MPC. Even if one part of the system is compromised, the other nodes can detect this and prevent further damage.
- Liveness: Decentralizing the RoT allows the system to tolerate failures. If some nodes go down or are compromised, the system keeps running, ensuring that services continue without interruption.
Closing thoughts: The Future of Secure Computing with Phala’s Decentralized RoT
Phala’s decentralized Root-of-Trust offers a much-needed upgrade to traditional security systems, especially in the world of blockchain and AI. By distributing trust across multiple nodes and integrating both hardware and software RoT, Phala ensures that applications built on their network remain secure, scalable, and flexible. For developers working with sensitive AI models or decentralized applications, Phala’s RoT model provides the robust security they need.
This new era of secure computing, powered by decentralized RoT, is paving the way for the future of AI and blockchain technology, offering unparalleled (without using prohibited terms) resilience, security, and flexibility.
To potential partners interested in Phala's TEE-as-a-service offering:
If you are excited about Phala’s decentralized Root-of-Trust and our TEE-as-a-Service infrastructure and would like to explore a partnership or learn more about how these solutions can enhance your AI or blockchain projects, feel free to reach out to us directly. We're always eager to collaborate with forward-thinking companies and developers who share our vision for secure, scalable, and decentralized computing.
Contact Us:
Visit our website: Phala Network
Or drop us an email at: [email protected]