Build Confidential dAGI
- Run AI Models Inside TEE
- RedPill by Phala Network runs AI models securely in a TEE, ensuring data privacy and integrity.

ZK can not guarantee privacy in public state sharing scenario, the rollup sequencer can see all data even if they prove the computation done correctly.
FHE cannot prove that the computations performed as expected, also the decryption integrity can not guaranteed by the companioned MPC.
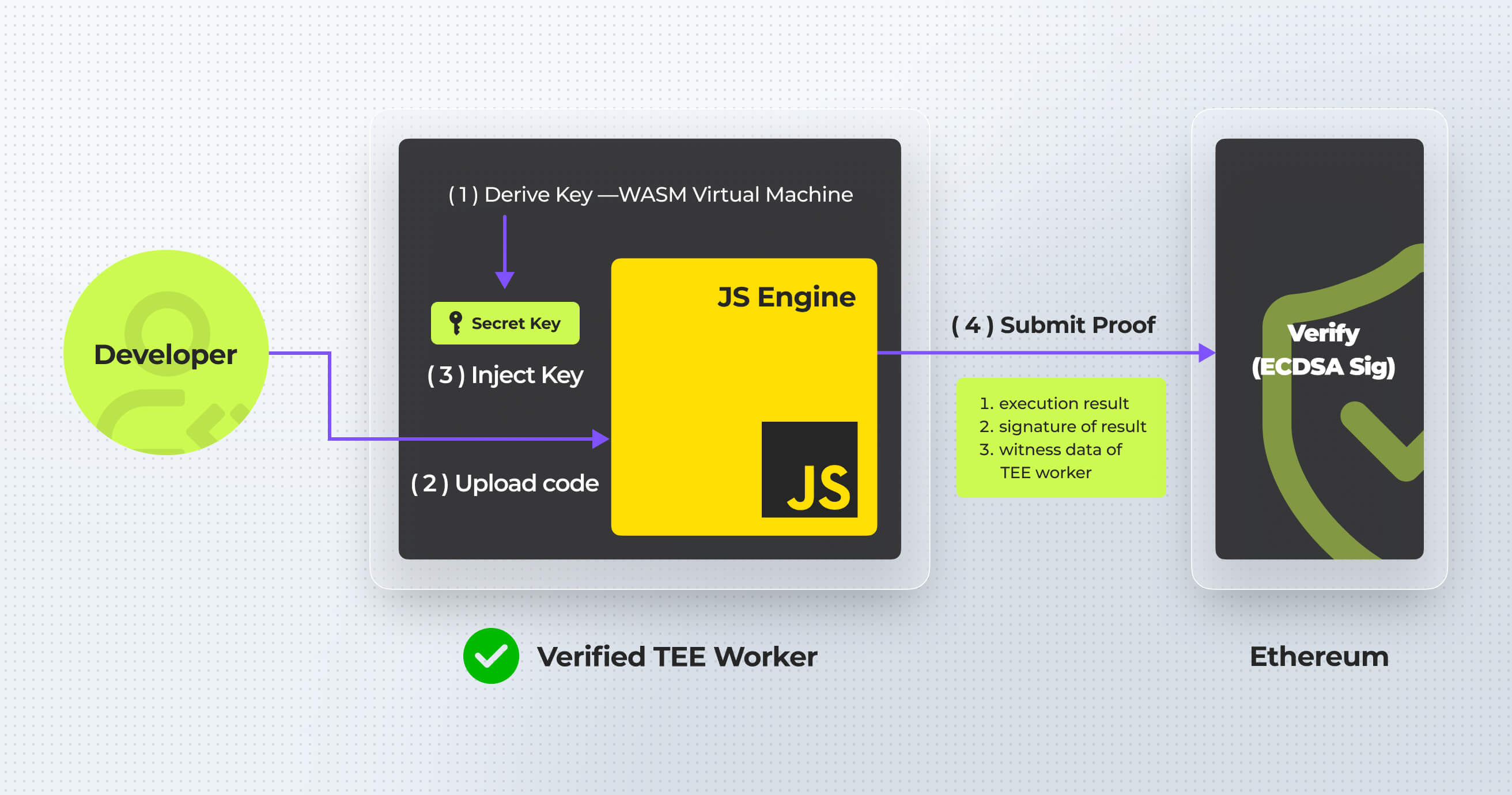
Trusted Execution Environments (TEE) create secure enclaves for processing sensitive data, allowing applications to execute securely in an isolated environment, without trust the privileged software, such as hypervisors or host operating systems.
Phala TEE supports confidential data exchange use cases, such as MEV (Maximal Extractable Value), blockchain games, and AI model training.
With 35,000 TEE workers, Phala’s Phat Contract is programmable to meet the needs of various blockchain projects, ensuring robust availability.
Phala TEE ensures your application, project, or blockchain use case remains operational and free from legislative risks, maintaining trust across multiple parties.
Our SDKs for Rust and JavaScript enable developers to launch their applications on our TEE network quickly, often within hours.
TEE can eliminate the collusion risk exist in MPC network, and prove the validity of encryption and decryption without rely on ZK.
Learn moreTo hedge the bugs in ZK implementation, TEE can be used as a 2-factor verifier to zk-Rollups. Inspired by Vitalik Buterin's presentation and a recent post by Justin Drake.
Learn moreCheck out our documentation and GitHub examples.
PHA is the native token of the Phala blockchain
Provide hardware to the network and earn rewards!
Help secure the network and earn yield by staking your PHA
Take an active part in deciding the future direction of off-chain compute
Bring tokens to and from the Phala Blockchain with SubBridge
Explore the architecture and power of Phala Network