
Introduction: The Age of User-Owned AI Agents
AI is no longer confined to data centers—it’s moving to the edge, into our homes, devices, and daily workflows. At Phala Network, we believe the next frontier for AI is trustless, user-owned agents that protect privacy and operate autonomously, wherever users need them.
However, deploying such powerful, context-aware agents outside traditional cloud environments raises critical questions:
- How do you guarantee user privacy and code integrity, especially for sensitive tasks?
- How do you deliver scalable, on-demand AI computation without a single point of trust?
- How do you empower IoT and personal AI agents to operate securely—across a wild variety of hardware and contexts?
Our answer: Trusted Execution Environments (TEE) at scale, delivered as decentralized infrastructure.
Why TEE is Essential for Personal Agents
Traditional cloud and edge architectures cannot fully protect user-owned agents:
- On-device compute is limited—today’s LLMs and advanced AI workloads often exceed what a phone or IoT gateway can handle.
- Server/cloud solutions require users to trust the operator, exposing sensitive personal context and assets.
- Web3 and blockchain integration increases the need for secure private key management and transaction signing.
TEE bridges the gap:
- Code and data are protected in isolated, attested hardware enclaves, even from the host operator.
- Secure plugins and hardware abstraction support integration with blockchains, messaging, and IoT hardware.
- Remote attestation guarantees that only trusted code is running and user data is never leaked, even during computation.
Case Study: Integrating AIMOverse Amico with Phala TEE Network
How the Integration Works
AiMoverse’s Amico SDK was designed for edge deployment, with a modular, layered architecture that makes it ideal for secure, hybrid execution. Here’s how we, as Phala engineers, supported and enabled this integration:
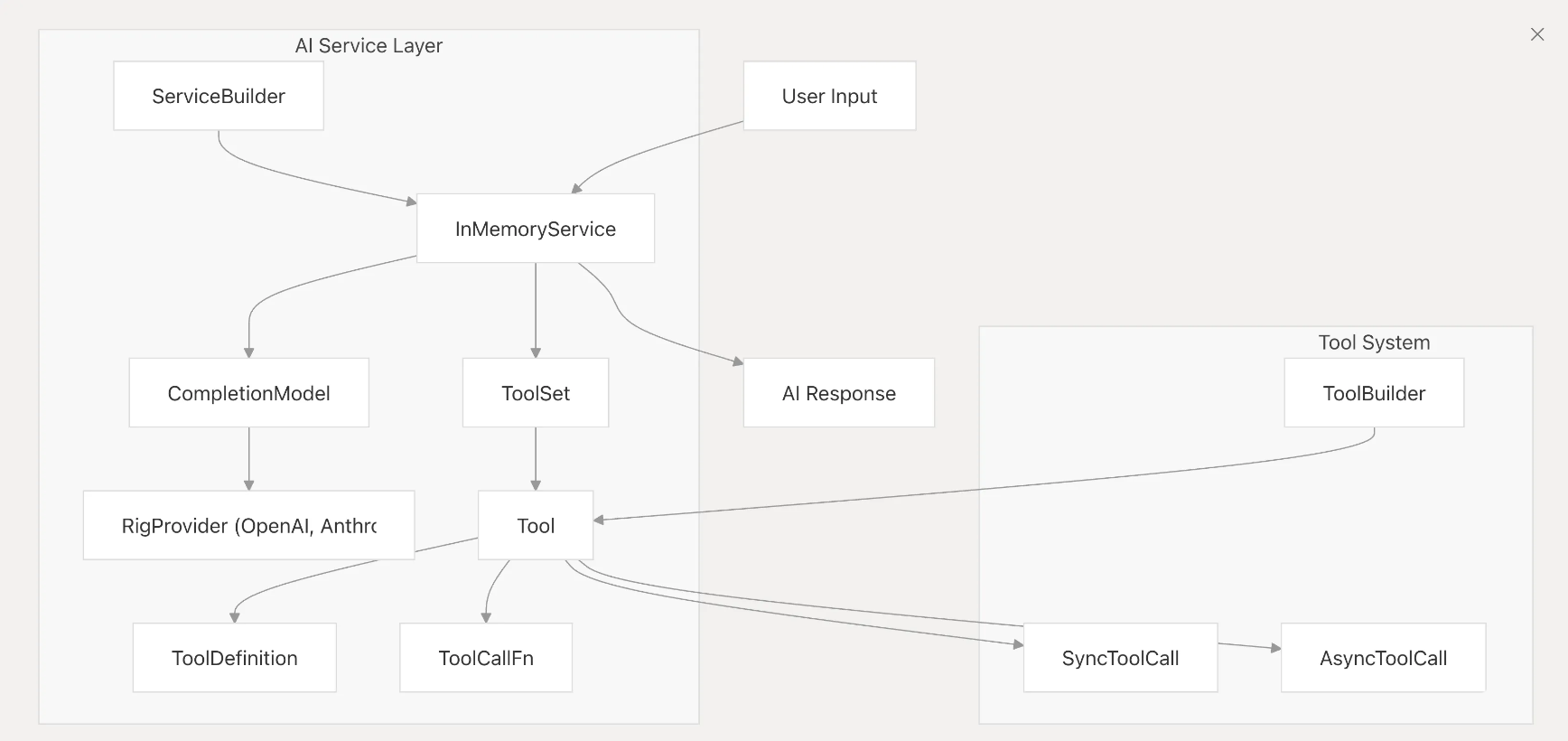
1. Modular Layer Placement
- Engine Layer & Sensitive Operations: Core agent logic (
amico-core), wallet/key management, and event processing are compiled and run inside Phala’s TEE-powered enclave. - Plugins & Web3: Decentralized plugins (
amico-mods) such as Ethereum/Solana adapters are vetted and loaded into the enclave after attestation, enabling secure Web3 operations. - Hardware Abstraction:
amico-halinterfaces with device sensors/effectors, with trusted I/O routed through encrypted, attested channels.
2. Secure Edge-to-Cloud Communication
- Agents can run partially on edge devices, offloading heavy computation or confidential tasks to Phala’s decentralized TEE cloud via secure, attested APIs.
- Result: Users get low-latency, privacy-preserving context processing locally, while accessing scalable, confidential AI workloads in the cloud.
3. Privacy by Design
- No personal data or private keys ever leave the TEE enclave unencrypted.
- Phala’s attestation service lets users verify both the code running in the enclave and the plugins loaded, closing off supply chain and runtime attacks.
- Data processed in the enclave is scrubbed from memory after use, with encrypted persistent storage where needed.
IoT and Personal AI Use Cases Enabled
Smart Home Agents:
- Home automation agents run locally, but delegate complex, privacy-sensitive inference to Phala TEE—no cloud provider or platform can access your data or device states.
Personal Crypto Wallets:
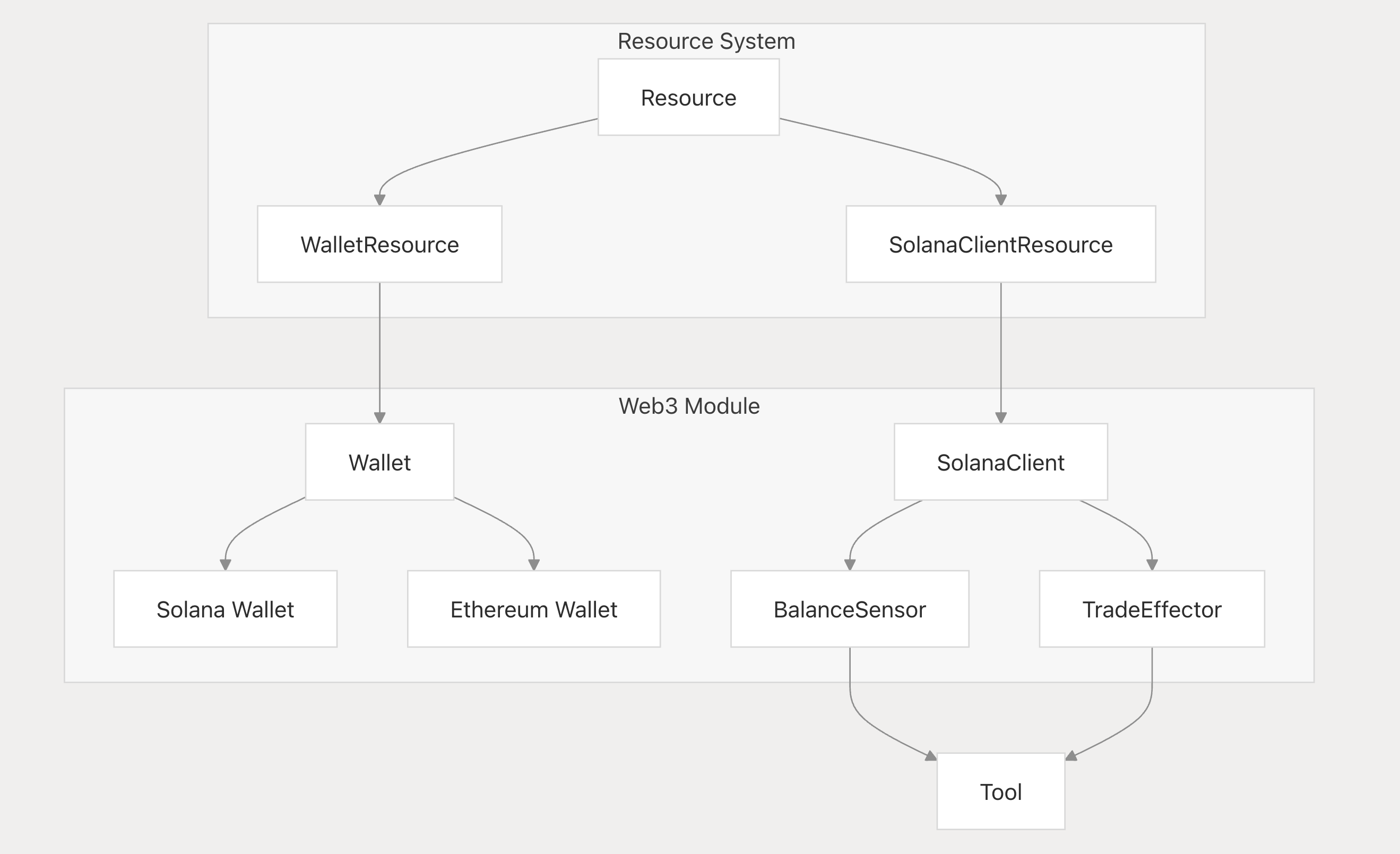
- Wallet logic and keys remain inside Phala enclaves, not on devices or central servers. Agents can sign transactions and interact with dApps securely, from any device.
Wearable Health & Mobile Assistants:
- Health sensor data is analyzed by user-owned agents, with advanced processing in Phala TEE. No cloud operator or third party ever sees sensitive medical info.
Decentralized Messaging & Collaboration:
- Agent-to-agent communication leverages encrypted, TEE-protected channels (e.g., Nostr), ensuring that only authorized code and users interact.
Engineering Insights: Lessons Learned
- Crate-level Modularity in the AIMOverse SDK was key—allowing selective, minimal code deployment in TEE, which is crucial given typical enclave memory limits.
- Async Runtime Adaptation: We worked with the AiMoverse team to optimize async runtimes (Tokio) within enclave constraints, maintaining responsive, event-driven agent logic.
- Automated Attestation & Deployment: Our deployment tooling automates enclave signing, plugin verification, and remote attestation, making integration robust for production-scale use.
Conclusion: Real-World, User-Owned AI at the Edge
Our collaboration with AIMOverse is a blueprint for building user-owned AI agents anywhere, with hardware-enforced privacy, verifiability, and decentralization. By combining modular agent frameworks with Phala’s TEE-powered decentralized cloud, developers and users can deploy trusted personal agents across IoT, web3, and edge computing—without compromise.
Ready to build or integrate your own TEE-protected agents?
- Phala Network — learn about our TEE infrastructure
- AIMOverse Amico SDK — open source agent framework
Let’s push the boundaries of decentralized, privacy-first AI—together.