
TL;DR
The convergence of AI and blockchain presents significant opportunities but also introduces new challenges, particularly in terms of security and availability. Phala Network’s advancements in TEE technology directly address these challenges, providing the infrastructure needed to build secure, scalable, and reliable AI-powered blockchain applications. As the demand for decentralized AI grows, leveraging Phala's robust TEE infrastructure will be essential for the future of secure and trustworthy blockchain ecosystems.
Understanding the Challenges in Blockchain AI: The Problems Without Phala's TEE Solution
1. How a Decentralized AI Ecosystem Functions
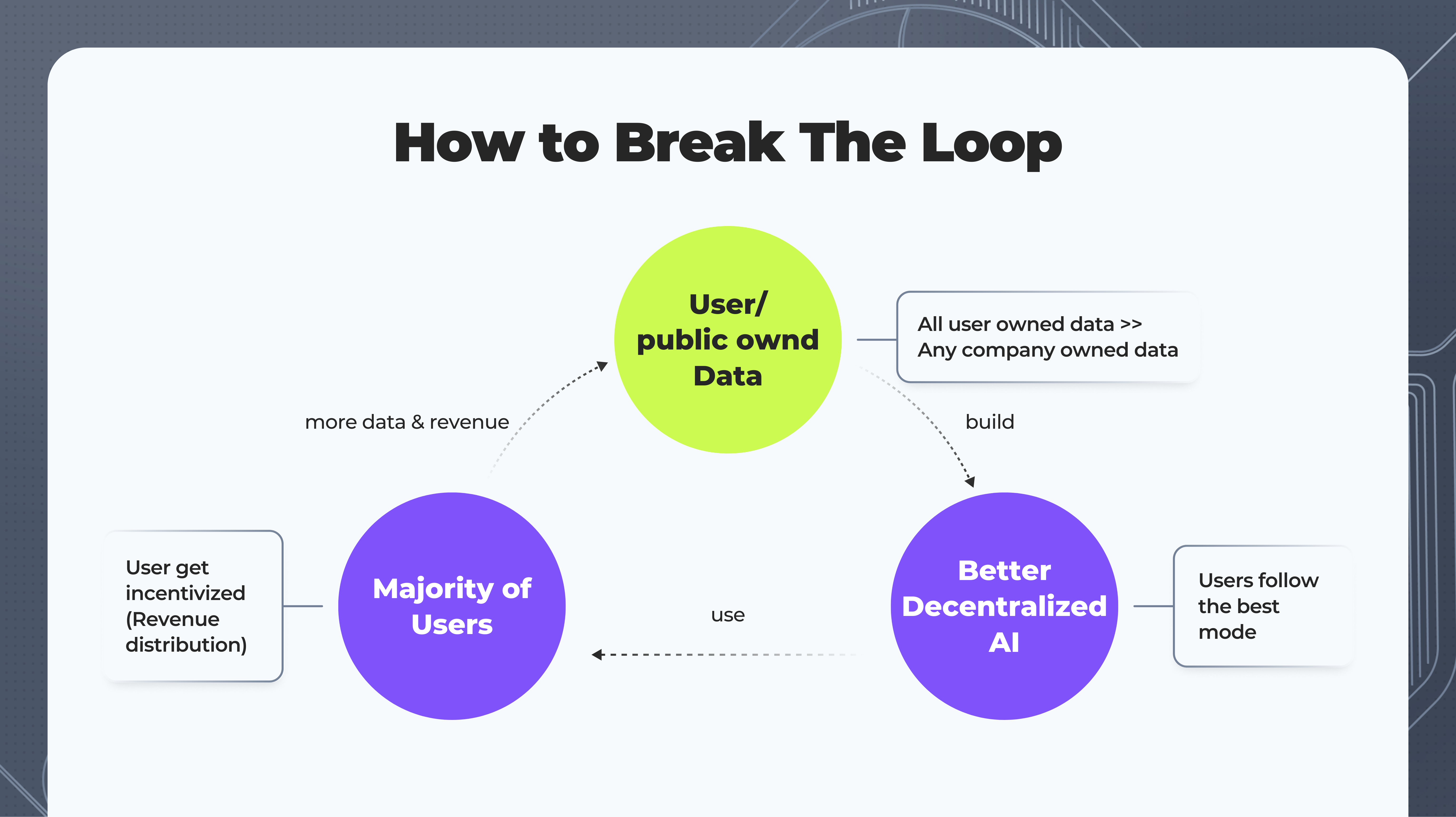
- The Challenge: In blockchain AI applications, multiple entities often contribute data to train and improve AI models. Coordinating these contributions securely and efficiently is a significant challenge, particularly when dealing with compute-intensive tasks. Centralized AI models exacerbate this issue by potentially creating unequal access, where only a select few have the best AI resources. This centralization can lead to scenarios where access to AI is restricted or banned by authorities, further limiting availability. Additionally, centralized AI systems can create a black-box attention economy, where users are subject to opaque algorithms that can manipulate or dominate information sources. A decentralized AGI ecosystem is essential to address these concerns, ensuring equal access to AI models, transparency, community-driven oversight, and resilience against bans or restrictions.
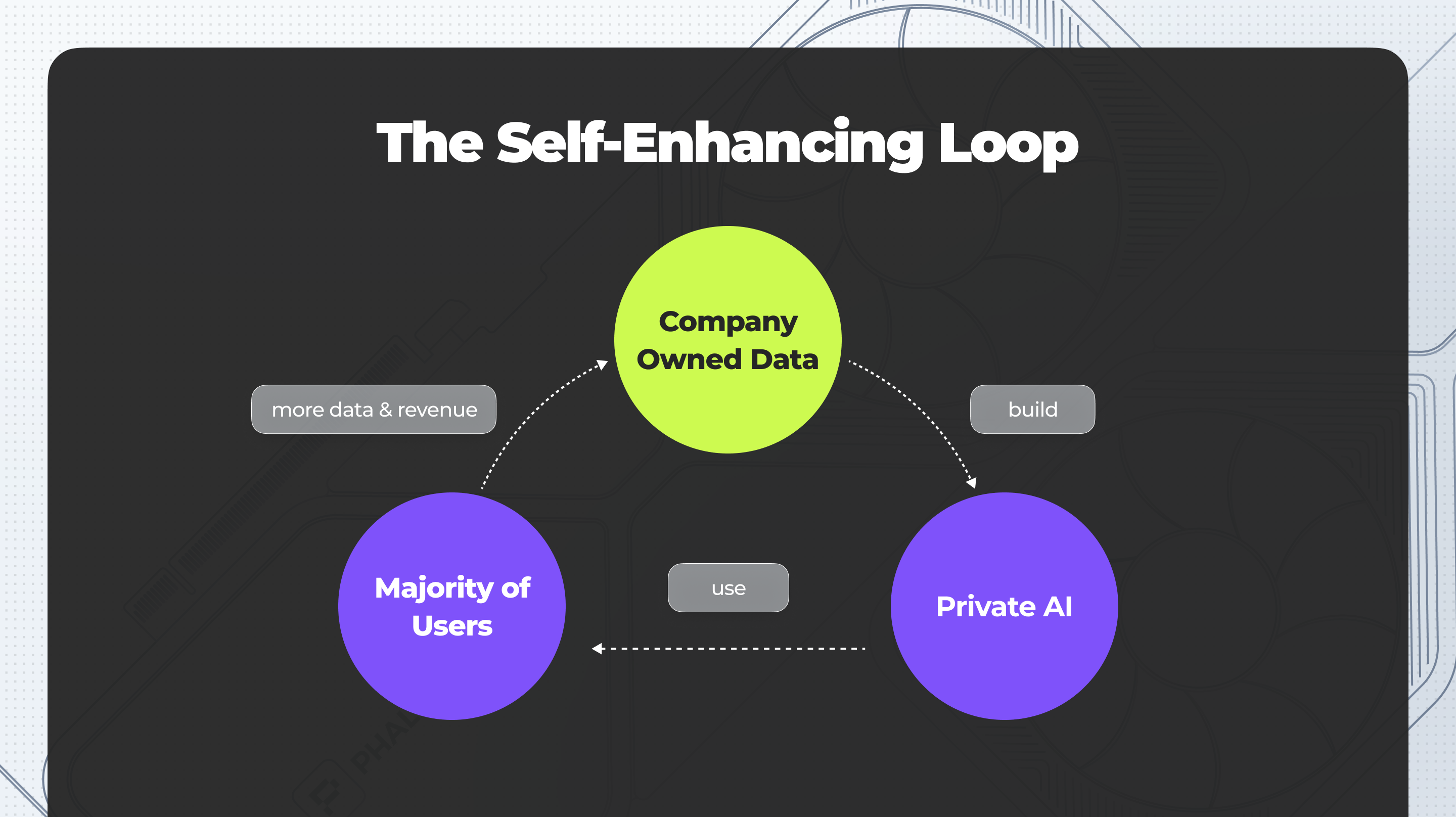
- Example: Imagine a decentralized AI platform where various stakeholders—such as data providers, individual contributors, and organizations—collaborate to develop and improve AI models. These models might be used for diverse purposes, such as language processing, autonomous decision-making, or even managing decentralized autonomous organizations (DAOs). To function effectively, this ecosystem needs to address several key challenges, which require a well-designed infrastructure.
- Tamper-Proof AI Models: Running AI models within Trusted Execution Environments (TEEs) ensures that they are tamper-proof, preventing unauthorized access or alterations. This is crucial for maintaining the integrity of the AI models and the data they process in a decentralized ecosystem.
- Unstoppable AI Operations: Redundancy is a key feature in decentralized systems. By implementing robust key management and regular key rotation, Phala ensures that even if some components fail or are compromised, the overall system continues to operate securely.
- DoS Resistance and Resource Management: In decentralized AI ecosystems, resisting Denial of Service (DoS) attacks is crucial. Phala’s TEE infrastructure includes resource accounting mechanisms that allocate and monitor resources effectively, reducing the risk of DoS attacks.
- Addressing TEE Vulnerabilities: The possibility of TEE vulnerabilities is acknowledged in the system design. Phala’s network admission control, including firmware upgrades, ensures that even if a vulnerability is detected, it can be swiftly addressed without compromising the entire ecosystem.
- EVM Integration and Onchain Attestation: Phala’s ecosystem supports Ethereum Virtual Machine (EVM) integration, enabling smart contract functionality within the TEE environment. Additionally, onchain attestation verification with tools like RiscZero ensures that only verified, secure TEEs are used, further enhancing the system’s trustworthiness.
2. AI Model Training Needs Program State Secrecy
- The Challenge: In blockchain-based AI systems, safeguarding the program state is essential. The program state encompasses critical information, such as training data, model parameters, and intermediate computational results. Without adequate protection, this sensitive information is at risk of being exposed, leading to severe privacy breaches and the potential leakage of proprietary AI model data. Ensuring the confidentiality of the program state is vital to maintaining the integrity and trustworthiness of AI systems within blockchain networks.
- To address these risks, it is critical to consider a defense-in-depth strategy, as outlined in the OpenAI article. This strategy involves multiple layers of security controls, making it difficult for attackers to exploit vulnerabilities even if they gain access to one layer. In the context of AI and blockchain, implementing TEEs as one of these layers can significantly enhance the security of AI models by ensuring that the computations are performed in a secure environment, thus reducing the risk of data leakage or tampering.
- Example: Bargaining in AI Model Secrecy
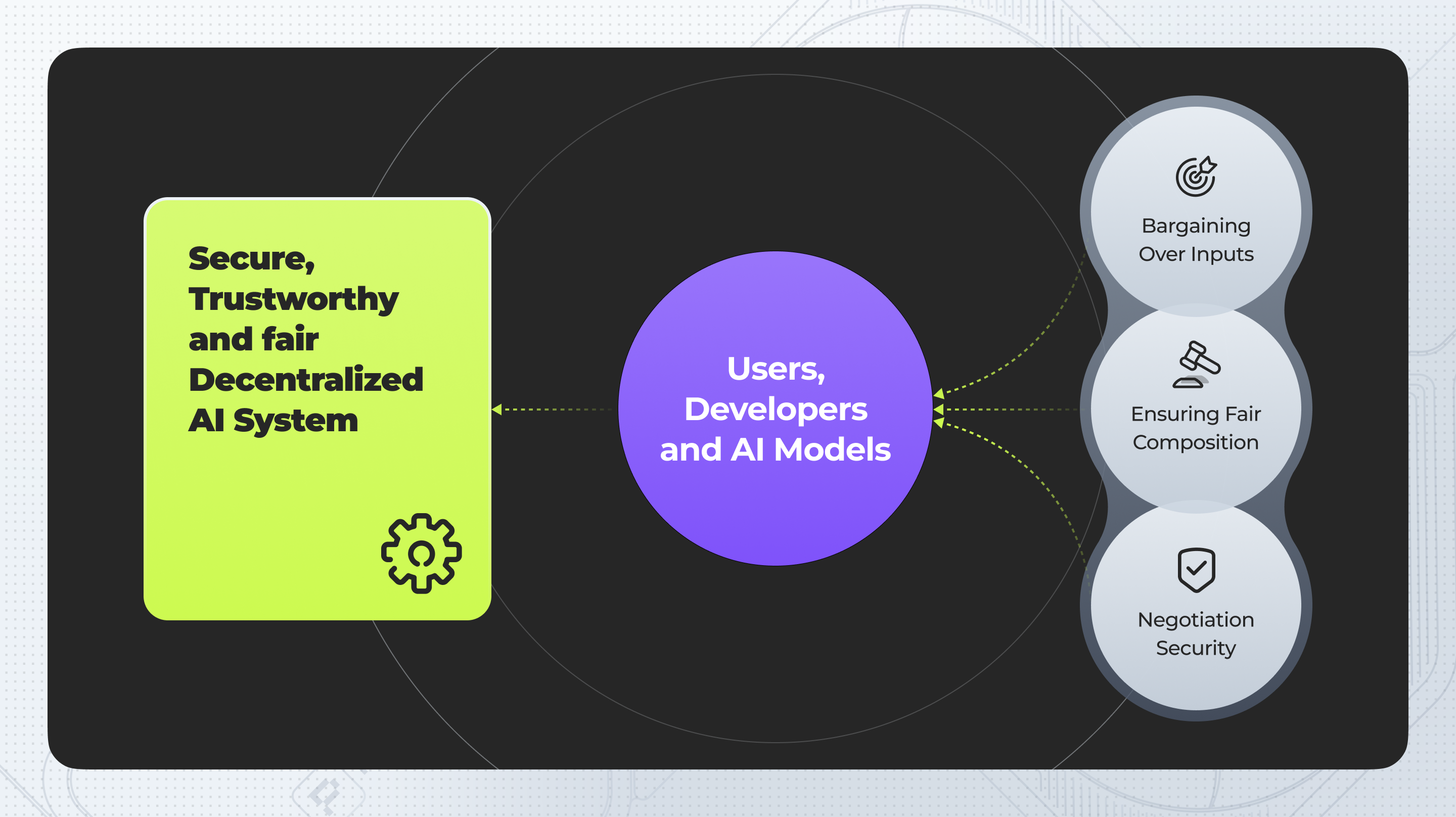
In decentralized AI systems, entities like users, developers, and AI models often need to collaborate while keeping their data secure. This process is akin to bargaining, where each party has private data and objectives.
- Bargaining Over Inputs: AI models negotiate which datasets to use for collective training. Each party aims to protect its data while benefiting from others, using TEE to maintain privacy during negotiations.
- Ensuring Fair Composition: One AI model may lead in integrating inputs, similar to how auctions need an operator. Fairness is ensured by processing within a secure TEE, preventing data manipulation.
- Negotiation Security: AI models negotiate access to specific data points or resources, ensuring their data remains secure. For example, an AI model might share top-performing data but require proof that other models' data won't conflict.
This approach ensures that AI-driven decisions in decentralized ecosystems are secure, trustworthy, and fair, much like how auctions and bargaining bots operate by protecting private data.
3. Addressing TEE Vulnerabilities and Reliability: AI Models Must Go Beyond Single-TEE Computations
- The Challenge: While Trusted Execution Environments (TEEs) are designed to protect sensitive computations, they are not immune to vulnerabilities or availability issues. A compromised or unavailable TEE node can disrupt AI model operations, leading to downtime or, worse, the exposure of sensitive data.
Building on the defense-in-depth strategy mentioned in the OpenAI article, it is essential to have multiple TEEs working in tandem. This not only mitigates the risk of a single point of failure but also ensures that if one TEE is compromised, others can continue to operate securely. This layered defense mechanism strengthens the overall security posture of decentralized AI systems, ensuring resilience and continuity even in the face of targeted attacks.
- Example: Imagine an AI model deployed in a decentralized autonomous organization (DAO) that makes real-time governance decisions based on member votes. If the TEE node running this model goes down, the DAO’s decision-making process could be halted, affecting its ability to function effectively. In a more severe scenario, if the TEE is compromised, attackers could manipulate the model to skew governance outcomes.
Closing Thoughts
As the convergence of AI and blockchain continues to present both opportunities and challenges, it's clear that robust infrastructure is essential for ensuring security, scalability, and trustworthiness. Phala Network’s advancements in TEE technology offer a compelling solution to these challenges, providing the necessary tools to build secure decentralized AI ecosystems. By addressing core issues such as program state secrecy and TEE vulnerabilities, Phala is setting the stage for the future of AI-driven blockchain applications, ensuring they remain resilient, reliable, and secure.