Overview
Encifher has joined hands with Phala Network to leverage its TEE infrastructure in rolling out a high-performance TEE co-processor. This co-processor implements on-chain asynchronous concolic execution, enabling developers on existing blockchains (i.e., chains with users and liquidity) to build performant, composable, privacy-preserving applications.
Encifher is building its own TEE co-processor on top of DStack, which allows the deployment of custom programs as Docker containers within a Trusted Execution Environment (TEE) powered by Intel TDX.
Encifher’s TEE co-processor leverages the guarantees provided by Phala DStack in a way that allows users to verify every computation or request processed within the co-processor.
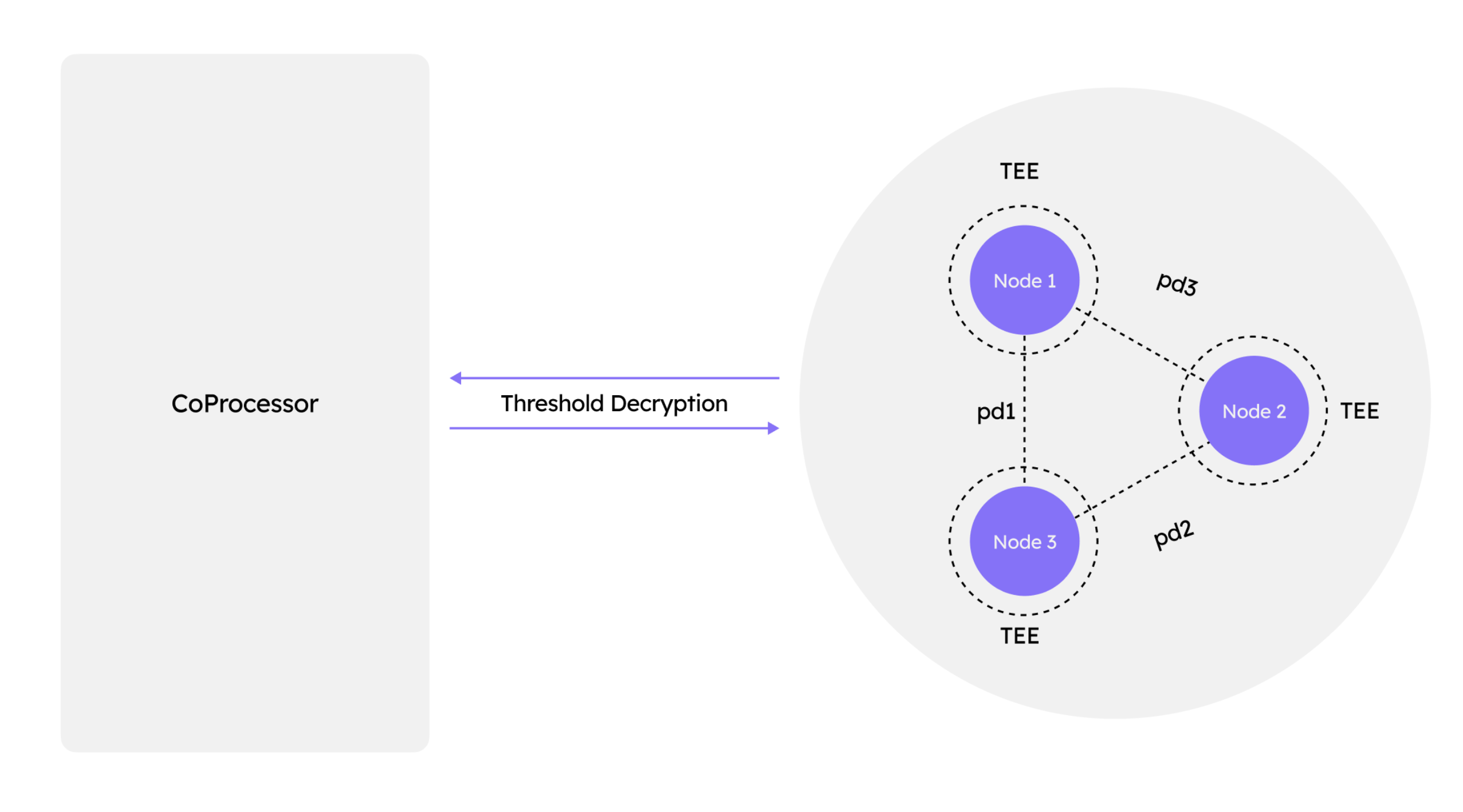
In addition, Encifher is developing a threshold committee network for the decryption of ciphertexts. Each node in this network will run within a TEE to mitigate the risk of MPC collusion attacks during threshold decryption.
Technical Integration
Encifher integrates the Phala DStack framework at two major components:
- On-chain computation request verification
- Threshold Committee nodes
On-chain Computation Request Verification
Encifher implements co-processor computation workflows such that every piece of off-chain computed data is verifiable against TEE-derived keys and attestation.
Computation is processed in batches, where each batch represents a complex computation expression with a defined set of inputs and outputs. Every batch is executed within the Trusted Execution Environment (TEE) and goes through three key stages:
- Pre-processing – Validation
- Processing – Computation
- Post-processing – Signing and Submission
Pre-processing
In the pre-processing stage, the processor validates proofs, input values, computation expressions, and the scope of computation requests based on the on-chain commitment relayed by the user. This stage also gathers all required input ciphertexts, ensuring that they are correct and intended for the computation.
Processing
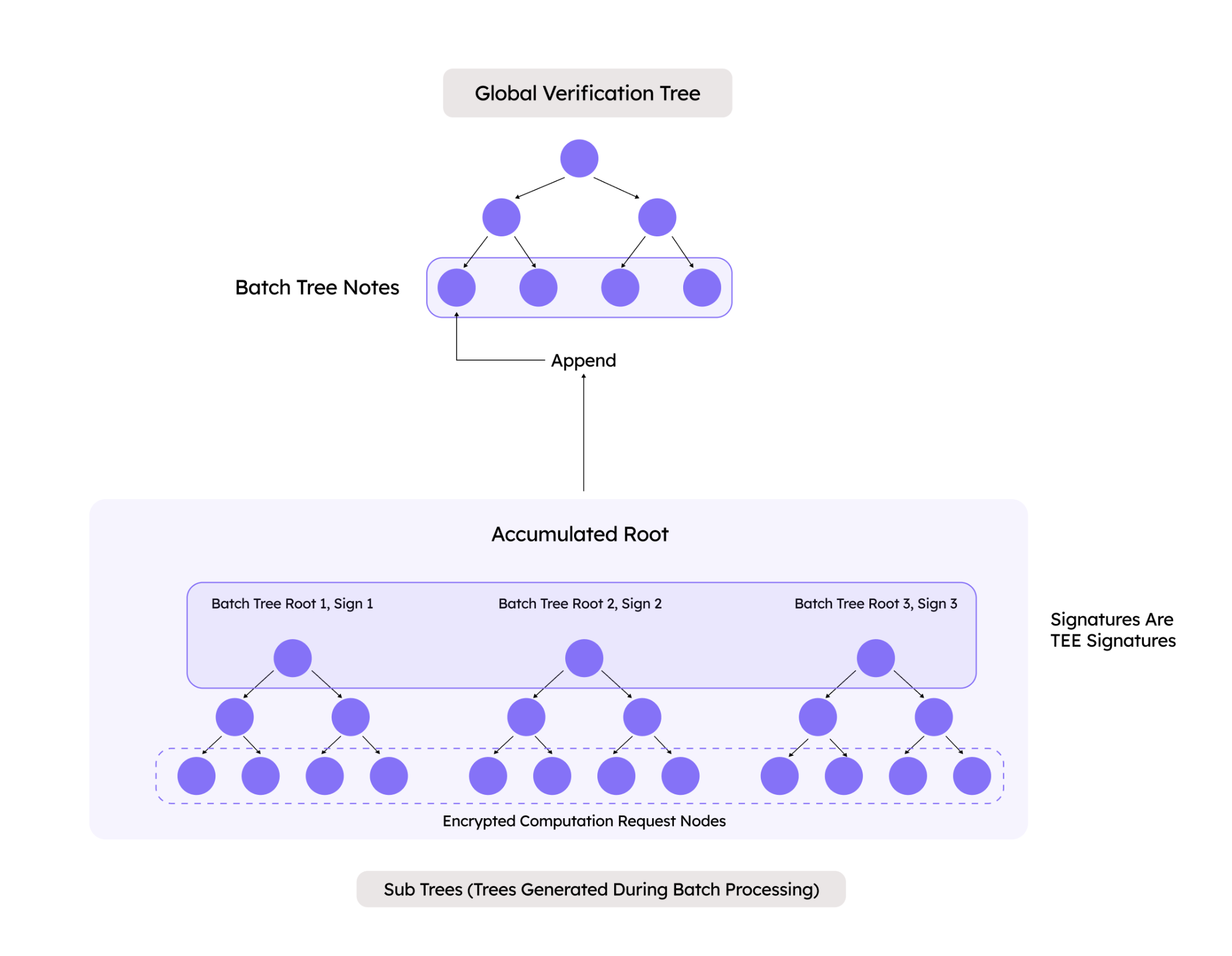
In the processing stage, the normalized expression is computed within the TEE. During this phase, the processor constructs a Batch Tree, which is temporarily stored in auxiliary storage. After a predefined retention period, the stored Batch Trees are retrieved and posted to an on-chain nested incremental Merkle tree, enabling asynchronous verification by users or other programs.
Post-processing
Once computation is complete and the Batch Trees are constructed, their roots are signed using a TEE-derived key (as per the DStack key derivation scheme). These signed roots are periodically submitted to the on-chain verification contracts. They are accepted only if the signatures are verified against the registered derived keys.
Threshold Committee Nodes
Encifher employs a threshold committee infrastructure that manages the global secret key in a sharded form and performs threshold decryption over ciphertexts upon user requests.
In threshold decryption schemes, the private decryption key is split among multiple parties (nodes), and only a subset (threshold t out of n) must collaborate to reconstruct or contribute to the decryption process. However, this setup introduces the risk of collusion attacks, where a malicious subset of t or more nodes collaborates to reconstruct the private key or decrypt sensitive data without authorization. Once the key is reconstructed or enough partial decryptions are aggregated, the adversary effectively breaks the confidentiality guarantees of the system. These attacks are particularly dangerous in long-lived systems where the secret must remain secure over time, or in settings without stringent accountability and isolation mechanisms among participants.
Role of TEE in Mitigating Collusion
Phala Dstack enabled TEEs offer a hardware-isolated execution context where code and data are protected from access or tampering, even by privileged software like the operating system. By integrating TEEs into the threshold decryption workflow, each node can perform its partial decryption inside a TEE, ensuring that the private key shard is never exposed to the host environment or external observers. Furthermore, TEEs can enforce strict policies—for instance, verifying that a decryption request is valid, rate-limited, and originates from an authenticated source—before computing a partial response. This minimizes the possibility of key shards being extracted or abused even in case of collusion among operators. In essence, TEEs shift the trust model from distributed parties to a combination of hardware-enforced isolation and cryptographic verification, significantly raising the bar for successful collusion.