
In May 2025, Phala Network’s dstack – an open-source framework for confidential containers – underwent its first ever security audit conducted by independent experts at zkSecurity. This audit represents the first comprehensive review of a Trusted Execution Environment (TEE) platform at the operating system level, and its results validate dstack’s ambitious “zero trust compute” architecture.
What dstack does?
Dstack powers Phala Cloud, a zero-trust cloud computing service supporting both TEE CPUs and GPUs. The framework allows developers to deploy unmodified Docker images to TEEs with enhanced security, verifiability, and censorship resistance.
How does dstack enforce trust? It uses a combination of secure boot, cryptographic measurements, and remote attestation. These measurements form the chain of trust – any change in the bootloader, OS image, or container config will alter the hashes, and thus can be detected by verifying the attestation.
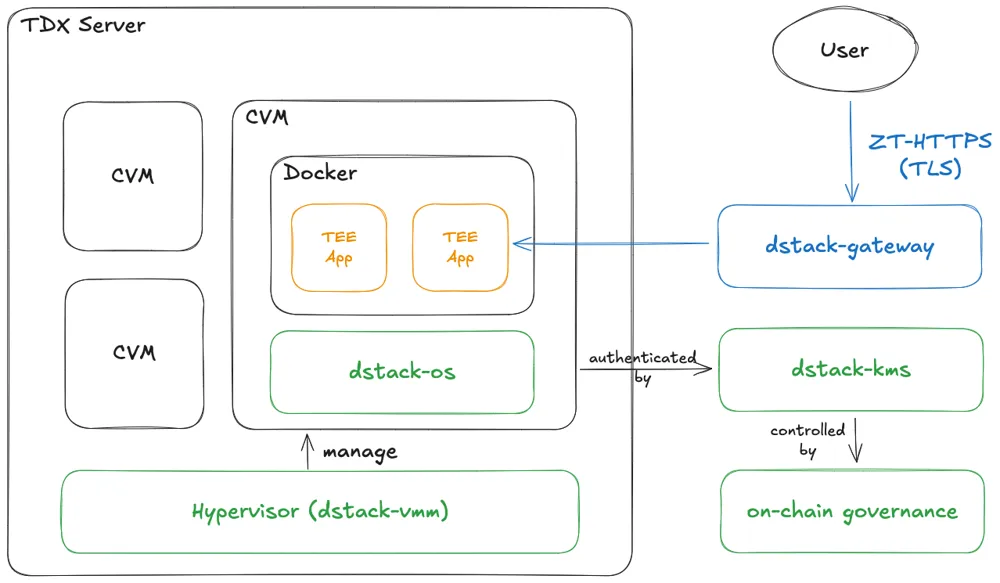
Key components include:
- dstack-OS: The cornerstone minimized operating system running within the TEE
- dstack-KMS: A key management service as the distributed Root-of-Trust, issuing cryptographic keys to a validated Confidential Virtual Machine (CVM)
- dstack-Gateway: A secure ingress component providing verifiable domain management, allowing users to connect to the TEE apps over TLS with remote attestation built in
- dstack-VMM: A service managing the lifecycle of CVMs
The big picture is a full chain-of-trust from hardware to application: the hardware and KMS are the Root-of-Trust, the OS is a reproducible minimal image, and the application container is launched in a measured environment where all parties can verify what’s running.
Security audit: what was reviewed
The audit was conducted by zkSecurity between May and June 2025. It covered both the dstack and meta-dstack repositories, focusing on low-level components (remote attestation, key management, system setup) and OS image generation. The audit is the first of its kind for a confidential compute stack based on Intel TDX.
Two areas were in scope:
- Low-level libraries and tooling, including remote attestation components, guest agent service, and utilities
- Image-related files for the operating system, including Yocto BitBake recipes and initialization scripts
The architecture includes a chain of verifiability from boot firmware to the container. All key configuration and runtime events are measured and recorded before secrets are issued. The guest OS is built as a minimal image with separate profiles for development and production, with the latter stripped of debug interfaces and login consoles.
Key findings and changes
The audit validated the architecture and offered several key improvements, which have since been implemented:
- A high-severity issue with the OVMF build configuration, now fixed with a more secure implementation
- Medium-severity issues related to terminal binaries, symbolic link handling, and environment variable protection
- Several low-severity findings and documentation improvement recommendations
The Phala team responded promptly to all findings, implementing fixes and enhancing documentation, demonstrating their commitment to maintaining the highest security standards.
Confidential Compute Changed—Today
The successful audit of dstack marks a watershed moment for confidential computing. For years, cloud providers asked users to trust their security promises. Phala's dstack flips this to "don't trust – verify", with every layer of the stack now having both hardware attestation proofs and external security validation.
This effectively moves cloud computing from trust toward true trustlessness. Developers using Phala Cloud can now rely on a publicly audited foundation, focusing on verifying just their application rather than scrutinizing countless components. The combination of reproducible builds, cryptographic measurements, and third-party review transforms platform security from a black box to a transparent system.
This sets a new industry precedent. Other providers will likely undergo similar rigorous audits and publish results. Having cryptographically verifiable infrastructure is powerful, but independent auditing builds the final layer of confidence even skeptical enterprises need.
Get full report: https://phala.network/dstack/dstack-audit.pdf