
TL;DR
Trusted Execution Environments (TEEs), such as Intel SGX, are widely used to protect cryptographic keys and sensitive computations. However, TEEs face a critical challenge: keys stored in volatile enclave memory are lost during hardware failures or restarts. Traditional backups introduce centralization risks, while manual recovery processes are error-prone.
The Unruggable-AI repository addresses this by integrating TEEs, Fairblock’s MPC network, and a conditional private decryption protocol to ensure keys are securely backed up and recoverable without exposing them to centralized entities or single points of failure. This study explains how the system leverages Fairblock’s FairyRing MPC framework and its Private Decryption mechanism to achieve secure, automated key persistence and recovery.
Here are some useful resources to explore as you read:
- Start with the Code: Use Fairblock/Unruggable-AI and modify the CosmWasm contract for your needs.
- Test on Phala Cloud: Deploy via Phala Cloud to simulate failures and recoveries—use your $20 in free credits.
- Phala Cloud Docs: Explore the Phala Cloud documentation for a full overview and ask questions in the support group.
Let’s dive in!
1. Problem Statement
- Ephemeral Key Storage: Keys generated in TEEs are lost if the enclave crashes or the machine reboots.
- Centralized Backup Vulnerabilities: Storing keys in HSMs or cloud vaults reintroduces trust assumptions and attack surfaces.
- Manual Recovery Complexity: Human-driven key recovery is slow, risky, and impractical for mission-critical systems.
2. Introduction to MPC-TEE Hybrid Architecture
The system combines three core components:
- TEE (Intel TDX): Generates and encrypts keys within a secure enclave.
- Smart Contracts: Monitor TEE activity and trigger recovery workflows.
- Fairblock’s FairyRing MPC Network: Securely stores encrypted key shares and enables private decryption under predefined conditions.
| Component | Technology Stack | Security Guarantees |
| Smart Contract | CosmWasm Smart Contract (contract.rs) | On-chain enforcement of key recovery policies |
| MPC Network | FairyRing (TIBE, CKKS) | (t,n)-threshold secret sharing |
| Phala TEE | Phala Cloud + Dstack SDK | Remote attestation, memory encryption |
3. Workflow: Secure Storage and Recovery
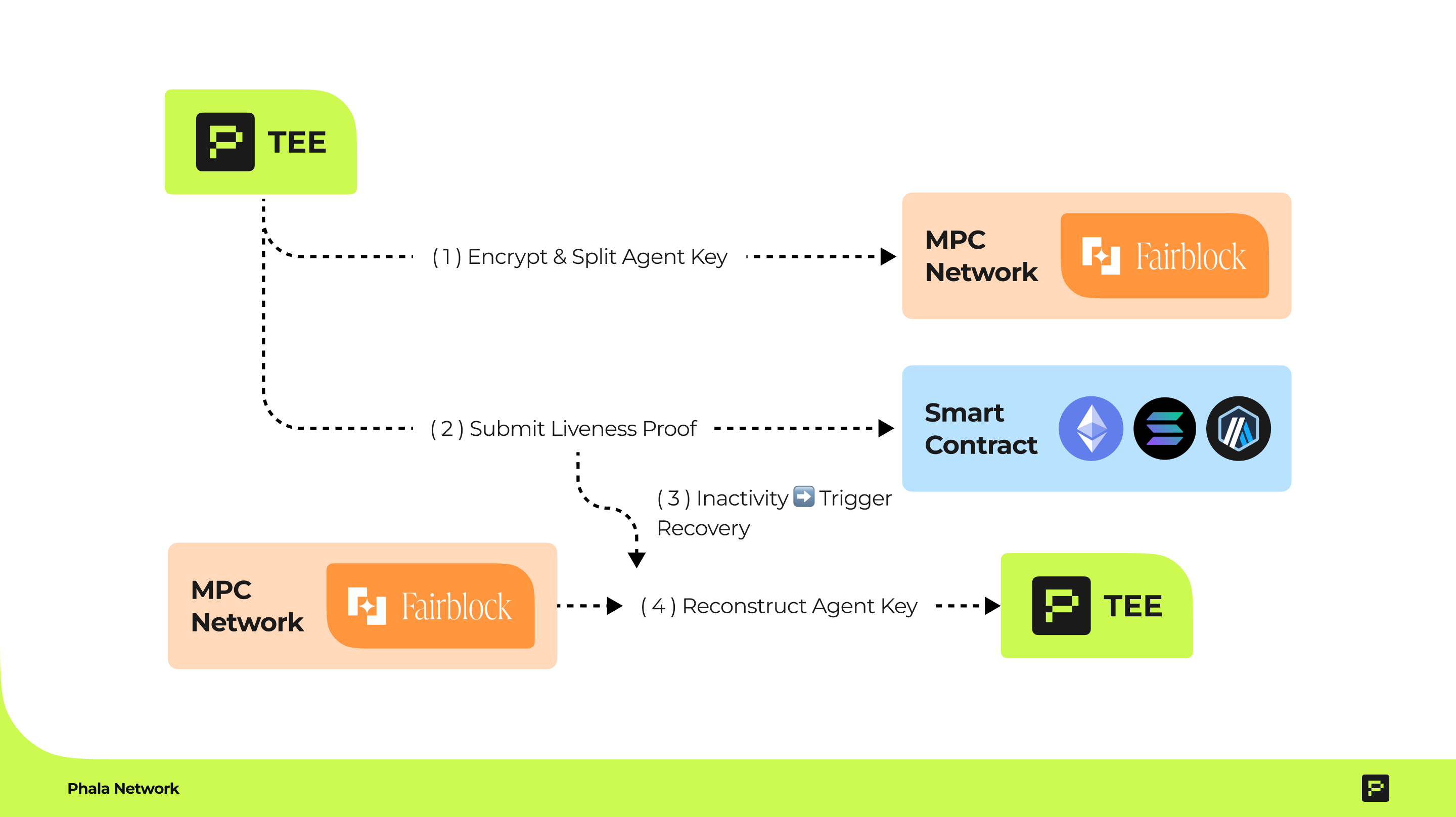
Phase 1: Key Generation and Encryption
- A private key (e.g., the Agent wallet) is generated inside the Phala TEE enclave.
- The key is encrypted using threshold encryption, splitting it into shares distributed across the FairyRing MPC network.
Check the source code in the Fairblock Github which are the components that running in Phala Cloud
Phase 2: Periodic Key Submission to Smart Contracts
- The TEE periodically submits the encrypted key to a smart contract (e.g., on a blockchain).
- Submissions act as a "liveness proof," signaling that the TEE is operational.
Phase 3: Failure Detection and Recovery Trigger
- If the TEE stops submitting encrypted keys (e.g., due to a crash), the smart contract detects inactivity after a predefined interval.
- The contract authorizes a pre-approved address (e.g., a governance module or backup administrator) to initiate a private decryption request.
Phase 4: Fairblock Private Decryption
- The authorized party submits a decryption request to the FairyRing MPC network.
- MPC nodes collaboratively decrypt the key shares without exposing individual shares or the full key to any participant.
- The reconstructed key is securely returned to a new TEE instance or a designated recovery endpoint.
4. Innovations and Benefits
1. TEE-First Security
- Keys are never stored in plaintext outside the TEE.
- All TEE operations produce verifiable attestations that prove computation integrity with the binding of the attestation to the validator's public key.
2. Integration with Smart Contracts
- Automated Workflows: Smart contracts act as decentralized oracles, monitoring TEE liveness and triggering recovery.
- Permissioned Recovery: Only entities with on-chain authorization (e.g., multisig governance) can initiate decryption.
3. Remove hardware lock-in
Live Migration: Sensitive data like keys are securely backed up and recoverable by external MPC, can be migrated to anther TEE hardware
4. Fairblock’s Private Decryption Protocol
Conditional Decryption: Decryption occurs only if predefined criteria are met (e.g., TEE inactivity)
5. Another Possibility of TEE x MPC: Building Accountable MPC
Fairblock’s research on Accountable MPC proposes a hybrid architecture where MPC nodes operate inside TEE-secured environments to enhance the security and accountability of the MPC network itself. This direction addresses a critical challenge in traditional MPC: collusion among nodes or malicious behavior that violates protocol rules.
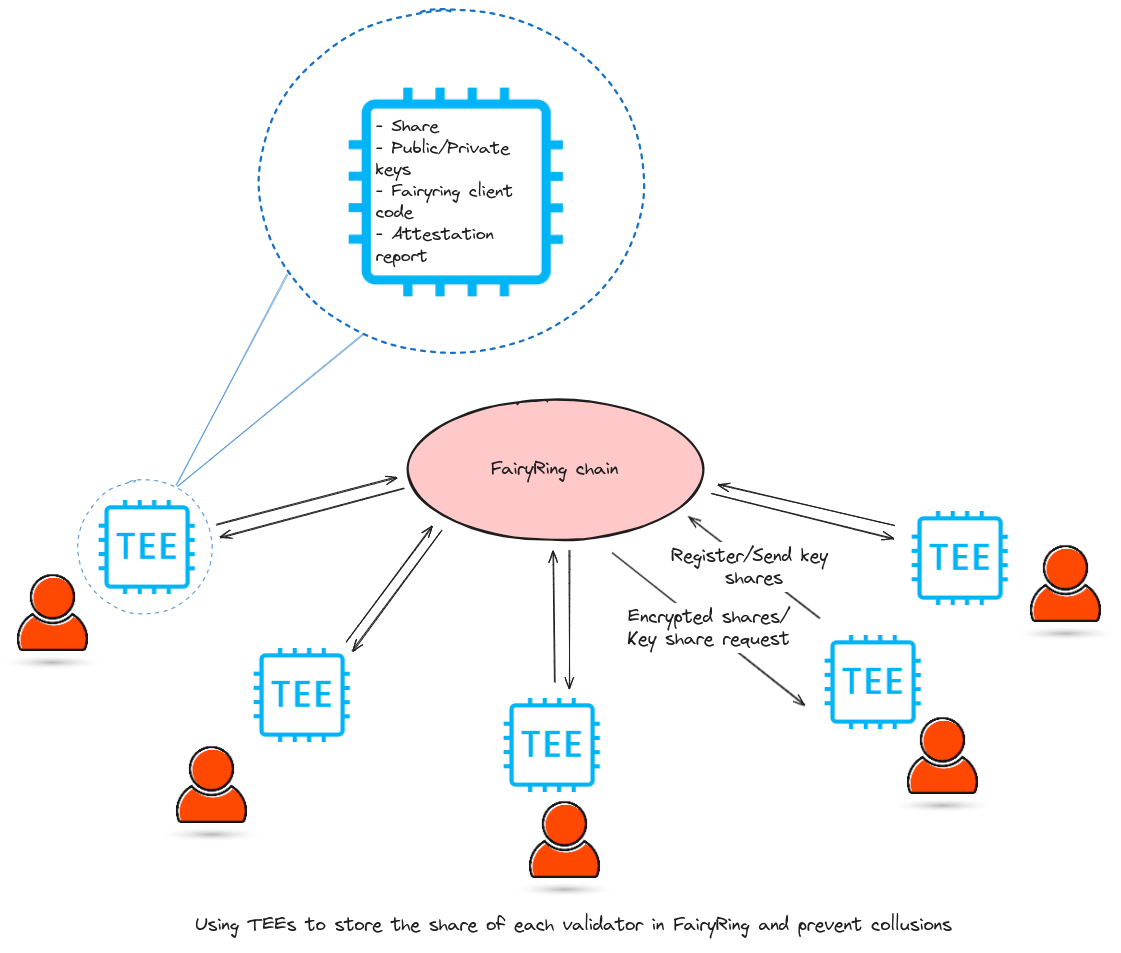
Source: https://hackmd.io/@Fairblock/rkSiU78TR
6. Conclusion: A Practical Model for Unruggable AI
The Phala-Fairblock collaboration shows that unruggable AI—systems that maintain privacy and persistence—is achievable today. By linking TEEs with MPC and blockchain coordination, this hybrid architecture solves the resilience challenge, supporting AI deployments in hostile, failure-prone settings.
Steps for Developers
- Start with the Code: Use Fairblock/Unruggable-AI and modify the CosmWasm contract for your needs.
- Test on Phala Cloud: Deploy via Phala Cloud to simulate failures and recoveries—use your $20 credit.
- Learn the System: Explore the Phala Cloud documentation for a full overview and ask questions in the support group.
This case study serves as both a technical example and a prompt for the AI community to build systems that last.