Executive Summary
The healthcare industry generates 2.3 exabytes of data annually, yet 97% remains unused due to privacy constraints and regulatory barriers. This untapped potential represents unprecedented opportunities for medical breakthroughs, personalized treatments, and improved patient outcomes. Healthcare organizations face an impossible choice: maintain strict privacy compliance or unlock the transformative power of AI-driven data collaboration.
Privacy computing eliminates this trade-off, enabling healthcare organizations to harness AI's full potential while maintaining complete data sovereignty, ensuring global regulatory compliance, and building unbreakable patient trust. Organizations failing to implement robust privacy protections face mounting regulatory penalties, reputational damage, and exclusion from the emerging AI-powered healthcare economy.
1. The Healthcare Privacy Computing Imperative: Beyond Traditional Compliance
1.1 The Critical Security Gap in Healthcare AI Applications
Healthcare AI applications process the most sensitive data imaginable—patient records, genomic sequences, medical imaging, real-time biometric data, and proprietary clinical algorithms. Traditional healthcare security approaches protect data at rest and in transit but create catastrophic vulnerabilities during AI processing when patient data must be decrypted for computation.
This fundamental weakness creates unacceptable risks for healthcare organizations deploying AI systems. A single breach can expose thousands of patient records, violate HIPAA requirements, trigger massive penalties, and destroy decades of patient trust. Privacy computing technologies address this gap by protecting patient data throughout its entire lifecycle, including during active AI processing, using hardware-based trusted execution environments that maintain encryption even during the most complex medical computations.
1.2 Converging Healthcare Regulatory and Market Pressures
The healthcare regulatory landscape creates a perfect storm of compliance requirements that traditional cloud security cannot adequately address:
Healthcare-Specific Data Protection Frameworks:
- HIPAA (1996, updated 2013): Foundational US healthcare privacy with mandatory encryption, access controls, and breach notification requirements carrying penalties up to $1.5 million per incident
- 21st Century Cures Act (2016): Information blocking provisions with civil monetary penalties up to $1 million for healthcare providers restricting data access
- GDPR Article 9 (2018): Special category protections for health data with enhanced consent requirements and explicit lawful basis mandates
- FDA Software as Medical Device Guidance (2021): AI/ML-based medical devices requiring demonstrated safety and effectiveness with continuous monitoring
Emerging Healthcare AI Governance:
- EU AI Act High-Risk Applications (2024): Healthcare AI systems classified as high-risk with mandatory conformity assessments, quality management systems, and post-market surveillance
- FDA AI/ML Action Plan: Real-world performance monitoring for medical AI with predetermined change control plans
- WHO Ethics and Governance of AI for Health (2021): Global framework emphasizing transparency, accountability, and patient autonomy in healthcare AI
Industry-Specific Compliance Multipliers:
- Clinical Research: FDA 21 CFR Part 11 electronic records requirements with validation, audit trails, and electronic signatures
- Pharmaceutical: ICH E6 Good Clinical Practice guidelines for data integrity in clinical trials
- Medical Devices: ISO 13485 quality management with risk management per ISO 14971
- Genomics: Genetic Information Nondiscrimination Act (GINA) protections with emerging state-level genetic privacy laws
International Healthcare Data Transfer Crisis:
Privacy Shield invalidation has made international healthcare data transfers extraordinarily complex. Standard Contractual Clauses face heightened scrutiny for health data, creating operational nightmares for global healthcare organizations and multinational clinical trials.
1.3 The Business Case for Healthcare Privacy Computing
Market Access and Revenue Impact:
Healthcare organizations increasingly select AI partners based on demonstrated privacy capabilities rather than policy promises. Organizations without privacy computing face exclusion from:
- Government Healthcare Contracts: VA, CMS, and NIH requiring FedRAMP High authorizations with mathematical security guarantees
- International Clinical Trials: Multinational pharmaceutical companies processing patient data across jurisdictions
- Health Information Exchanges: Regional HIEs requiring cryptographic proof of patient data protection
- Academic Medical Centers: Research institutions demanding intellectual property protection for proprietary clinical algorithms
Competitive Advantage Through Technical Differentiation:
Privacy computing enables healthcare organizations to transform regulatory compliance from a cost center into competitive advantage. Instead of accepting security limitations, organizations can offer mathematically guaranteed patient privacy protection that enables new business models including:
- Federated Clinical Trials: Multi-site studies without centralizing patient data
- Real-World Evidence Generation: Pharmaceutical companies accessing diverse patient populations
- AI-Powered Precision Medicine: Personalized treatments using multi-institutional datasets
- Population Health Analytics: Public health agencies monitoring disease trends across healthcare systems
Risk Mitigation and Total Cost of Ownership:
Beyond compliance benefits, healthcare privacy computing significantly reduces:
- HIPAA Breach Penalties: Mathematical guarantees eliminate exposure to OCR fines averaging $2.2 million per incident
- Malpractice Insurance: Demonstrable privacy protection reduces healthcare liability premiums
- Regulatory Audit Costs: Automated compliance verification streamlines OCR, FDA, and state health department audits
- Patient Trust Restoration: Mathematical privacy guarantees accelerate recovery from privacy incidents
The Healthcare Strategic Imperative:
Healthcare organizations failing to implement privacy computing face mounting regulatory penalties, patient trust erosion, and competitive disadvantage as privacy computing becomes the baseline expectation for healthcare AI services. In healthcare, privacy computing is no longer optional but fundamental to sustainable AI innovation and patient care excellence.
2. Case Studies: Privacy Computing Transforming Healthcare AI
2.1 MELLODDY Consortium – Setting New Standards for Privacy Computing in Pharma R&D
The MELLODDY (Machine Learning Ledger Orchestration for Drug Discovery) consortium represents a pioneering deployment of privacy computing in the pharmaceutical industry, establishing a benchmark for secure, multi-party AI collaboration in drug discovery among global leaders like Amgen, AstraZeneca, Bayer, Boehringer Ingelheim, GSK, Janssen, Merck, Novartis, Astellas, and Servier.
Technical Implementation:
- Federated Learning: Each pharma company trains machine learning models locally on sensitive chemical and biological datasets. Only the model parameters—not raw data—are shared and securely aggregated, maintaining strict data confidentiality.
- Secure Multi-Party Computation (MPC) and Blockchain: MPC ensures privacy throughout the model aggregation process, while blockchain technology is used to record and audit key operations without exposing sensitive competitive or research details.
- Advanced Data Security Protocols: Data is de-identified, with all operations subjected to comprehensive security auditing. Both in-house and external checks verify that proprietary or patient-level data remains inaccessible to partners.
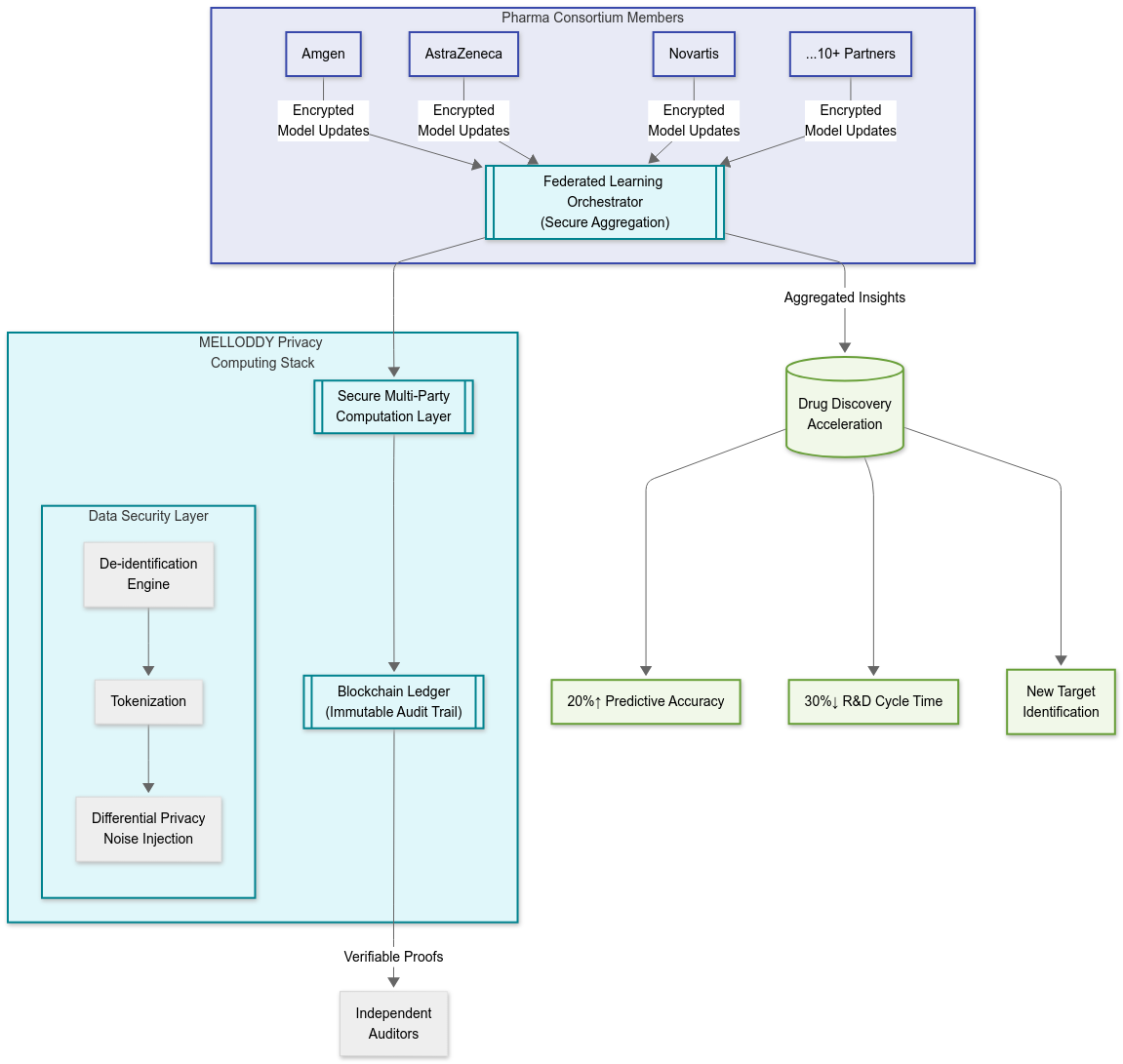
Healthcare Industry Impact:
MELLODDY’s approach has profoundly shifted expectations in pharmaceutical research:
- Regulatory and Competitive Benchmark: The project demonstrates that even competing pharma giants can safely collaborate, breaking data silos without compromising intellectual property or patient privacy. This opens new avenues for cross-company AI innovation under strict legal compliance (GDPR, HIPAA).
- Market Influence: Pharmaceutical and health AI companies that cannot demonstrate mathematically verifiable privacy protections—enabled by federated learning and MPC—face challenges accessing privacy-conscious markets and advanced collaborations. MELLODDY sets a precedent, pushing the entire industry toward provable, technical guarantees rather than policy-level assurances.
- Acceleration of Drug Discovery: By securely pooling insights without sharing sensitive data, participating companies improved predictive accuracy in drug candidate selection, significantly advancing R&D efficiency.
MELLODDY has thus established a new baseline for privacy in pharmaceutical data science. Future healthcare AI and SaaS offerings will be measured against standards of provable privacy, with market access and trust increasingly tied to the adoption of such advanced computing frameworks.
2.2 California Precision Medicine Consortium - Establishing New Standards for Healthcare Privacy Computing
The California Precision Medicine Consortium (CPMC), led by UC San Diego in partnership with multiple University of California medical centers, Cedars-Sinai Medical Center, and other leading healthcare institutions, has made a strategic decision to invest heavily in privacy computing technologies for precision medicine research. Their comprehensive implementation of federated learning and privacy-preserving analytics demonstrates that privacy computing is not a research luxury, but a healthcare imperative that directly impacts research velocity, patient trust, and scientific breakthrough potential.
The consortium's architecture centers on the pSCANNER Clinical Data Research Network, integrating clinical data from over 21 million patients while maintaining cryptographic isolation and patient sovereignty:
Patient Data Sovereignty: Clinical data remains encrypted and controlled exclusively by each healthcare institution, with encryption keys never leaving institutional boundaries. The system implements patient-controlled consent protocols that allow individuals to verify data use compliance before authorizing research participation.
Research Institution Protection: Proprietary clinical algorithms, research methodologies, and institutional intellectual property are protected through encrypted storage and runtime isolation within distributed computing environments. This prevents competitive intelligence exposure while enabling collaborative research advancement.
Consortium-Wide Assurance: The framework provides cryptographic proof of HIPAA compliance and research ethics adherence, enabling CPMC to conduct multi-institutional studies while maintaining the highest standards of patient privacy and regulatory compliance.
Technical Architecture Highlights:
- Federated Clinical Analytics: Distributed regression and statistical analyses performed across institutions without centralizing patient data, enabling real-time comparative effectiveness research while maintaining patient privacy
- Privacy-Preserving Genomic Research: Advanced differential privacy techniques protect individual genetic information while enabling population-level genomic discoveries
- Patient-Centric Consent Management: Granular consent controls allowing patients to authorize specific research uses while maintaining privacy protection for all other applications
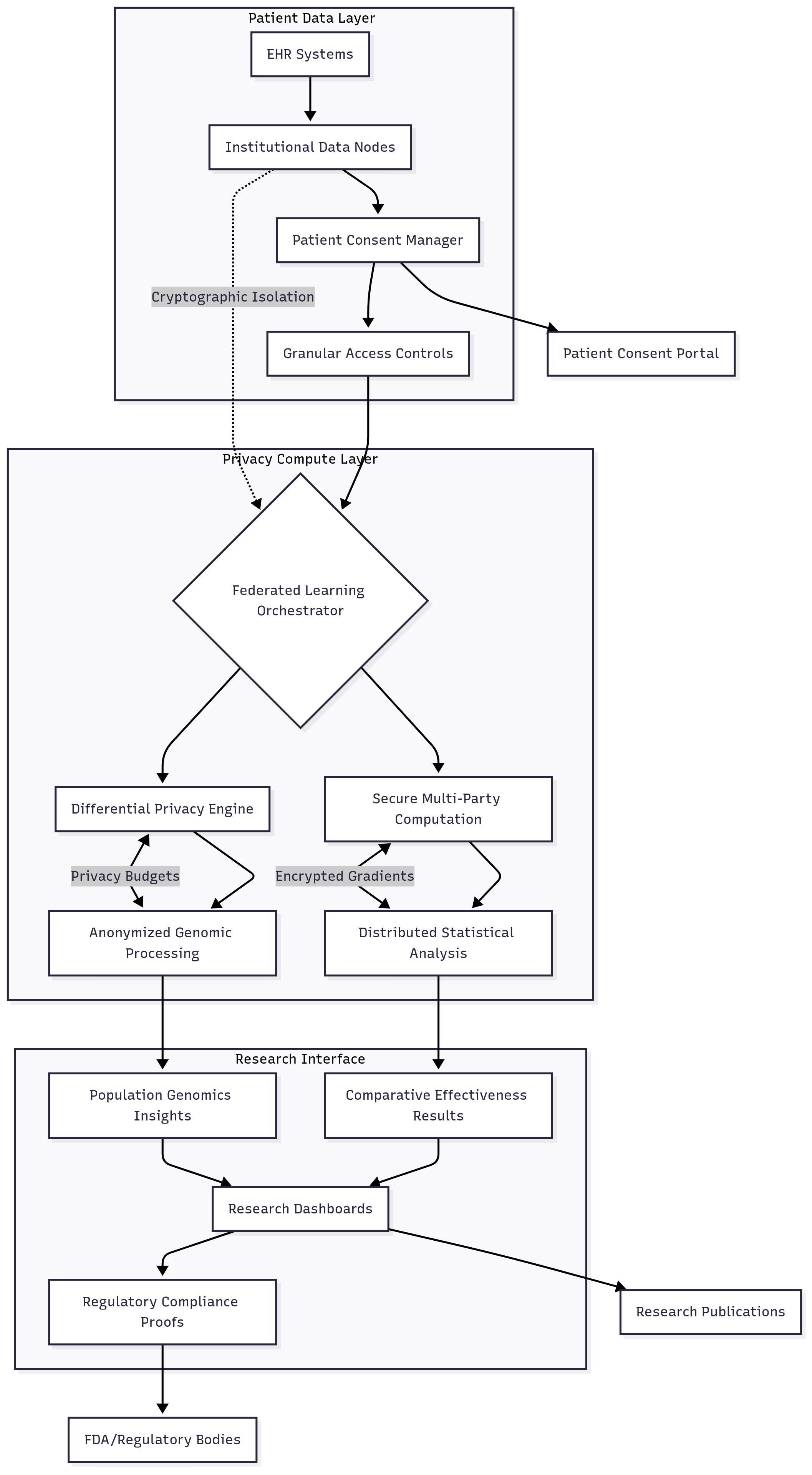
Healthcare Industry Impact:
CPMC's comprehensive investment in privacy computing reflects healthcare research realities:
Research Acceleration: Enables processing of sensitive patient data across institutional boundaries, unlocking research that was previously impossible due to privacy constraints
Patient Trust Enhancement: Mathematical privacy guarantees increase patient willingness to participate in precision medicine research, expanding cohort diversity and research impact
Competitive Research Differentiation: Protects institutional clinical expertise and research methodologies while enabling collaborative scientific advancement
Regulatory Leadership: Demonstrates gold standard approaches to healthcare data privacy that influence federal precision medicine initiatives and international research collaborations
CPMC's privacy computing deployment has fundamentally transformed healthcare research by proving that mathematical privacy guarantees enable research acceleration and patient trust previously impossible through traditional approaches. The consortium's success processing millions of patient records has established privacy computing as essential infrastructure, becoming the gold standard that accelerates adoption across academic medical centers, pharmaceutical companies, and government agencies seeking to replicate CPMC's research velocity and patient trust advantages.
3. Healthcare-Specific AI+SaaS Applications
3.1 Federated Clinical Research Platform
Best Practice Industry: Multi-Site Clinical Trials + AI + SaaS
Target Healthcare Organizations: Academic medical centers, pharmaceutical companies, contract research organizations, specialty hospitals, rare disease consortiums

Challenge
A consortium of pediatric oncology centers needed to develop AI-powered treatment protocols by analyzing combined patient data across institutions. However, patient privacy regulations, institutional policies, and the highly identifiable nature of rare disease data made traditional data sharing impossible. Each institution had insufficient patient populations for meaningful AI training, creating a critical barrier to advancing pediatric cancer care.
Solution Highlights
TEE-Based Federated Learning for Clinical Data: Implementation of federated learning protocols within trusted execution environments, enabling each medical center to train AI models locally while contributing encrypted model updates to shared clinical algorithms. Patient data never leaves institutional security perimeters, maintaining absolute privacy protection.
Secure Multi-Party Clinical Computation: Advanced cryptographic protocols aggregate local model updates using homomorphic encryption within confidential computing enclaves. This prevents any institution from accessing others' patient data while enabling collaborative development of superior treatment protocols.
Healthcare-Verified Attestation: Each federated learning node operates within verified TEEs providing cryptographic proof of HIPAA compliance and patient data protection. Remote attestation enables participating institutions to validate that partners use approved, compliant software before sharing clinical insights.
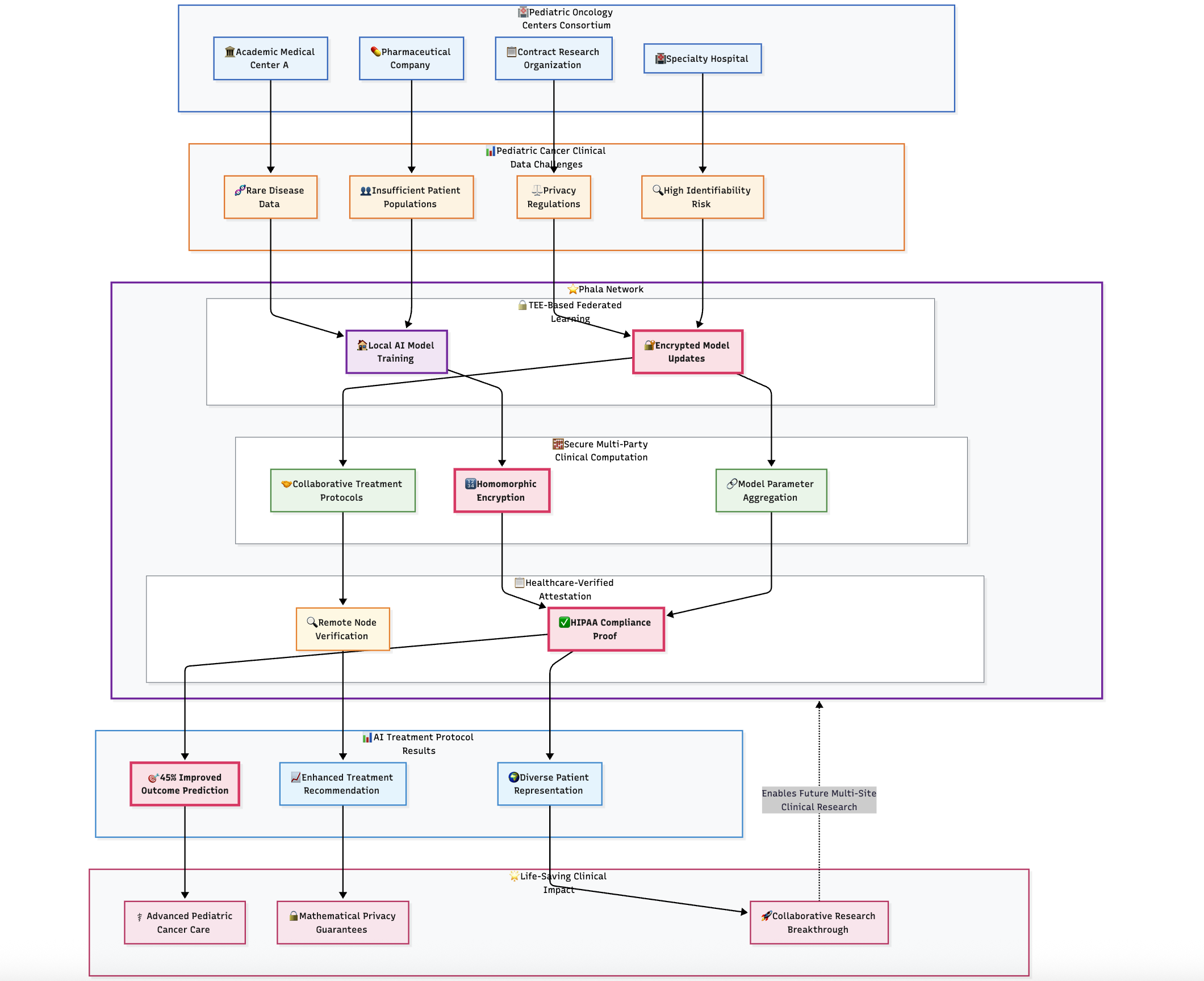
Results and Impact
The federated learning implementation enabled participating oncology centers to develop AI treatment protocols with 45% improved patient outcome prediction compared to single-institution training. Treatment recommendation accuracy increased substantially due to diverse patient representation across ethnic, genetic, and socioeconomic populations. Privacy computing made this life-saving collaboration possible by providing mathematical guarantees that patient privacy would remain absolutely protected throughout the research process.
3.2 Hospital-Wide AI Clinical Decision Support Platform
Best Practice Industry: Healthcare AI + Clinical Decision Support + SaaS
Target Healthcare Organizations: Health systems, academic medical centers, specialty hospitals, integrated delivery networks, accountable care organizations

Challenge
A large health system required AI-powered clinical decision support across all care settings while maintaining strict patient privacy protection and regulatory compliance. Traditional cloud-based AI services posed unacceptable risks for processing patient health information, creating a choice between accepting privacy risks or forgoing AI benefits for patient care.
Solution Highlights
Confidential Clinical AI Deployment: Enterprise-grade clinical AI models deployed within confidential computing enclaves that process patient data without exposing information to external parties. Hardware-level isolation ensures even cloud administrators cannot access patient health information during AI processing.
Role-Based Clinical Access in TEEs: Sophisticated access controls implemented within TEEs ensure clinicians only interact with patient data appropriate to their roles and care relationships. Fine-grained data isolation maintained while preserving AI functionality across different clinical specialties and care teams.
Privacy-Preserving Clinical Learning: Federated learning protocols enable AI model enhancement across departments and hospital locations without centralizing patient data. Local model updates remain encrypted while contributing to overall clinical AI capabilities and treatment recommendations.
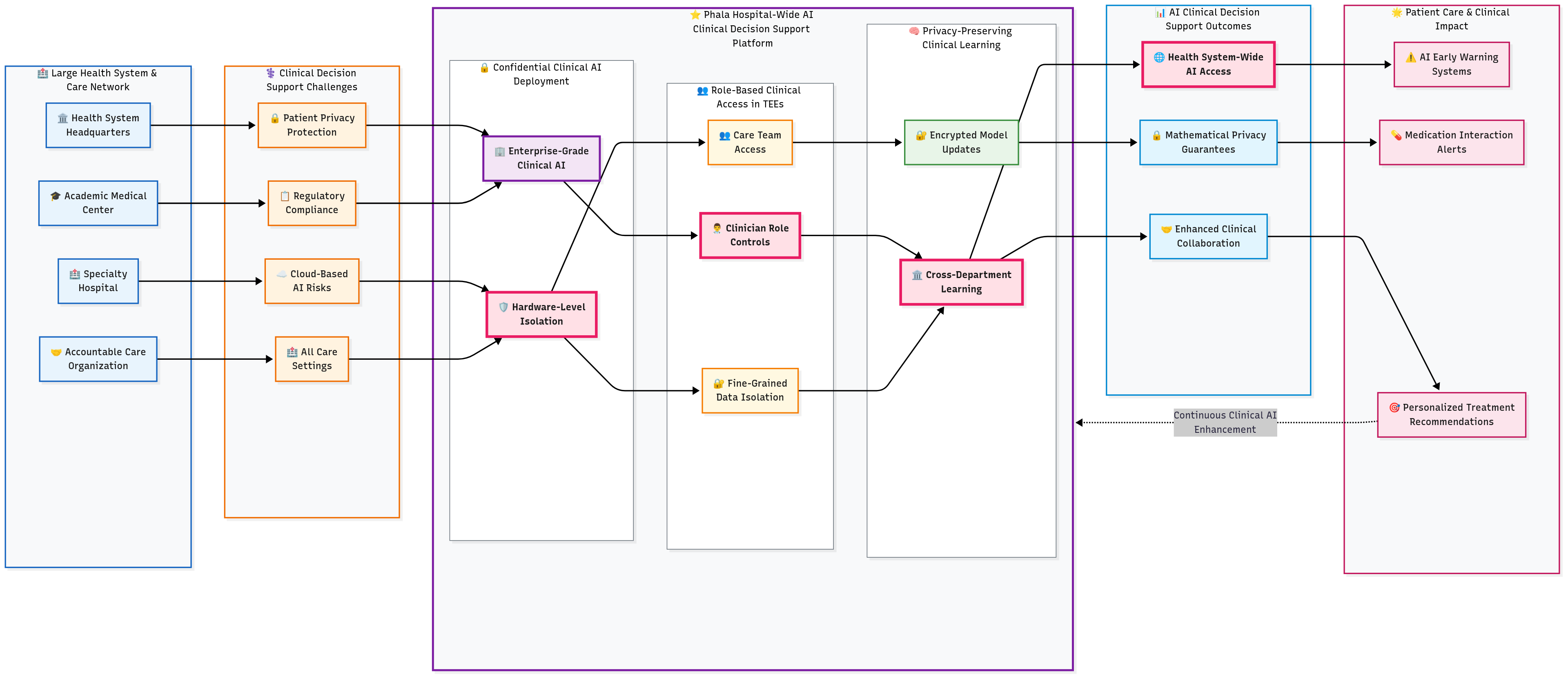
Results and Impact
The implementation enabled health system-wide access to AI clinical decision support without compromising patient privacy protection. Privacy computing made enterprise clinical AI deployment feasible by providing mathematical guarantees that patient information would remain protected throughout processing, enabling new forms of clinical collaboration and evidence-based care delivery. Clinical outcomes improved through AI-powered early warning systems, medication interaction alerts, and personalized treatment recommendations.
3.3 Pharmaceutical Real-World Evidence Platform
Best Practice Industry: Drug Development + Real-World Data + AI + SaaS
Target Healthcare Organizations: Pharmaceutical companies, biotechnology firms, contract research organizations, health insurers, healthcare analytics companies

Challenge
Pharmaceutical companies developing new therapies needed access to diverse, real-world patient data to demonstrate drug safety and efficacy for regulatory submissions. However, healthcare providers were reluctant to share patient data due to HIPAA requirements, institutional policies, and patient privacy concerns, creating barriers to evidence generation and drug approval processes.
Solution Highlights
TEE-Based Real-World Data Processing: Sensitive patient data from electronic health records, claims databases, and registries processed within confidential computing enclaves that prevent access by pharmaceutical companies or platform administrators. Healthcare data remains encrypted throughout analysis while enabling sophisticated outcomes research.
Secure Longitudinal Patient Analytics: Advanced analytics track patient outcomes over time using encrypted patient identifiers that enable longitudinal analysis without exposing patient identity. TEE isolation prevents unauthorized access to patient information while enabling robust real-world evidence generation.
Privacy-Preserving Comparative Effectiveness Research: Multi-party computation enables pharmaceutical companies to compare their products against competitors using real-world data without exposing proprietary information or patient details to competing organizations.
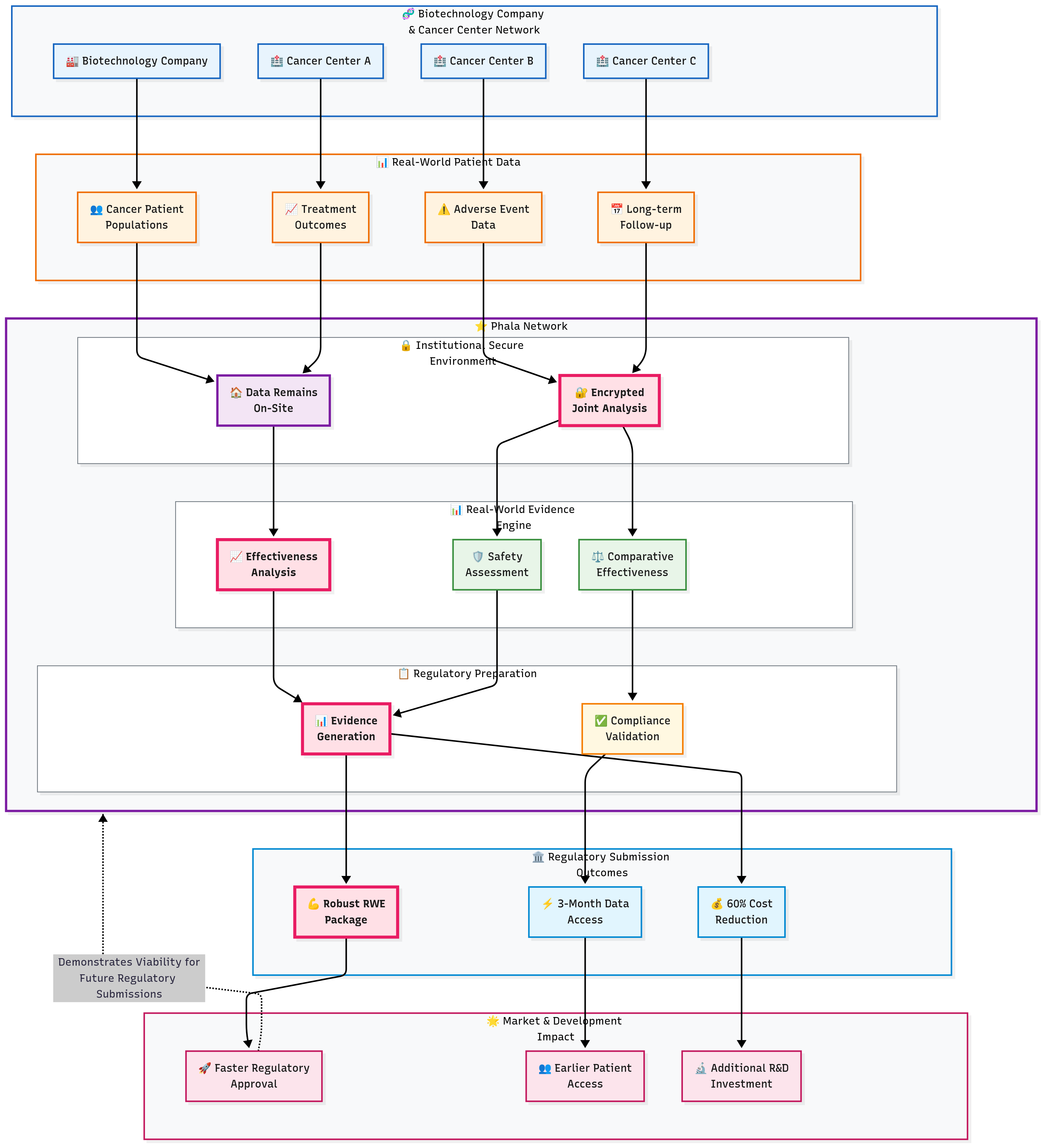
Results and Impact
The privacy computing implementation enabled pharmaceutical companies to access real-world evidence that accelerated regulatory approvals and supported value-based contracting negotiations. Healthcare providers gained confidence in data sharing through mathematical privacy guarantees, unlocking valuable revenue streams from pharmaceutical partnerships. Patient privacy remained absolutely protected throughout the evidence generation process, maintaining trust while advancing therapeutic development.
3.4 Population Health Surveillance Platform
Best Practice Industry: Public Health + Disease Surveillance + AI + SaaS
Target Healthcare Organizations: State health departments, CDC, WHO, health information exchanges, integrated delivery networks, academic research institutions
Challenge
Public health agencies needed real-time disease surveillance capabilities using data from multiple healthcare systems to monitor outbreaks, track population health trends, and evaluate intervention effectiveness. Traditional surveillance approaches required manual reporting with significant delays, while automated approaches raised privacy concerns among healthcare providers and patients.
Solution Highlights
TEE-Based Syndromic Surveillance: Real-time analysis of clinical data streams within trusted execution environments enabling early outbreak detection without exposing patient information. Healthcare providers contribute encrypted data feeds while maintaining complete patient privacy protection.
Privacy-Preserving Epidemiological Modeling: Advanced AI models analyze population health patterns using differential privacy techniques within TEEs, providing statistical insights while preventing identification of individual patients or healthcare facilities.
Secure Multi-Jurisdictional Collaboration: Cross-border health surveillance enabling international disease monitoring while complying with varying national data protection requirements. TEE-based processing satisfies data sovereignty requirements while enabling global health security.
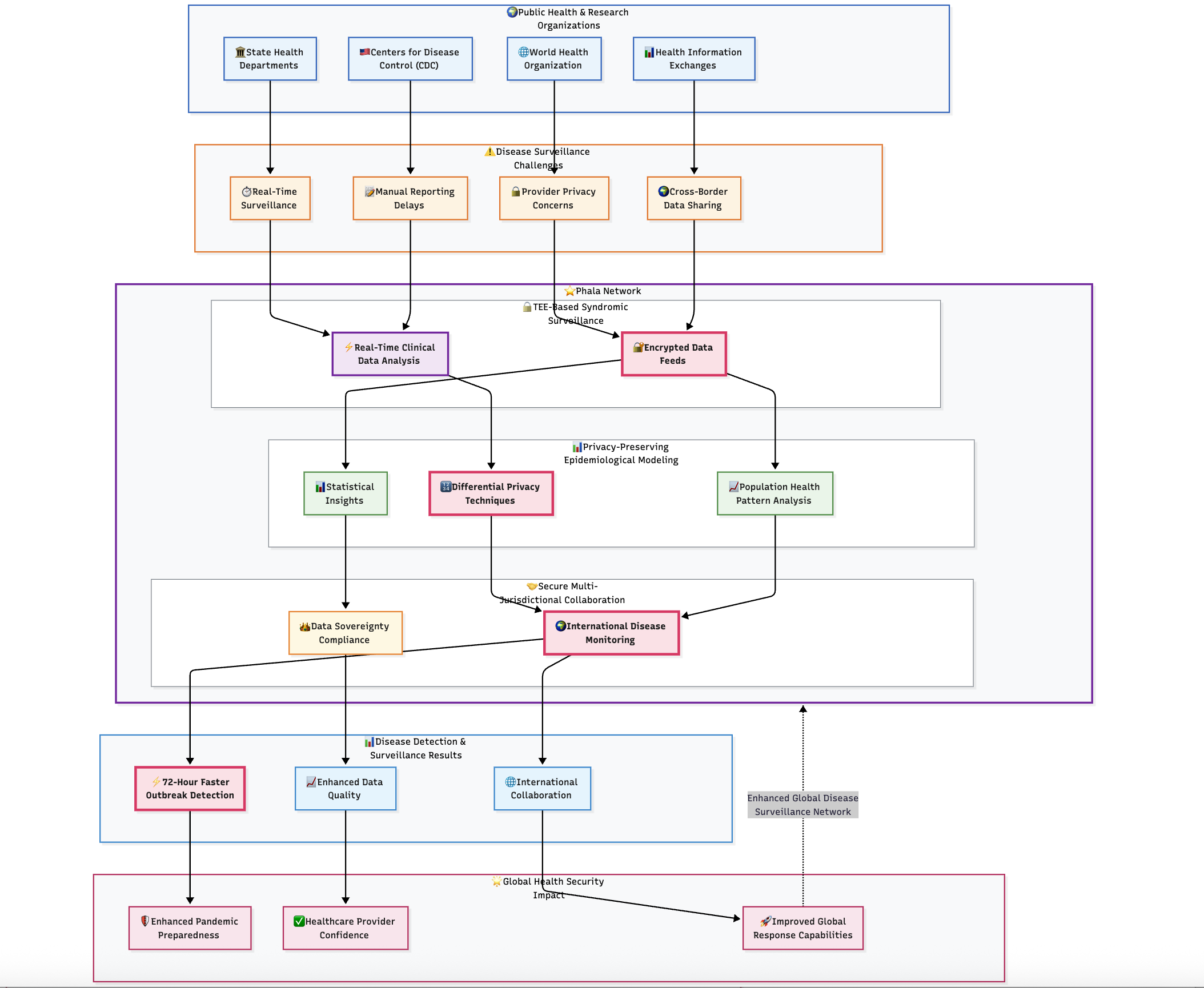
Results and Impact
The privacy computing implementation enabled public health agencies to detect disease outbreaks 72 hours faster than traditional surveillance methods while maintaining absolute patient privacy protection. Healthcare providers gained confidence in automated reporting through mathematical privacy guarantees, improving surveillance data quality and completeness. International collaboration improved through privacy-preserving cross-border data sharing, enhancing global pandemic preparedness and response capabilities.
3.5 Genomic Research Collaboration Platform
Best Practice Industry: Genomics + Precision Medicine + AI + SaaS
Target Healthcare Organizations: Academic medical centers, pharmaceutical companies, genomics companies, biotechnology firms, precision medicine initiatives

Challenge
Genomic research requires large, diverse datasets to identify genetic variations associated with disease risk and treatment response. However, genomic data is highly identifiable and sensitive, creating significant privacy barriers to the data sharing necessary for meaningful genetic research and precision medicine development.
Solution Highlights
TEE-Protected Genomic Analysis: Sensitive genomic data processed within confidential computing enclaves maintaining complete genetic privacy protection. Genome-wide association studies (GWAS) and pharmacogenomic analyses performed without exposing individual genetic information to researchers or platform operators.
Federated Genomic Learning: Privacy-preserving federated learning enables genetic research across multiple biobanks and research institutions without centralizing genomic data. Each institution maintains complete control over genetic information while contributing to shared research advances.
Secure Precision Medicine Development: AI-powered precision medicine algorithms developed using multi-institutional genomic datasets while protecting both patient genetic privacy and institutional intellectual property. Advanced differential privacy techniques provide additional protection against inference attacks.
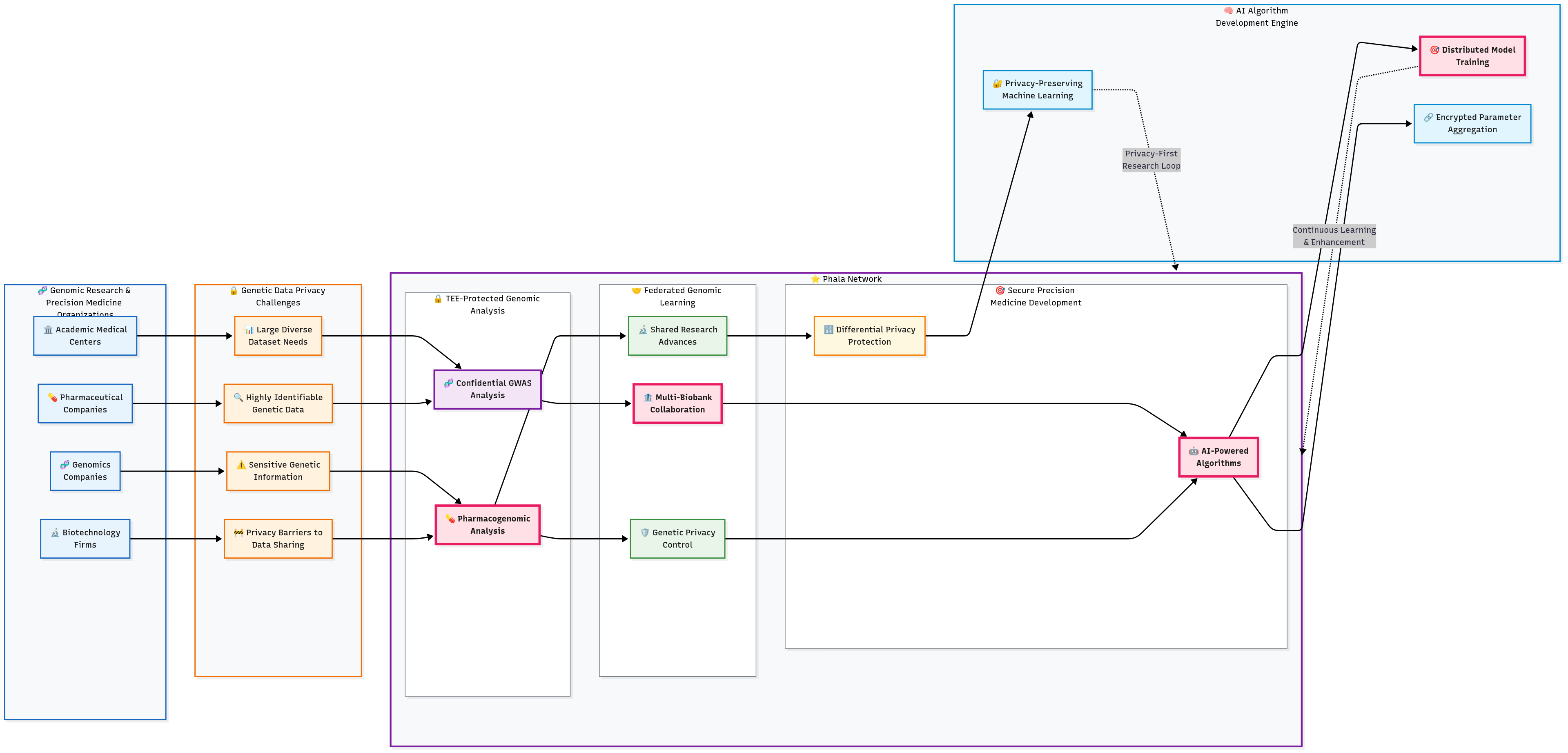
Results and Impact
The privacy computing implementation enabled genomic research consortiums previously impossible due to privacy constraints. Research participants gained confidence through mathematical genetic privacy guarantees, increasing study enrollment and genetic diversity. Precision medicine algorithm accuracy improved through access to larger, more diverse genomic datasets while maintaining absolute genetic privacy protection throughout the research process.
4. Technical Deep Dive: Healthcare Privacy Computing Technologies
Privacy computing for healthcare extends beyond basic data protection to address the unique requirements of medical data, clinical workflows, and healthcare regulations. Healthcare privacy computing must handle the most sensitive personal information while enabling complex AI analyses that can save lives and advance medical science.
Healthcare-Specific Security Requirements:
Healthcare data requires enhanced protection due to its highly personal nature, long-term value, and strict regulatory requirements. Privacy computing for healthcare implements:
- HIPAA-Compliant Cryptographic Guarantees: Technical safeguards meeting and exceeding HIPAA Security Rule requirements through mathematical verification rather than policy compliance
- Patient Consent Management: Granular consent controls enabling patients to authorize specific uses while maintaining privacy protection for all other applications
- Clinical Workflow Integration: Seamless integration with electronic health records, clinical decision support systems, and healthcare information exchanges
Medical Data Sovereign Architecture:
Healthcare privacy computing enables medical organizations to maintain cryptographic control over patient data even when processing occurs on third-party infrastructure. This capability directly addresses healthcare data sovereignty requirements while enabling access to cloud-scale AI resources—transforming the traditional trade-off between compliance and innovation into a competitive advantage for patient care.
Healthcare Data Clean Room Implementation:
Medical data clean rooms enable privacy-preserving collaboration where multiple healthcare organizations analyze combined patient datasets without exposing underlying health information to participants. Modern implementations use trusted execution environments for mathematical isolation, with computation in hardware-protected enclaves that prevent data exfiltration while enabling joint medical research and population health analysis.
5. Phala Healthcare Solution: Bridging Medical Innovation and Privacy Excellence
5.1 Healthcare-Specific Security Architecture
Phala's healthcare-grade confidential computing platform addresses four critical security gaps that traditional healthcare cloud environments cannot solve:
1. Healthcare Trust Verification: Creates an unbroken verification chain specifically designed for medical applications, from hardware microcode through healthcare-specific operating systems to clinical applications—providing end-to-end medical software supply chain verification meeting FDA Software as Medical Device requirements.
2. HIPAA-Compliant Network Architecture: Implements healthcare-specific end-to-end encryption with unique cryptographic keys per patient data workload, preventing network compromise while maintaining seamless clinical workflow integration and emergency access capabilities.
3. Patient Data Lifecycle Protection: Maintains encryption throughout the entire patient data lifecycle, including during AI processing within TEE environments, addressing the fundamental weakness of in-memory patient data exposure that enables catastrophic healthcare breaches.
4. Healthcare Consortium Verification: Phala's breakthrough approach implements healthcare consortium networks for immutable security attestation verification specific to medical applications. This creates independently auditable proof of HIPAA compliance and patient privacy protection that satisfies the most stringent healthcare regulatory requirements.
5.2 Healthcare Integration and Deployment Strategy
Seamless Clinical Integration:
- EHR Compatibility: Direct integration with Epic, Cerner, and other major electronic health record systems
- Clinical Workflow Preservation: Standard healthcare IT workflows remain unchanged, minimizing disruption to patient care
- FHIR-Compliant APIs: Full Fast Healthcare Interoperability Resources (FHIR) support for seamless healthcare data exchange
Healthcare-Specific Phased Implementation:
Phase 1: Clinical Assessment & Foundation (Months 1-3)
- Comprehensive patient data classification and healthcare threat modeling
- HIPAA compliance gap analysis and remediation planning
- Clinical pilot project identification and healthcare governance framework establishment
Phase 2: Clinical Pilot Implementation (Months 4-8)
- Limited scope deployment with clinical performance baseline establishment
- Healthcare security policy development and HIPAA compliance testing
- Clinical workflow optimization and healthcare staff training
Phase 3: Healthcare System Deployment (Months 9-18)
- Extension across additional clinical applications and patient populations
- Clinical process automation and medical staff training programs
- Integration with healthcare IT service management and clinical decision support systems
Phase 4: Advanced Healthcare Capabilities (Months 19-24)
- Federated clinical learning and advanced medical analytics deployment
- Cross-institutional healthcare verification framework implementation
- Strategic planning for healthcare ecosystem-wide privacy computing adoption
6. Healthcare Strategic Implementation and Competitive Transformation
6.1 Healthcare Business Value Across Stakeholder Categories
Privacy computing fundamentally transforms how healthcare organizations approach regulatory compliance and patient trust by replacing policy-based assurances with mathematical guarantees. This creates unprecedented competitive advantages across critical healthcare stakeholder categories:
Healthcare Regulatory Compliance:
- HIPAA Mathematical Verification: Cryptographic proof satisfying OCR audits through technical demonstration rather than policy documentation
- FDA AI/ML Compliance: Continuous monitoring and validation of medical AI systems with immutable audit trails
- International Health Data Protection: Enabling compliant cross-border medical research and international patient care
Clinical Research Transformation:
- Federated Clinical Trials: Multi-site studies without centralizing patient data, accelerating research timelines
- Real-World Evidence Generation: Pharmaceutical access to diverse patient populations while maintaining privacy
- Genomic Research Collaboration: Privacy-preserving genetic studies enabling precision medicine advancement
Healthcare AI Provider Advantages:
- Patient Trust Enhancement: Mathematical privacy guarantees addressing patient concerns about health data sharing
- Clinical Integration: Seamless deployment in healthcare environments with regulatory compliance built-in
- Healthcare Market Access: Enabling AI services for previously inaccessible high-security healthcare markets
6.2 Healthcare Strategic Implementation Framework
Immediate Healthcare Market Opportunities:
The convergence of healthcare AI advancement, patient privacy expectations, and regulatory evolution creates unprecedented opportunities for healthcare organizations implementing privacy computing:
Premium Healthcare Market Access:
- Government Healthcare Contracts: VA, DOD, and federal healthcare agencies requiring mathematical security guarantees
- Academic Medical Centers: Research institutions demanding protection for clinical intellectual property
- Specialty Healthcare: High-acuity providers serving patients with elevated privacy expectations
- International Healthcare: Cross-border care and research requiring data sovereignty compliance
Healthcare Investment Prioritization Framework:
- Clinical Impact Use Cases: Focus on applications with clear patient care benefits and clinical adoption potential
- Healthcare Partnership Strategy: Leverage specialized medical expertise while building internal clinical capabilities
- Medical Staff Development: Critical investment in healthcare-specific privacy computing skills
6.3 Call to Action: Seizing the Healthcare Privacy Computing Advantage
Privacy computing represents both a fundamental healthcare market opportunity and clinical necessity. Healthcare organizations successfully implementing privacy computing capabilities will capture high-value clinical markets and research opportunities that define tomorrow's medical landscape.
Next Steps for Healthcare Leaders:
- Conduct Healthcare Privacy Assessment: Evaluate current patient privacy posture against clinical requirements and regulatory mandates
- Engage Healthcare Technology Partners: Understand available options for healthcare-specific privacy computing implementation
- Begin Clinical Skills Development: Invest in medical informatics capabilities for privacy computing implementation and clinical operations
The Future Healthcare Landscape:
The future of healthcare AI will be defined by organizations that successfully balance medical innovation with absolute patient privacy protection. Privacy computing technologies provide the foundation for this balance, enabling continued clinical advancement while meeting the highest standards of patient data protection.
Healthcare organizations that act decisively to implement privacy computing capabilities today will be best positioned for success in the evolving medical landscape—transforming regulatory compliance from a clinical burden into a competitive advantage that opens new research opportunities, enables premium clinical services, and builds unbreakable patient trust through mathematical guarantees rather than policy promises.
About Phala Network: Leading provider of healthcare privacy computing solutions enabling medical organizations to harness AI power while maintaining complete patient data sovereignty and healthcare regulatory compliance. Contact our healthcare solutions team to begin your clinical privacy computing transformation and capture the competitive advantages that mathematical patient privacy protection delivers.