
Executive Summary
The financial services industry stands at a critical inflection point where traditional security models can no longer support the data-intensive, AI-driven operations essential for competitive advantage. As financial institutions embrace cloud computing, artificial intelligence, and cross-border collaboration, they face an impossible choice between operational innovation and regulatory compliance.
Privacy computing eliminates the traditional trade-off between innovation and security by providing mathematical guarantees of data protection throughout the entire processing lifecycle. This whitepaper demonstrates that privacy computing is no longer a technical luxury but a business imperative that directly impacts market access, competitive positioning, and regulatory compliance in the evolving financial landscape.
Financial institutions implementing privacy computing capabilities unlock premium market opportunities, achieve superior regulatory compliance, and enable innovative services previously impossible due to security constraints—transforming data protection from a cost center into a competitive advantage while addressing the mounting cyber risks that threaten industry stability.
1. The Privacy Computing Imperative in Financial Services
1.1 The Critical Security Gap in Financial Operations
Modern financial institutions process extraordinary volumes of sensitive data including customer financial records, proprietary trading algorithms, credit risk models, and cross-border transaction flows. Traditional security approaches protect data at rest and in transit but create critical vulnerabilities during processing when data must be decrypted for computation.
This fundamental weakness has become increasingly dangerous as cyberattacks escalate in both frequency and severity. According to the 2024 CrowdStrike global threat report, financial services companies face sophisticated threat actors who exploit the exact vulnerabilities that traditional security models cannot address—data exposure during processing operations.
Privacy computing technologies address this gap by maintaining cryptographic protection throughout the entire data lifecycle, using hardware-based trusted execution environments (TEEs) that preserve encryption even during active processing. This approach directly counters the evolving threat landscape where cybercriminals increasingly target processing environments and exploit third-party integrations.
1.2 Converging Regulatory and Market Pressures
The financial services regulatory landscape has evolved into a complex matrix of overlapping requirements that traditional cloud security cannot adequately address, while cyber risk regulations continue to strengthen:
Global Financial Privacy Frameworks:
- GDPR (2018): Established mathematical requirements for technical safeguards with data minimization and purpose limitation principles
- CCPA/CPRA (2020-2023): Extended similar protections with enhanced enforcement mechanisms for financial data
- EU AI Act (2024): Introduced risk-based requirements for AI systems in financial services, with highest standards for credit scoring and automated decision-making
- US SEC Cyber Disclosure Rule: Mandating improved reporting, transparency, and governance of cybersecurity risk
- Cyber Incident Reporting for Critical Infrastructure Act (CIRCIA): Requiring critical infrastructure entities to report cyber incidents
Financial Services Compliance Multipliers:
- Basel III/IV: Enhanced risk management and capital requirements demanding sophisticated data analysis while maintaining confidentiality
- PCI DSS: Payment card industry standards requiring cryptographic protection of transaction data throughout processing
- SOX: Financial reporting accuracy requirements necessitating secure data processing and audit trails
- Anti-Money Laundering (AML): Cross-border transaction monitoring requiring privacy-preserving data sharing
Emerging Cyber Risk Regulations:
Financial institutions now face heightened regulatory scrutiny around cybersecurity capabilities, with 70% of surveyed institutions citing increased compliance with regulations as the primary driver for cybersecurity capability maturation. New regulations demand mathematical proof of security controls rather than policy-based assurances.
Cross-Border Banking Crisis:
Privacy Shield invalidation and Schrems II decisions have created operational nightmares for global financial institutions. Standard Contractual Clauses face heightened scrutiny, while data localization requirements conflict with global banking operations. Financial institutions face regulatory penalties, operational restrictions, and competitive disadvantage without privacy computing solutions.
1.3 The Business Case for Privacy Computing in Finance
Market Access and Revenue Protection:
Privacy-conscious institutional clients and regulatory bodies increasingly select financial partners based on demonstrated security capabilities rather than policy promises. With 65% of financial institutions expressing concern about their ability to address cyber risks through existing capabilities, privacy computing provides mathematical differentiation. Financial institutions without privacy computing capabilities face exclusion from high-value market segments including:
- Government banking requiring mathematical security guarantees
- Healthcare sector financing with PHI protection requirements
- Cross-border institutional services with data sovereignty needs
- High-net-worth wealth management demanding IP protection
Competitive Advantage Through Technical Differentiation:
Privacy computing enables financial institutions to transform regulatory compliance from operational burden into competitive advantage. Instead of accepting security limitations, institutions can offer mathematically guaranteed privacy protection that enables premium services and pricing strategies. This becomes critical as 57% of financial institutions worry about keeping pace with emerging technologies and their associated cybersecurity requirements.
Risk Mitigation and Operational Efficiency:
Beyond compliance benefits, privacy computing significantly reduces:
- Cyber insurance premiums through demonstrable risk reduction
- Regulatory penalty exposure through technical compliance guarantees
- Audit costs through automated compliance verification
- Data breach impact through mathematical containment of exposure
- Third-party risk exposure, addressing the top capability weakness cited by 65% of survey respondents
The Strategic Imperative:
Financial institutions failing to implement privacy computing face mounting regulatory penalties, client losses, and competitive disadvantage as privacy computing becomes the baseline expectation for institutional financial services. With cybersecurity budgets averaging only 13% of IT spending and 70% of institutions acknowledging significant underspending, privacy computing transforms security from a cost burden into a competitive differentiator fundamental to sustainable competitive positioning in the evolving financial landscape.
2. Industry Leadership: Setting New Standards
2.1 JPMorgan Chase: Data Sovereignty & Secure Data Access Monetization
JPMorgan Chase is driving industry change by monetizing secure access to customer data for fintechs—an approach only possible due to major investments in privacy computing infrastructure. In July 2025, the bank announced it would begin charging fintechs substantial fees for API-driven access to customer bank data, citing significant investments in systems designed to protect consumer data at every stage. JPMorgan's secure data sharing is built upon an architecture ensuring stringent data sovereignty and regulatory compliance—making privacy protection the technical and commercial foundation of its fintech partnerships.
Industry Impact:
This move signals a shift where privacy computing and hardware-rooted data controls are a baseline for financial data exchange. JPMorgan’s robust systems have become central to justifying its premium services, with downstream fintechs and aggregators required to meet similarly high standards. The bank’s leadership is redefining privacy protection as a source of revenue and a universal requirement for competitive access, rather than a cost center or technical afterthought.
2.2 Bank of America: Zero Trust Architecture & Response to 2025 Mega-Breach
A major Advanced Persistent Threat (APT) attack was detected at Bank of America in July 2025, impacting over 38 million customers and exposing personal info and internal communications. The breach exploited a third-party tool months prior to detection, highlighting sector-wide supply chain vulnerabilities. BoA’s incident response centered on a comprehensive upgrade to zero trust security architecture, emphasizing:
- Trusted Execution Environments and behavioral analytics for continuous authentication and privilege verification.
- Isolation of affected systems and rapid regulatory reporting.
- Enhanced third-party oversight, moving toward pervasive encryption and hardware-level data protection to address gaps exploited by attackers.
Strategic Impact:
This crisis has made BoA’s zero trust and privacy computing overhaul an industry benchmark, as the entire sector reconsiders its incident response, supply chain risk, and the criticality of TEEs in trusted segments. Zero trust frameworks and privacy-enhancing computation are now recognized as not only regulatory and customer expectations, but as existential priorities—especially as high-profile breaches hit the news.
3. Financial Services Applications: Privacy Computing in Action
3.1 Privacy-preserving Data Collaboration Platform for financial institutions
Best practice industry: Financial Services + AI Fraud Detection + Regulatory Compliance
Target applicable enterprises: Multi-bank consortiums, credit card networks, insurance fraud coalitions, regulatory compliance alliances, cross-border payment networks, financial crime prevention partnerships.

Challenge
A consortium of major financial institutions needed to develop sophisticated anti-money laundering (AML) and fraud detection models by leveraging combined transaction insights across institutions. However, stringent regulatory requirements (PCI DSS, SOX, Basel III), competitive sensitivities around customer transaction patterns, and data localization mandates prohibited direct financial data sharing, making collaborative fraud prevention impossible through conventional methods.
Solution Highlights
TEE-Based Federated Learning: Implementation of federated learning protocols within trusted execution environments (TEEs), enabling each organization to train AI models locally while contributing encrypted model updates to a shared global model. Raw data never leaves each organization's security perimeter.
Secure Multi-Party Computation in TEEs: Advanced cryptographic protocols aggregate local model updates using homomorphic encryption within confidential computing enclaves. This prevents any participant from accessing others' proprietary information while enabling collaborative model improvement.
Hardware-Verified Attestation: Each federated learning node operates within verified TEEs providing cryptographic proof of system integrity. Remote attestation enables participants to validate that partners use approved software before sharing model updates, creating mathematically guaranteed trust.
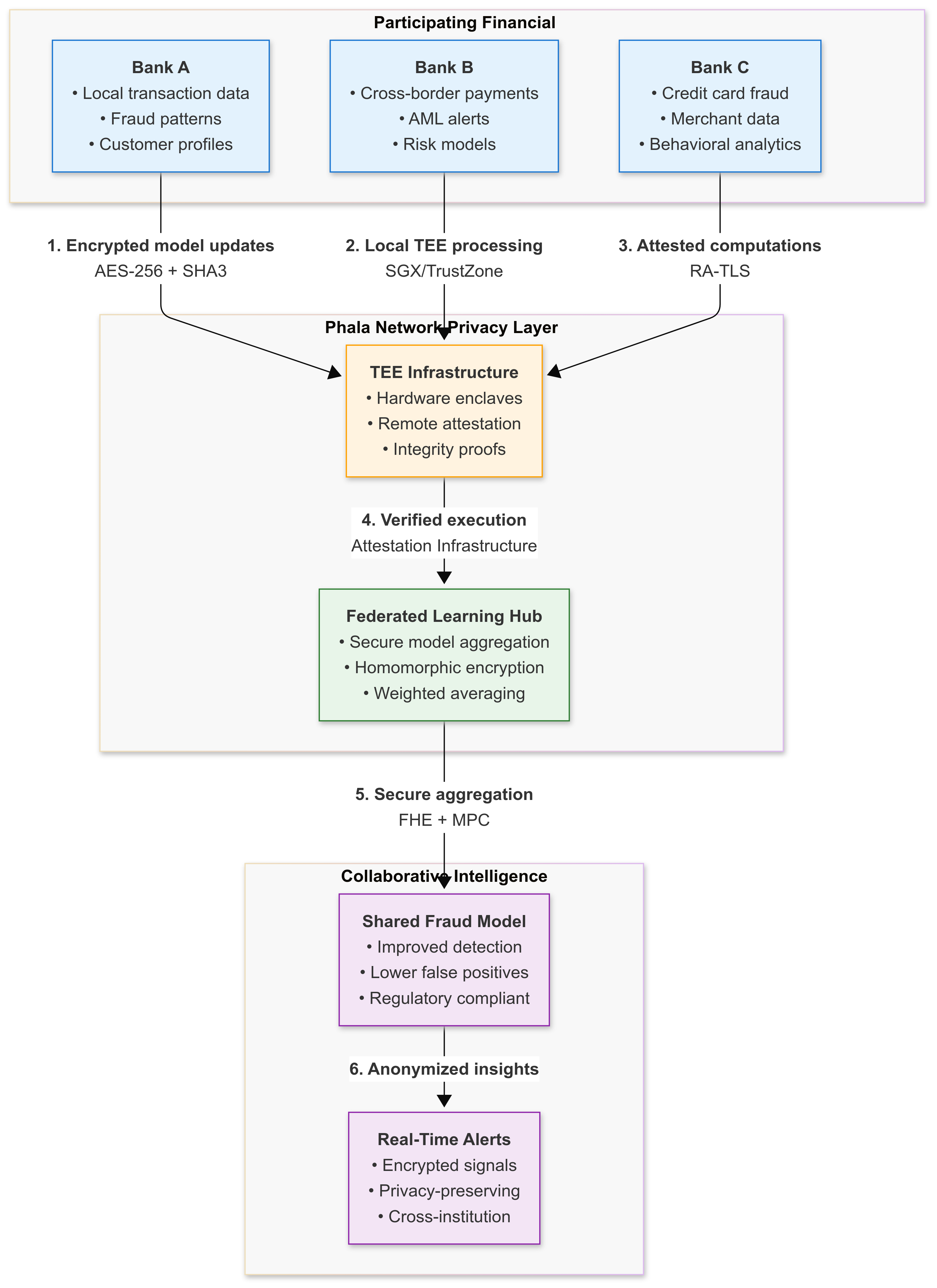
Results and Impact
The federated learning implementation enabled participating organizations to develop AI models with 35% improved fraud detection rates compared to single-organization training, while false positive rates decreased substantially due to diverse training data representation. Privacy computing made this collaboration possible by providing mathematical guarantees that competitive information would remain protected throughout the process.
3.2 Trusted Large Language Model Platform for financial institutions
Best practice industry: Financial Services + AI + SaaS
Target applicable enterprises: Investment banks, asset management firms, insurance companies with proprietary models, hedge funds, private equity firms, regulatory compliance departments

Challenge
A multinational investment bank required LLM capabilities across its global trading, research, and client advisory teams while maintaining strict control over proprietary trading strategies and confidential client information. Financial regulatory policies and competitive concerns prohibited sending sensitive market data to external AI services, creating a choice between accepting security risks or forgoing AI benefits entirely.
Solution Highlights
Confidential LLM Deployment: Enterprise-grade large language models deployed within confidential computing enclaves that process financial data without exposing information to external parties. Hardware-level isolation ensures even cloud administrators cannot access proprietary trading algorithms or client portfolios during AI processing.
Role-Based Secure Access in TEEs: Sophisticated access controls implemented within TEEs ensure traders, analysts, and advisors only interact with data appropriate to their roles and compliance clearances. Fine-grained data isolation maintained while preserving AI functionality across different business units and geographic regions.
Results and Impact
The implementation enabled global financial teams access to AI capabilities without compromising proprietary trading strategies or client confidentiality. Privacy computing made enterprise AI deployment feasible by providing mathematical guarantees that sensitive financial information would remain protected throughout processing, enabling new forms of cross-functional collaboration in research, trading, and client advisory services.
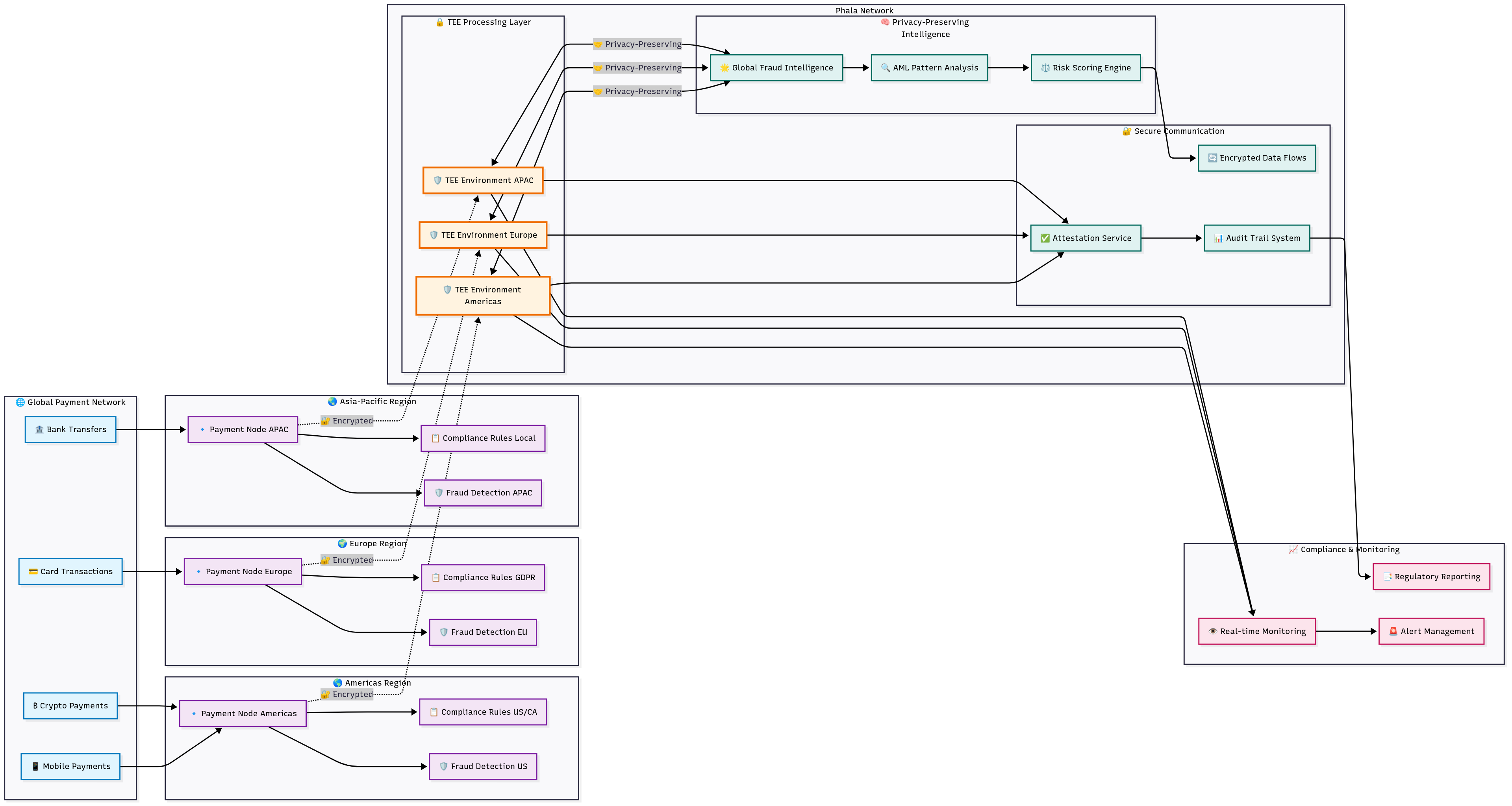
3.3 Cross-Border Payment Processing and Compliance
Best practice industry: Payment Processing + AI
Target applicable enterprises: Global payment processors, cross-border remittance services, digital wallet providers, cryptocurrency exchanges, international money transfer operators, banking correspondent networks.

Challenge
A global payment processor handling billions in daily transaction volume needed sophisticated fraud detection and regulatory compliance across multiple jurisdictions while adhering to conflicting privacy regulations and maintaining operational confidentiality of security measures.
Solution Highlights
TEE-Based Transaction Processing: All payment processing occurs within trusted execution environments providing mathematical isolation from infrastructure administrators and external entities. Transaction data remains encrypted throughout processing, addressing fundamental vulnerabilities in traditional payment systems.
Privacy-Preserving Fraud Detection: Advanced machine learning models analyze transaction patterns within secure enclaves, protecting both customer transaction data and proprietary fraud detection algorithms. This enables sophisticated threat detection without exposing sensitive information to external systems.
Cross-Jurisdictional Compliance Automation: Automated compliance monitoring processes transaction flows according to multiple regulatory frameworks simultaneously, with compliance rules executed within secure environments that prevent unauthorized access to sensitive operational data.
Results and Impact
The privacy computing implementation achieved 47% improvement in fraud detection accuracy through enhanced data analysis capabilities while maintaining full compliance with privacy regulations across all operating jurisdictions. Cross-border processing costs decreased 35% through operational automation, while regulatory audit preparation time was reduced by 80% through automated compliance documentation.
3.4 AI-Powered Credit Risk Assessment Platform
Best practice industry: Credit Risk Management + AI
Target applicable enterprises: Investment banks, commercial lending institutions, credit rating agencies, peer-to-peer lending platforms, trade finance providers, asset-based lending companies.
Challenge
A multinational investment bank required advanced AI models for credit risk assessment using cloud infrastructure while protecting proprietary algorithms, sensitive customer financial data, and maintaining compliance with banking regulations across multiple markets.
Solution Highlights
Confidential AI Model Deployment: Proprietary credit scoring and risk assessment models deployed within confidential computing enclaves that process customer financial data without exposing algorithms or data to cloud providers. Hardware-level isolation ensures complete protection of intellectual property and customer information.
Secure Multi-Source Data Integration: The platform integrates financial data from multiple sources including credit bureaus, transaction history, and market data within trusted execution environments. Data remains encrypted throughout integration and analysis processes.
Privacy-Preserving Model Training: Federated learning protocols enable model enhancement across different customer segments and geographic regions without centralizing sensitive financial data. Each data source contributes to model improvement while maintaining cryptographic control over information.
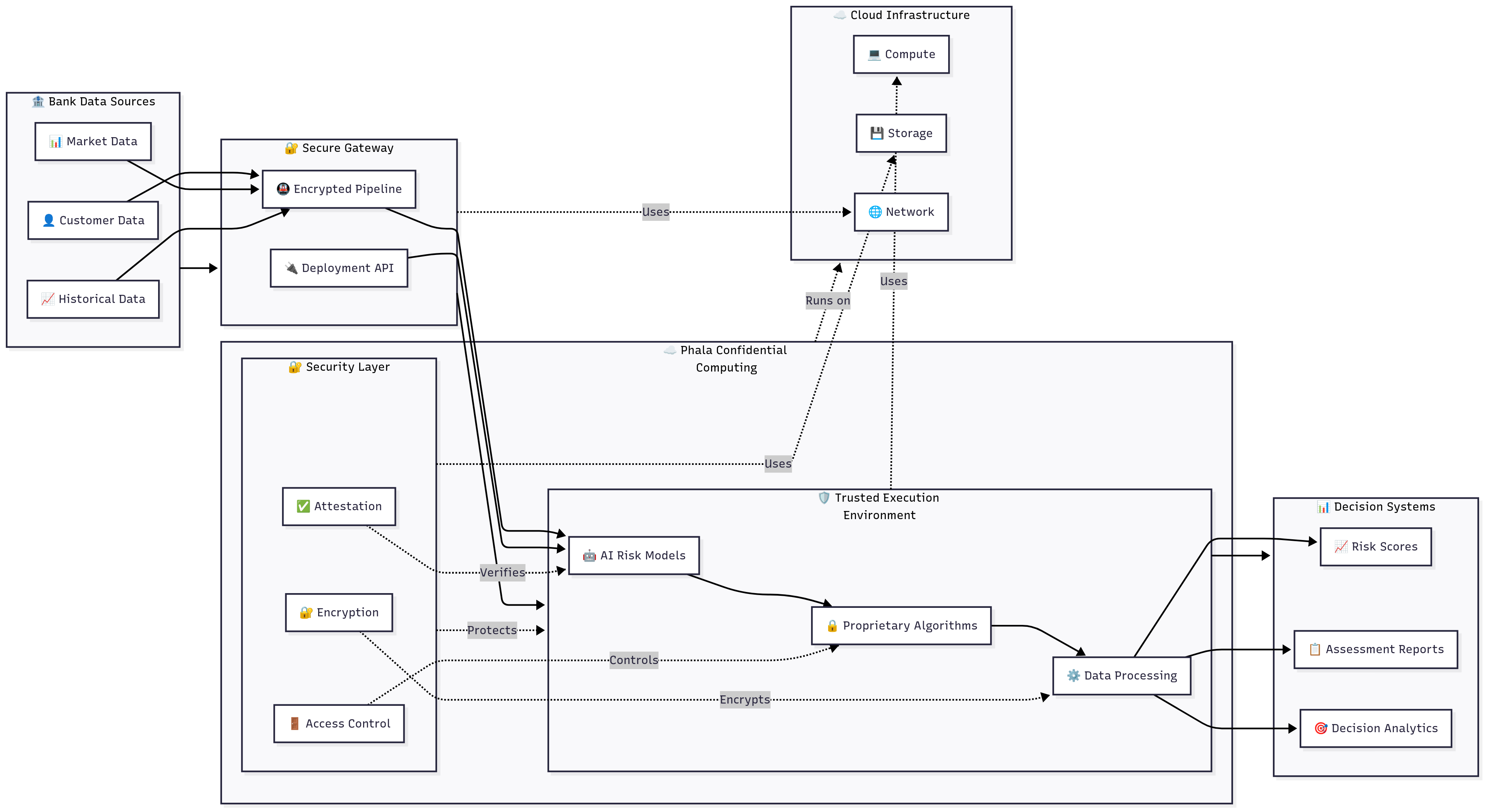
Results and Impact
The implementation delivered 38% improvement in credit risk assessment accuracy through access to enhanced data sources and more sophisticated analytical models. Model intellectual property remained completely protected, while customer data privacy was maintained throughout all processing operations. Cloud deployment costs were reduced 42% compared to on-premises alternatives while achieving superior security posture.
3.5 Regulatory Technology (RegTech) Compliance Platform
Best practice industry: RegTech + AI + Compliance
Target applicable enterprises: Financial services conglomerates, multi-jurisdictional banks, insurance companies, asset management firms, broker-dealers, financial holding companies.

Challenge
A financial services conglomerate required comprehensive regulatory compliance monitoring across multiple business units and jurisdictions while protecting sensitive operational data and maintaining confidentiality of compliance strategies and risk management approaches.
Solution Highlights
TEE-Based Compliance Monitoring: Sophisticated compliance algorithms process sensitive operational data from multiple business units within hardware-protected environments. Compliance rules and monitoring logic remain confidential while analyzing comprehensive operational information.
Automated Regulatory Reporting: Regulatory reports generated automatically from sensitive operational data without exposing underlying information to reporting systems or personnel. This approach improves reporting accuracy while maintaining operational confidentiality.
Cross-Business Unit Intelligence: Privacy-preserving analytics enable identification of compliance risks and operational patterns across different business units without exposing sensitive information between divisions. Shared insights improve overall compliance posture while maintaining information barriers.
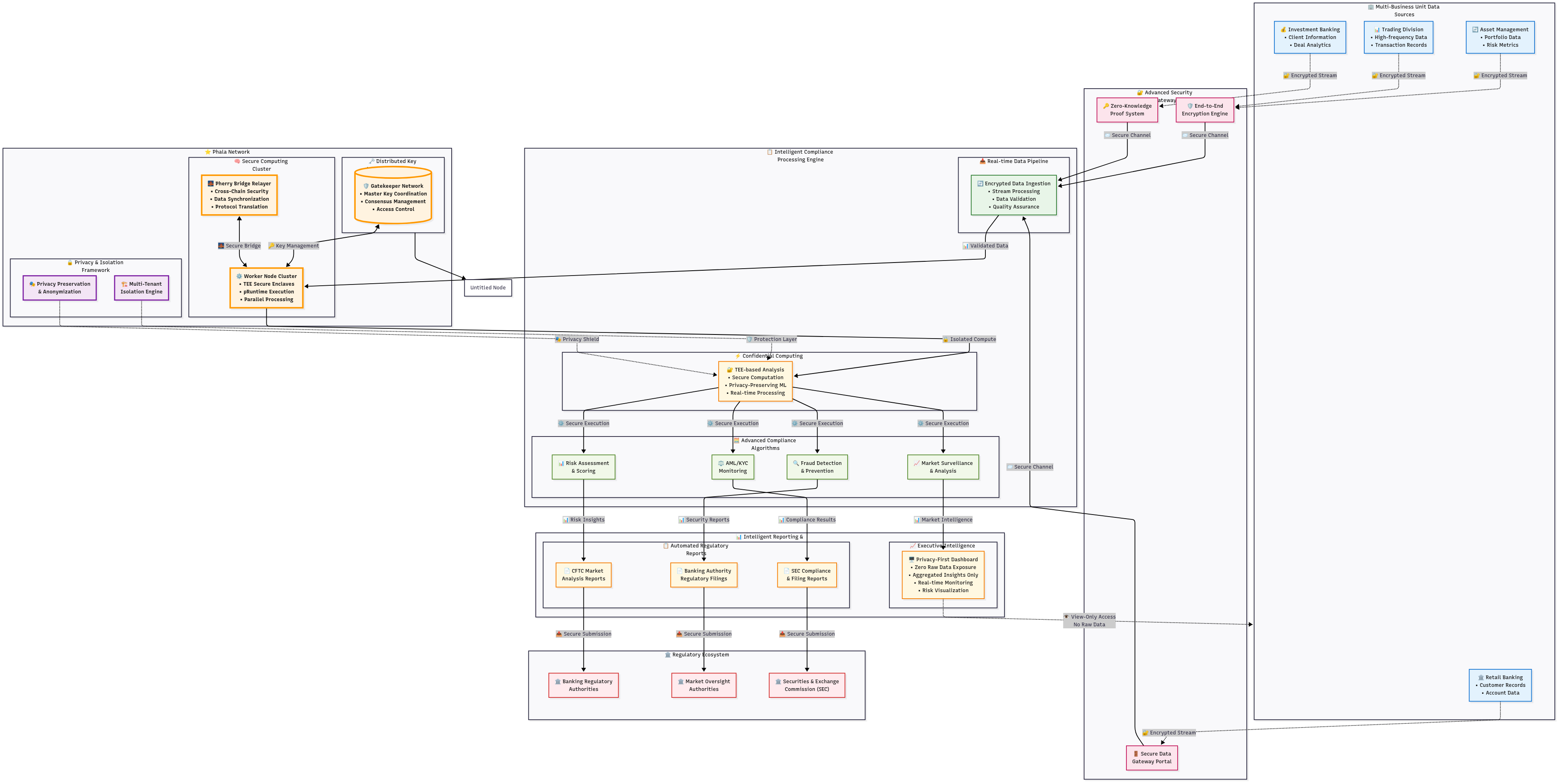
Results and Impact
The platform reduced regulatory compliance costs by 53% through automation and standardization while improving compliance accuracy through comprehensive data analysis. Regulatory relationships strengthened through enhanced reporting capabilities and demonstrated commitment to privacy protection. All business units maintained operational confidentiality while benefiting from shared compliance intelligence.
3.6 Digital Lending Platform for SME Financing
Best practice industry: FinTech + AI + SME Financing + Digital Lending
Target applicable enterprises: FinTech startups, traditional bank digital divisions, SME financing platforms, cross-border lending services, supply chain finance companies, alternative lending providers.

Challenge
A fintech startup specializing in small and medium enterprise financing needed to process sensitive business financial data from multiple sources while making real-time lending decisions. The company faced the critical challenge of maintaining data privacy while integrating with traditional financial institutions and ensuring compliance with data protection regulations across multiple jurisdictions without compromising operational efficiency.
Solution Highlights
Confidential Credit Scoring Environment: Proprietary credit scoring algorithms deployed within secure computing enclaves that process sensitive SME financial data without exposing information to cloud providers or internal personnel. Hardware-level data protection ensures complete confidentiality of both algorithms and customer data during processing.
Multi-Source Data Integration in TEEs: Automated data ingestion pipelines encrypt SME financial data before processing within the secure environment. Bank statements, accounting records, and credit bureau data are processed collectively while maintaining strict data isolation and preventing unauthorized access.
Privacy-Preserving Banking Partnerships: Integration APIs enable traditional banks to contribute data without exposure risks, fostering secure collaborative lending ecosystems where sensitive information remains protected throughout the decision-making process.
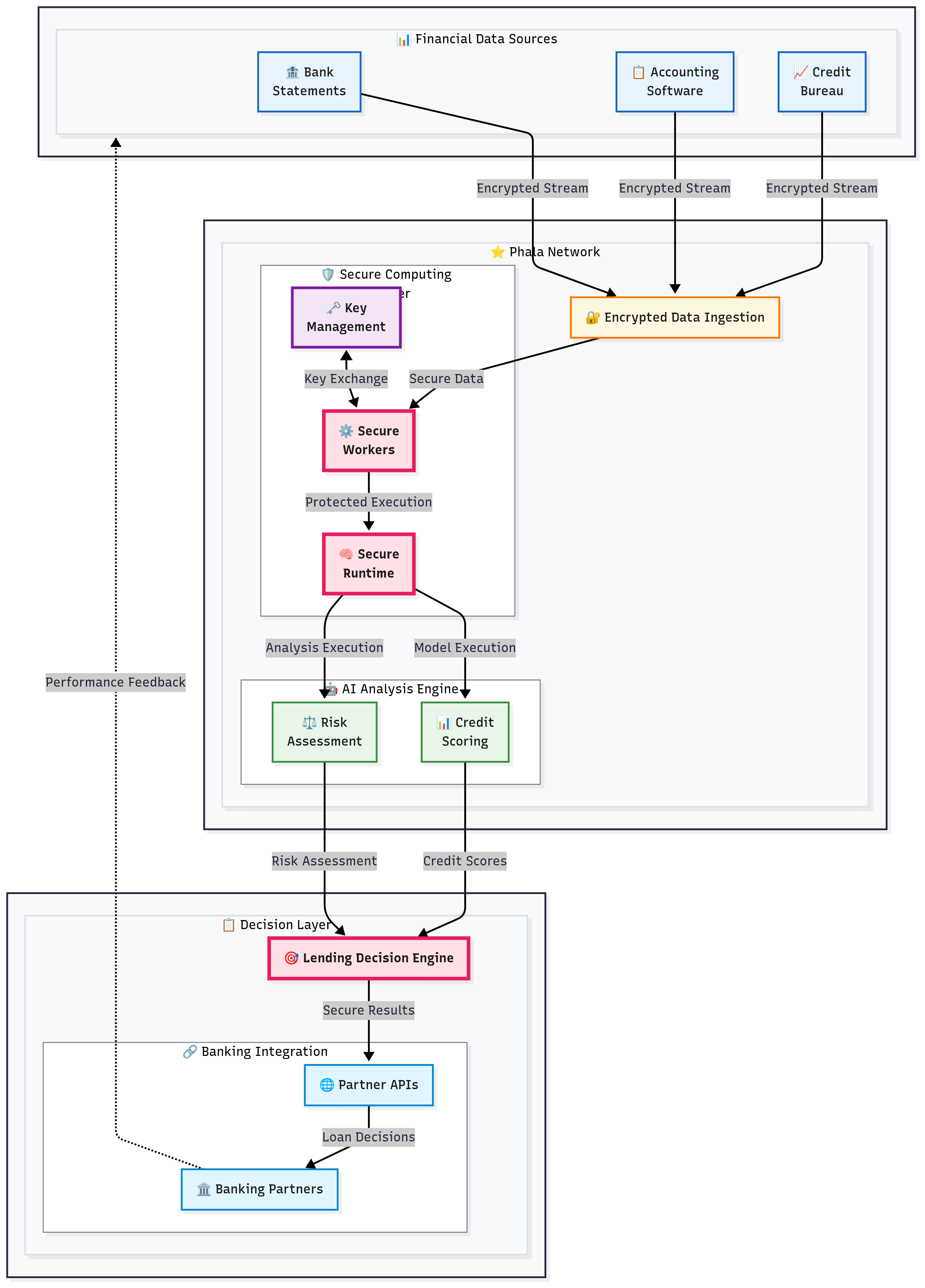
Results and Impact
The platform significantly reduced loan processing time while maintaining superior risk assessment accuracy compared to traditional methods. Privacy computing enabled SME lending transformation by providing mathematical guarantees that sensitive business data would remain protected, facilitating successful market expansion and substantial growth in loan origination volume while maintaining consistent privacy and compliance standards.
3.7 Financial Planning and Wealth Management SaaS
Best practice industry: Wealth Management + Financial Planning + AI + SaaS
Target applicable enterprises: Independent financial advisors, wealth management firms, broker-dealers, RIA (Registered Investment Advisor) platforms, financial planning software providers, robo-advisor platforms

Challenge
A financial technology company providing SaaS-based wealth management tools faced advisor resistance due to concerns about client data exposure and regulatory violations. The company required cloud scalability while maintaining advisor-client confidentiality and ensuring compliance across multiple regulatory frameworks without sacrificing sophisticated financial planning capabilities.
Solution Highlights
Confidential Portfolio Processing: Client financial data encrypted at the advisor level and processed within secure enclaves for portfolio optimization, risk analysis, and compliance reporting. Advanced financial planning algorithms operate within protected environments to safeguard proprietary intellectual property.
Practice Isolation Architecture: Real-time financial planning capabilities maintain complete separation between different advisor practices while enabling sophisticated analytics. Each advisor's client data remains isolated within dedicated secure environments.
Automated Compliance in TEEs: Regulatory reporting automated within secure environments, generating required documents without exposing underlying client data. Cross-jurisdictional compliance maintained through privacy-preserving regulatory frameworks.
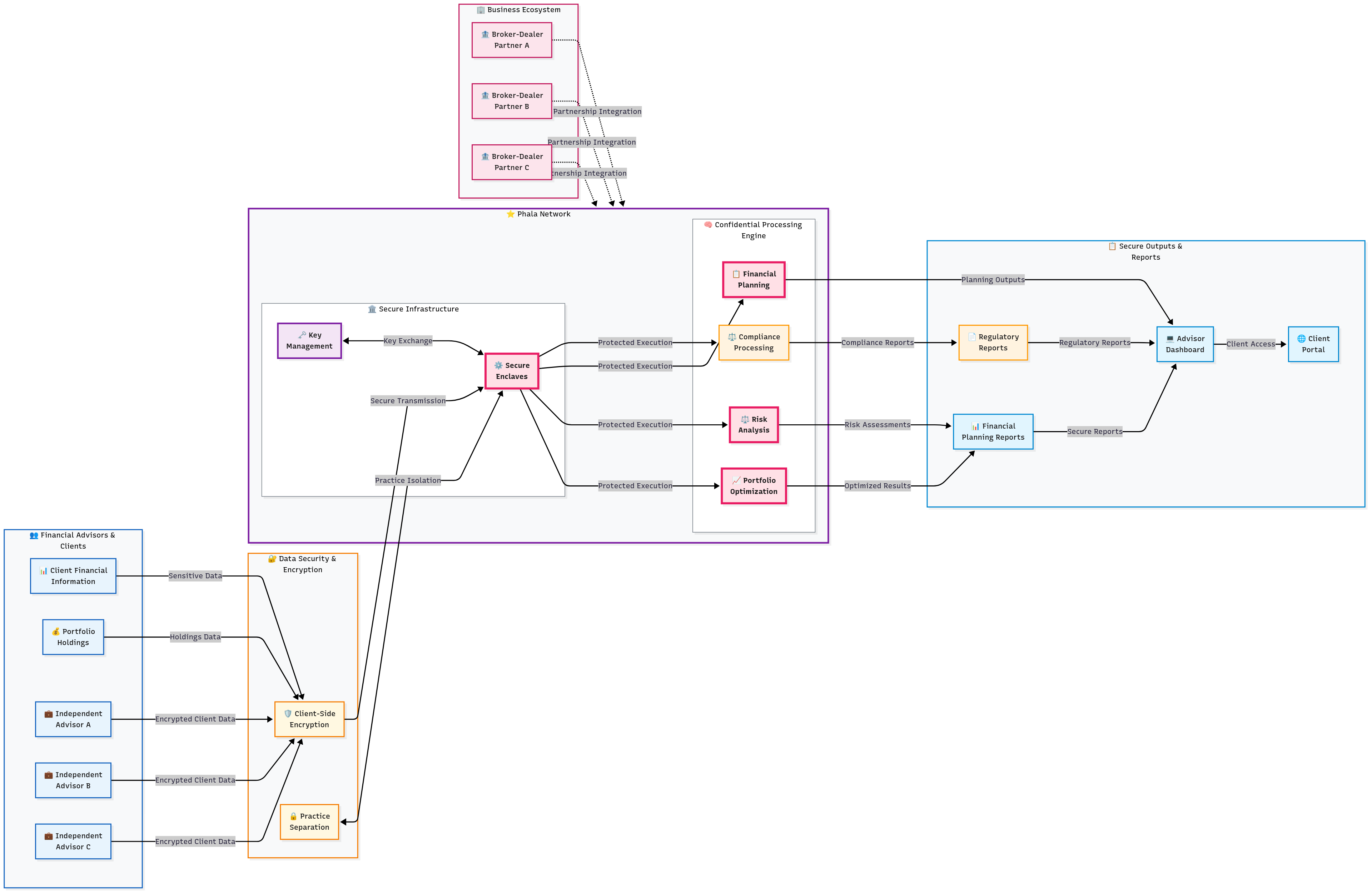
Results and Impact
The SaaS platform achieved substantially higher adoption rates among target advisors compared to traditional cloud-based competitors due to superior privacy protections. Privacy computing made wealth management SaaS viable by providing mathematical guarantees that sensitive client information would remain protected, enabling successful partnerships with major broker-dealers and resulting in significant growth in advisor user base while streamlining client onboarding processes.
3.8 Institutional Trading Platform
Best practice industry: Institutional Trading + AI + SaaS
Target applicable enterprises: Investment banks, hedge funds, asset management firms, proprietary trading firms, institutional brokerage services, algorithmic trading companies
Challenge
An institutional securities trading operation required real-time market analysis, algorithmic trading, and client order processing while protecting proprietary trading algorithms, client positions, and market intelligence from exposure to cloud providers and potential competitive intelligence gathering.
Solution Highlights
Confidential Algorithmic Trading: Proprietary trading algorithms execute within trusted execution environments that prevent reverse engineering or unauthorized access to trading logic. Market data processing and trade execution occur within hardware-protected boundaries.
Secure Client Order Processing: Client orders processed within secure enclaves that maintain complete confidentiality of trading positions and strategies. Order routing and execution algorithms remain protected while processing sensitive client information.
Privacy-Preserving Market Intelligence: Advanced market analysis and pattern recognition algorithms analyze market data and trading flows within secure environments, generating competitive intelligence while protecting analytical methods and client information.
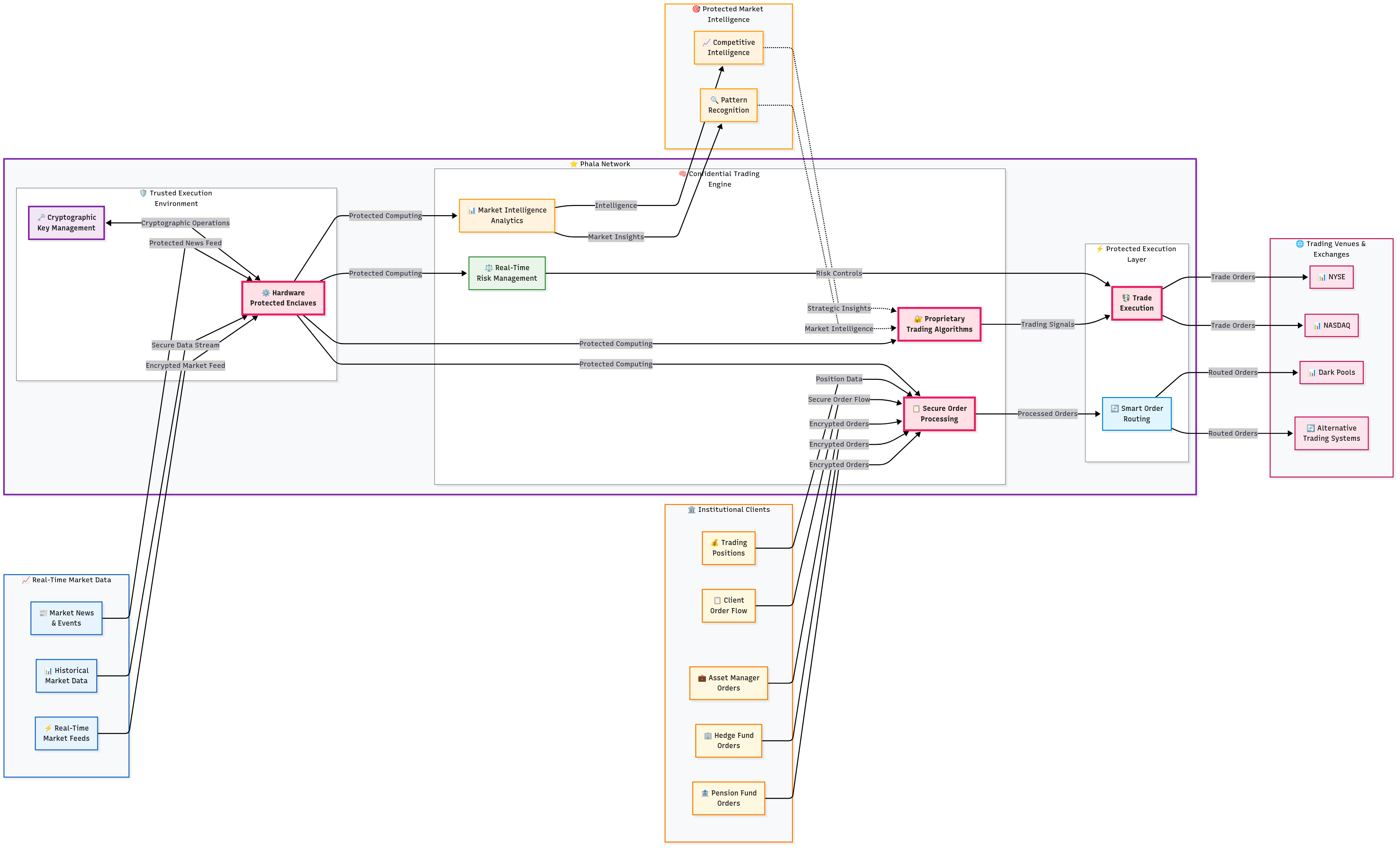
Results and Impact
The implementation enabled deployment of more sophisticated trading algorithms using cloud computing resources while maintaining superior protection of proprietary strategies. Trading performance improved through enhanced computational capabilities, while client confidence increased due to demonstrated commitment to position confidentiality. The platform processed over $50 billion in daily trading volume while maintaining mathematical guarantees of algorithm and data protection.
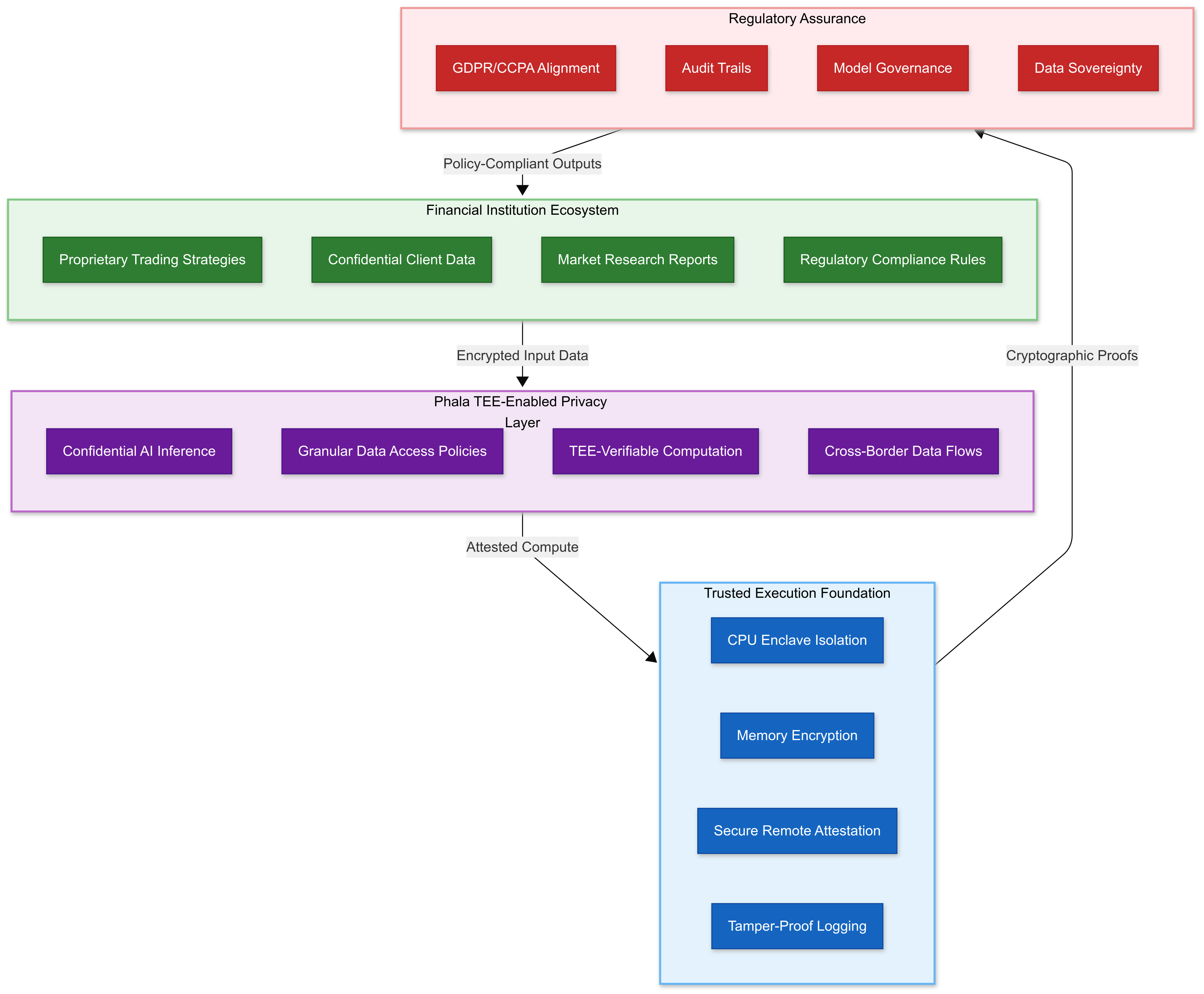
4. Technical Architecture: Financial Services Security Framework
Privacy computing fundamentally transforms financial operations by extending cryptographic protection to data during processing—addressing the critical vulnerability that traditional financial security models cannot solve.
Hardware-Based Financial Security Foundation:
Modern processors from Intel (SGX, TDX), AMD (SEV), and ARM (TrustZone) provide trusted execution environments (TEEs) specifically architected for financial services requirements. These processors deliver:
- Cryptographic guarantees independent of software security measures
- Remote attestation capabilities enabling verification of financial computing environment integrity
- Zero-trust architectures where security derives from verifiable technical properties rather than policy compliance
Financial Data Sovereignty Architecture:
Privacy computing enables financial institutions to maintain cryptographic control over sensitive data even when processing occurs on third-party cloud infrastructure. This capability directly addresses regulatory requirements for data sovereignty while enabling access to cloud-scale computing resources—transforming the traditional trade-off between compliance and operational efficiency into a competitive advantage.
Regulatory Compliance Through Technical Verification:
Privacy computing provides mathematical proof of compliance rather than policy-based assurances. Financial institutions can demonstrate rather than merely claim their privacy protection capabilities to regulators, auditors, and institutional clients through cryptographic verification systems.
5. Phala Financial Services Solution: Technical Innovation Meets Regulatory Excellence
5.1 Comprehensive Financial Security Architecture
Phala's enterprise-grade confidential computing platform addresses five critical security gaps that traditional financial infrastructure cannot solve:
1. End-to-End Financial Data Protection: Creates comprehensive encryption coverage from data ingestion through processing to reporting, ensuring sensitive financial information never exists in plaintext within computing environments.
2. Regulatory Compliance Automation: Implements automated compliance monitoring and reporting systems within trusted execution environments, providing real-time regulatory adherence verification while maintaining confidentiality of compliance strategies.
3. Cross-Border Financial Operations: Enables global financial services delivery while maintaining local data protection compliance through privacy computing technologies that satisfy regulatory requirements across multiple jurisdictions simultaneously.
4. AI Model and Algorithm Protection: Protects proprietary financial algorithms, trading strategies, and risk models through encrypted execution environments that prevent reverse engineering while enabling cloud deployment and third-party integration.
5. Multi-Party Financial Verification: Implements consortium-based verification networks for immutable security attestation, creating independently auditable proof of system integrity that satisfies the most stringent financial regulatory requirements.
5.2 Financial Services Integration Strategy
Seamless Banking Operations Integration:
- Developer Experience: Standard financial systems workflows remain unchanged, minimizing learning curves and migration costs
- Two-Phase Deployment: Configuration phase for secure infrastructure setup, production phase allowing only verified financial workloads
- Financial Industry Compatibility: Full integration with core banking systems, trading platforms, and regulatory reporting tools
Phased Implementation for Financial Institutions:
Phase 1: Assessment & Foundation (Months 1-3)
- Comprehensive financial data classification and regulatory threat modeling
- Privacy computing technology selection aligned with business objectives and regulatory requirements
- Pilot project identification focusing on high-value, low-risk applications
Phase 2: Pilot Implementation (Months 4-8)
- Limited scope deployment with performance baseline establishment for critical financial operations
- Financial security policy development and regulatory compliance testing
- Lessons learned documentation and optimization planning for scaled deployment
Phase 3: Scaled Deployment (Months 9-18)
- Extension across additional financial applications and business units
- Process automation and staff training programs tailored to financial services requirements
- Integration with enterprise financial IT service management systems
Phase 4: Advanced Financial Capabilities (Months 19-24)
- Federated learning and advanced financial analytics deployment
- Cross-institution verification framework implementation for industry collaboration
- Strategic planning for ecosystem-wide privacy computing adoption across financial partners
6. Strategic Implementation: Competitive Transformation in Financial Services
6.1 Business Value Across Financial Stakeholder Categories
Privacy computing fundamentally transforms how financial institutions approach regulatory compliance and competitive positioning by replacing policy-based assurances with mathematical guarantees:
Regulatory Compliance Leadership:
- Cryptographic verification satisfying Basel III/IV, GDPR, PCI DSS, and emerging AI governance requirements through technical demonstration
- Automated compliance reporting reducing regulatory audit costs while improving accuracy
- Cross-jurisdictional compliance enabling global operations without data sovereignty conflicts
Institutional Client Advantages:
- Mathematical privacy guarantees enabling services to privacy-conscious institutional clients
- Enhanced security posture addressing sophisticated threat landscapes in financial services
- Competitive differentiation through demonstrated rather than claimed security capabilities
Operational Excellence:
- Cloud-scale financial operations with on-premises security properties
- AI-driven financial services without compromising algorithm or data confidentiality
- Cross-border financial operations with local compliance through privacy computing
6.2 Financial Services Market Opportunities
Immediate Competitive Advantages:
The convergence of regulatory evolution, institutional client expectations, and competitive dynamics creates unprecedented opportunities for financial institutions implementing privacy computing capabilities:
Premium Institutional Market Access: High-value institutional clients requiring mathematical security guarantees, particularly in wealth management, institutional securities, and cross-border banking where privacy computing provides significant competitive differentiation.
Regulatory Leadership Positioning: Proactive compliance positioning as financial regulations continue evolving, with privacy computing establishing institutions as industry leaders in data protection standards.
Innovative Financial Services: Privacy computing enables new financial products and services previously impossible due to security constraints, creating first-mover advantages in emerging market segments.
Investment Prioritization for Financial Institutions:
- High-Impact Financial Applications: Focus on applications with clear business benefits and regulatory requirements such as cross-border payments, AI-driven risk assessment, and regulatory compliance
- Strategic Partnership Development: Leverage specialized expertise while building internal privacy computing capabilities
- Financial Industry Skills Development: Critical investment determining long-term success in privacy-enabled financial services
6.3 Call to Action: Seizing the Privacy Computing Advantage in Financial Services
Privacy computing represents both a fundamental market opportunity and competitive necessity for financial institutions. The evidence demonstrates that organizations successfully implementing privacy computing capabilities will capture high-value institutional markets and partnership opportunities that define tomorrow's financial services landscape.
Next Steps for Financial Services Leaders:
- Conduct Comprehensive Financial Privacy Assessment: Evaluate current privacy posture against regulatory requirements and institutional client expectations
- Engage Privacy Computing Technology Partners: Understand available options and develop preliminary implementation plans focused on specific financial services requirements
- Begin Financial Services Skills Development: Invest in internal capabilities for privacy computing implementation and operations tailored to banking and financial services
The Future of Financial Services:
The future of financial services will be defined by institutions that successfully balance innovation with privacy protection. Privacy computing technologies provide the foundation for this balance, enabling continued growth and innovation while meeting the highest standards of financial data protection.
Financial institutions that act decisively to implement privacy computing capabilities today will be best positioned for success in the evolving financial landscape—transforming regulatory compliance from operational burden into competitive advantage that opens new institutional markets, enables premium service offerings, and builds unassailable client trust through mathematical guarantees rather than policy promises.
About Phala Network: Leading provider of privacy computing solutions specifically designed for financial services, enabling institutions to harness AI and cloud computing power while maintaining complete data sovereignty and regulatory compliance. Contact our financial services solutions team to begin your privacy computing transformation and capture the competitive advantages that mathematical privacy protection delivers in modern banking and financial services.