How Developers Can Build Secure Web3 Backends with TEEs on Phala Cloud
2025-03-25
Introduction
The Bybit hack laid bare a harsh truth about Web2 backends: a single compromised server can lead to millions in losses. This wasn’t a fluke—it’s a glaring symptom of centralized vulnerabilities. Web3 promises decentralization, but without secure computation, it’s doomed to repeat Web2’s mistakes.
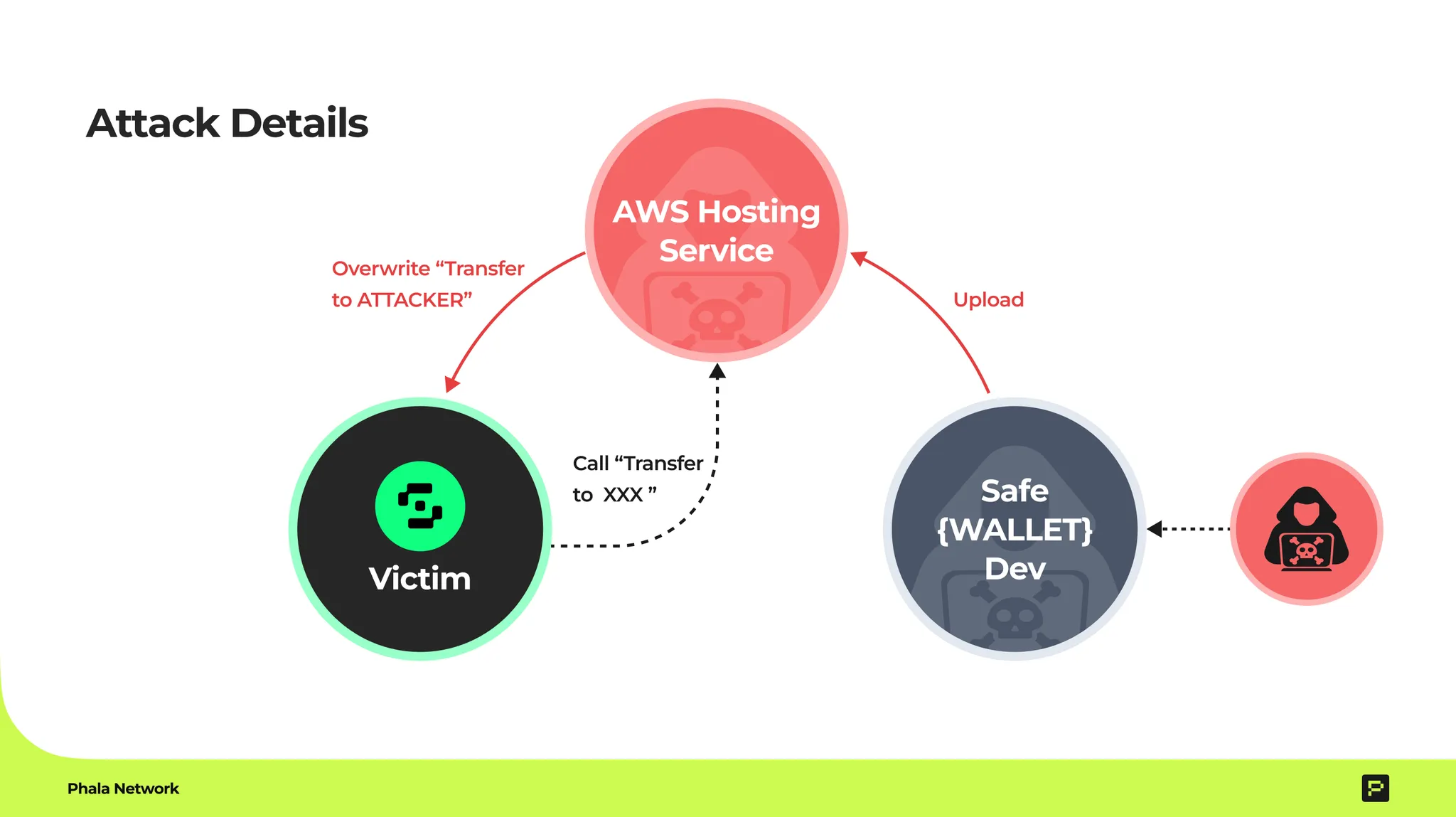
A developer working on Safe{Wallet} got hacked. Attackers secretly added malicious code to the wallet service (JaveScript hosted in AWS). Attackers stole funds because no one double-checked the actual transaction details—like verifying the address on that envelope.
Enter Trusted Execution Environments (TEEs)—hardware-based secure zones that keep data encrypted even during processing. Paired with Phala Cloud, TEEs empower developers to build Web3 backends where data confidentiality and code integrity are non-negotiable.
In this guide, we’ll break down how TEEs solve Web2’s security woes, how Phala Cloud delivers a trustless infrastructure, and—most importantly—how you can leverage it to build secure Web3 applications.
Let’s dive in.
Web2’s Security Pitfalls: A Developer’s Nightmare
Web2 backends are fragile by design. Here’s why they fail developers:
- Censorship Risks: Centralized servers can be shut down or manipulated by authorities or hackers, leaving your app at their mercy.
- Opaque Execution: You trust providers to run your code correctly, but insiders or compromised software (like the Bybit attacker’s sneaky JavaScript tweak on AWS) can sabotage it.
- Data Exposure: Encryption stops at rest and in transit—data gets decrypted for processing, opening attack windows.
By leveraging TEE, Web3 backends demand a paradigm where data remains encrypted even during computation and code execution is independently verifiable. See it in action here.
TEEs 101: The Hardware Foundation for Trustless Computing
TEEs (think Intel TDX or AMD SEV) are secure enclaves inside CPUs. Imagine a vault where your code and data live, untouchable by the outside world—even the OS or cloud provider. Here’s what they bring to the table:
- Confidential Computing: Data stays encrypted inside the TEE, safe from prying eyes.
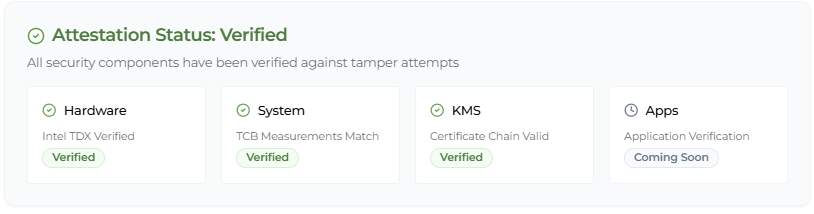
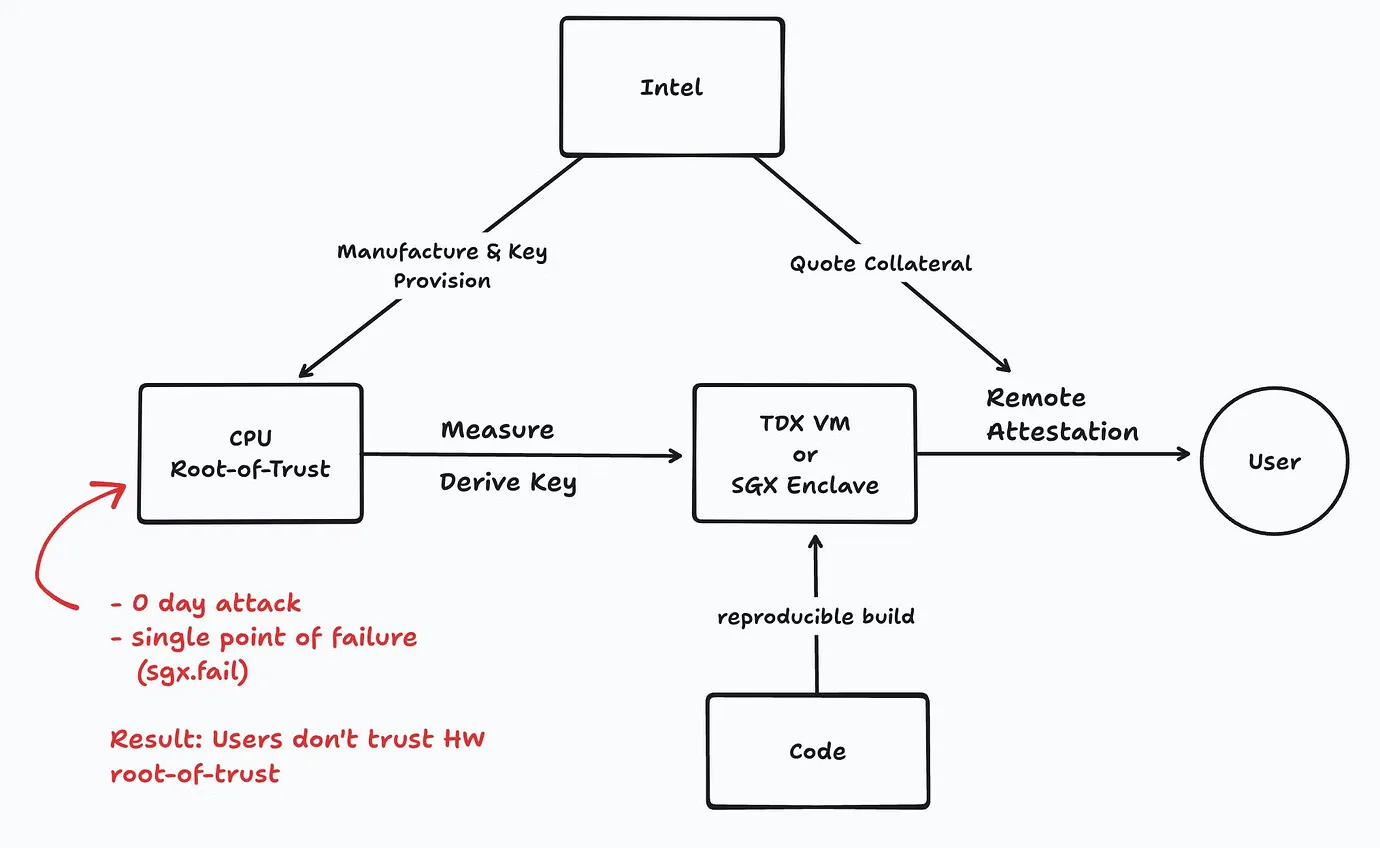
- Remote Attestation (RA): A cryptographic “certificate” proves your code runs in a legit TEE, signed by the CPU maker (e.g., Intel).
- Tamper-Proof Execution: Hackers can’t mess with your logic, even on a compromised machine.
Unlike Web2’s half-baked security, TEEs offer end-to-end encryption and verifiable execution—perfect for Web3’s trustless ethos.
Phala Cloud: Your TEE-Powered Web3 Backend Toolkit
Phala Cloud takes TEEs and wraps them in a decentralized, developer-friendly package. It’s built to deliver secure, verifiable backends without the centralized baggage. Here’s how it works:
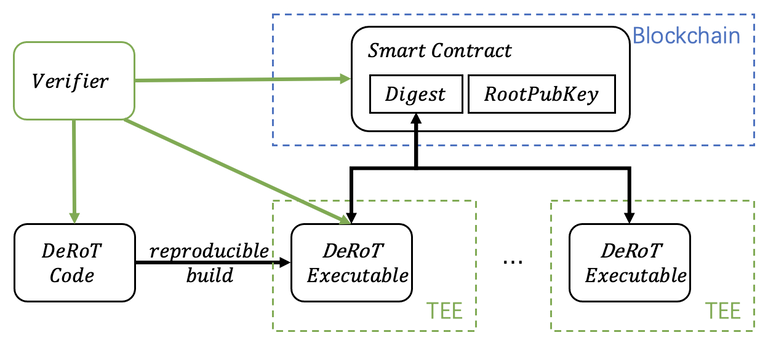
Key Architectural Components
- TEE Worker Nodes
- Run by independent providers on TEE-capable hardware (e.g., Intel TDX)..
- Each node spits out a Remote Attestation report, verifiable via on-chain smart contracts or tools like dcap-qvl.
- You can check what code runs where before trusting it.
- Trustless Coordination
- Smart contracts manage base image registration, KMS root key verification, user don't need to trust the Cloud provider.
- Even the application code updates can be managed by on-chain governance: new deployments must match hashes approved by governance, preventing unauthorized changes.
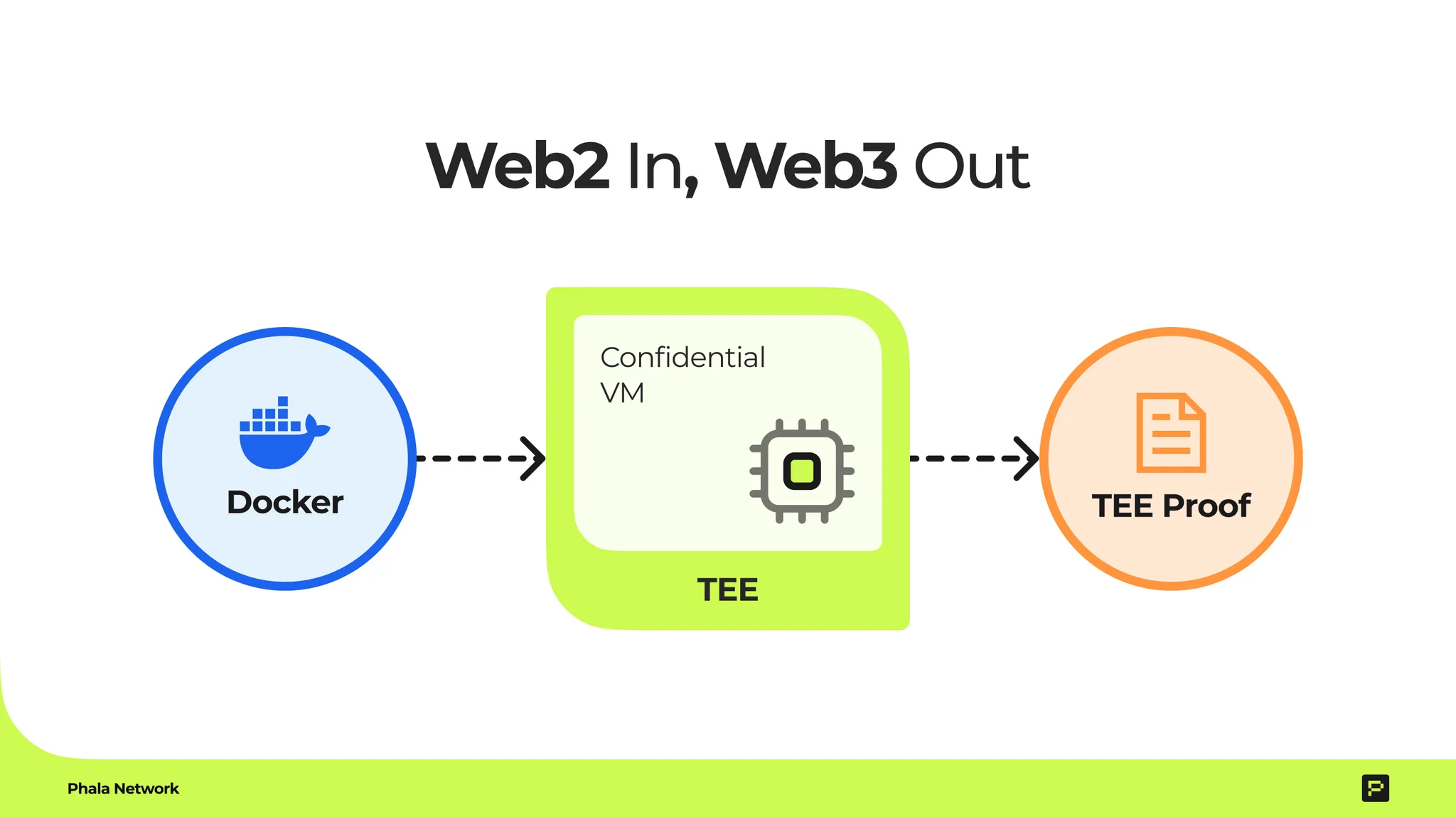
- Phala Cloud built on dstack SDK fundamentals: Modern TEE Abstraction Layer
- Built on dstack, this lets you drop any Docker program into a TEE with minimal fuss, keeping it verifiable.
Building on Phala Cloud: 3 Core Principles
Ready to code? Here’s how Phala Cloud ensures your Web3 backend is secure by design:
Data Confidentiality by Default
- Encrypted Communication: End-to-end encryption between users and backend inside TEE, the root-of-trust comes from RA report.
- In-Enclave Processing: Sensitive operations (e.g., key management, financial transactions) occur entirely inside the TEE.
2. Remote Attestation: Proving Trustworthiness
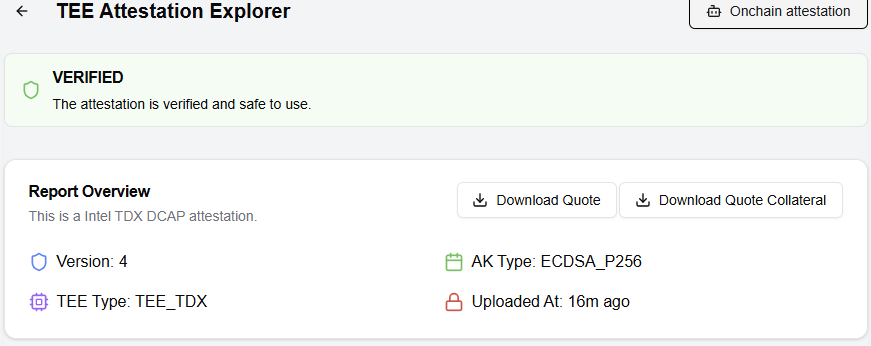
- RA Workflow:
- A user requests a RA report from a TEE worker.
- The report includes a hash of the enclave’s code and a digital signature from the CPU manufacturer (e.g., Intel).
- The user verifies the report against a trusted registry (e.g., Phala’s on-chain registry).
- Why This Matters: RA replaces blind trust with cryptographic proof that code is unmodified and runs in a genuine TEE.
Real-World Wins: What You Can Build
Phala Cloud isn’t just theory—it solves problems developers face daily. Here are three killer use cases:
1. Secure Private Key Management
- Problem: Centralized exchanges get hacked, losing user funds.
- Solution: Generate and store keys in TEEs, sign transactions in-enclave. Check the Create Crypto Wallet guide for a step-by-step.
- Win: RA proves keys never leave the TEE.
2. Confidential DeFi Transactions
- Problem: Front-running and MEV plague transparent blockchains.
- Solution: Encrypt and match orders in TEEs, hiding intent until execution. See how Flashbots uses TEEs for Ethereum blocks building here.
- Win: Fair trades, guaranteed by RA.
3. Privacy-First Identity Verification
- Problem: KYC exposes user data to third parties.
- Solution: Verify data in TEEs without sharing raw info—even with app devs.
- Win: Privacy meets compliance.
Phala Cloud vs. Traditional Clouds: A No-Brainer
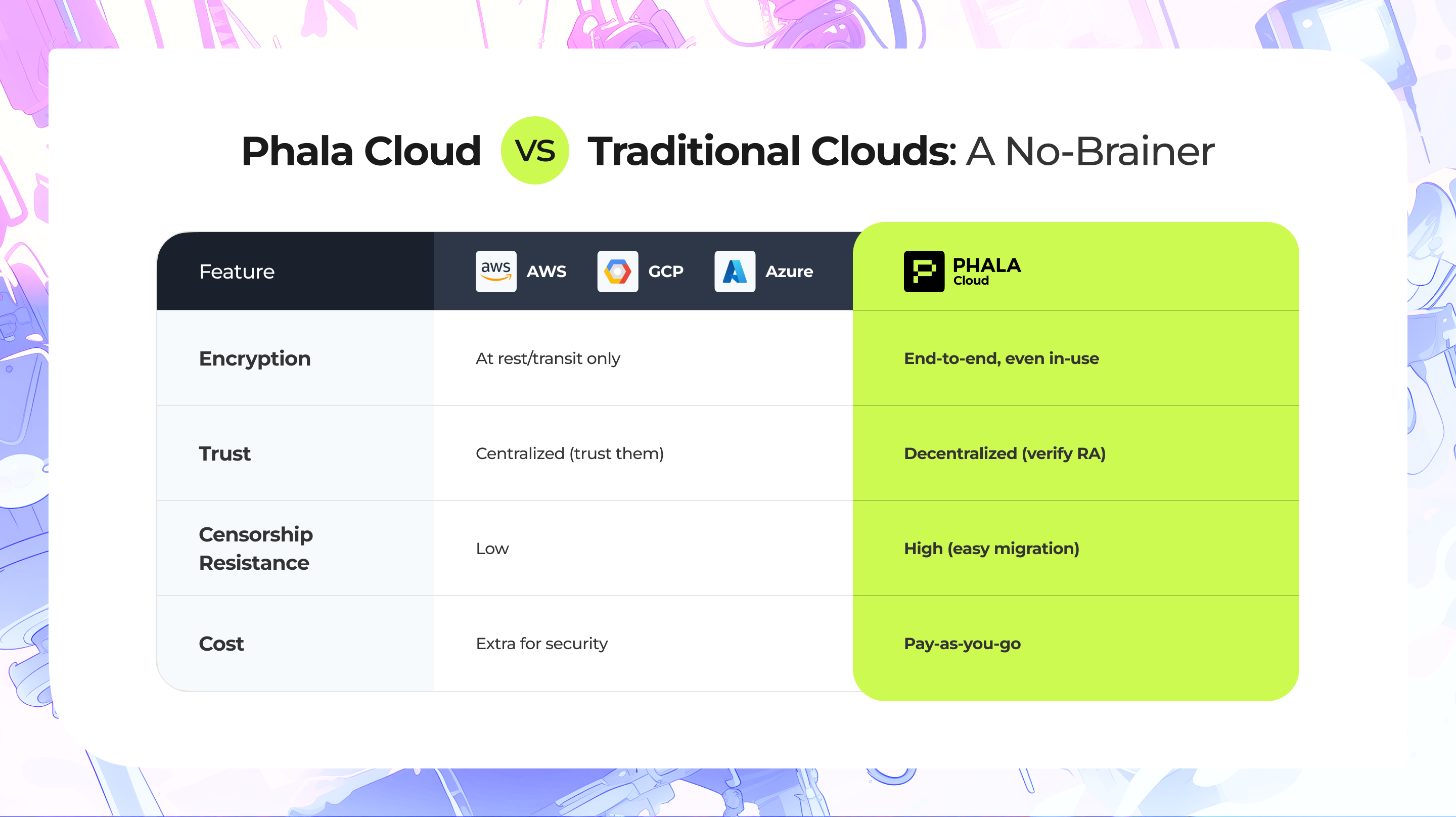
Phala Cloud’s decentralized trust and hardware-enforced security blow traditional clouds out of the water for Web3.
Get Started: Your Developer Roadmap
Building a secure Web3 backend is easier than you think with Phala Cloud. Here’s how to jump in:
- Migrate an Existing App: Follow the migration guide to TEE-ify your backend.
- Start Fresh with Templates: Grab a pre-built base from templates—think wallets or DeFi protocols.
- Master the dstack SDK: Dig into the dstack repo for TEE integration details.
Conclusion: Secure Web3 Starts Here
The Bybit hack wasn’t just a security fail—it was an architecture fail. Phala Cloud fixes that with TEEs and Web3 principles, delivering backends where:
- Data breaches can’t happen (it’s never exposed).
- Trust is proven, not assumed (thanks, RA).
- Security is hardware-deep, not a bolted-on afterthought.
For Web3 developers, Phala Cloud is your foundation for building apps that last. Ready to start?
- Check the Phala Cloud Docs.
- Explore live projects on the Explorer.
In Web3, security isn’t optional—it’s everything. Build it right with Phala Cloud.