
Hey developers! If you’re building a crypto wallet MCP and want to integrate it with AI tools while keeping the private keys safe, Phala Cloud’s Trusted Execution Environment (TEE) paired with a Model Context Protocol (MCP) server offers a secure solution. Using the NEAR Blockchain MCP server as an example, this guide will walk you through setting up a Crypto Wallet MCP server on Phala Cloud, ensuring your wallet’s private keys are protected from memory leaks and hacks. We’ll cover the risks of insecure setups, deployment steps, and how to connect your wallet to AI applications like Cherry Studio or Cursor. Let’s get started with a secure, efficient way to manage your crypto assets!
Why Use a Crypto Wallet MCP Server with Phala Cloud TEE?
Crypto wallets, especially those interacting with blockchains like Ethereum, Bitcoin, or NEAR, store private keys that control access to your assets. Integrating these wallets with AI agents—say, for automated trading or portfolio management—can be powerful, but it introduces significant risks if not done securely. The Model Context Protocol (MCP) enables AI tools to communicate with your wallet, but running this setup on a local machine leaves your private keys vulnerable to memory leaks, malware, or hacking attempts, potentially putting your wealth at risk.
The diagram below illustrates the difference between an insecure local setup and a secure TEE-based approach:
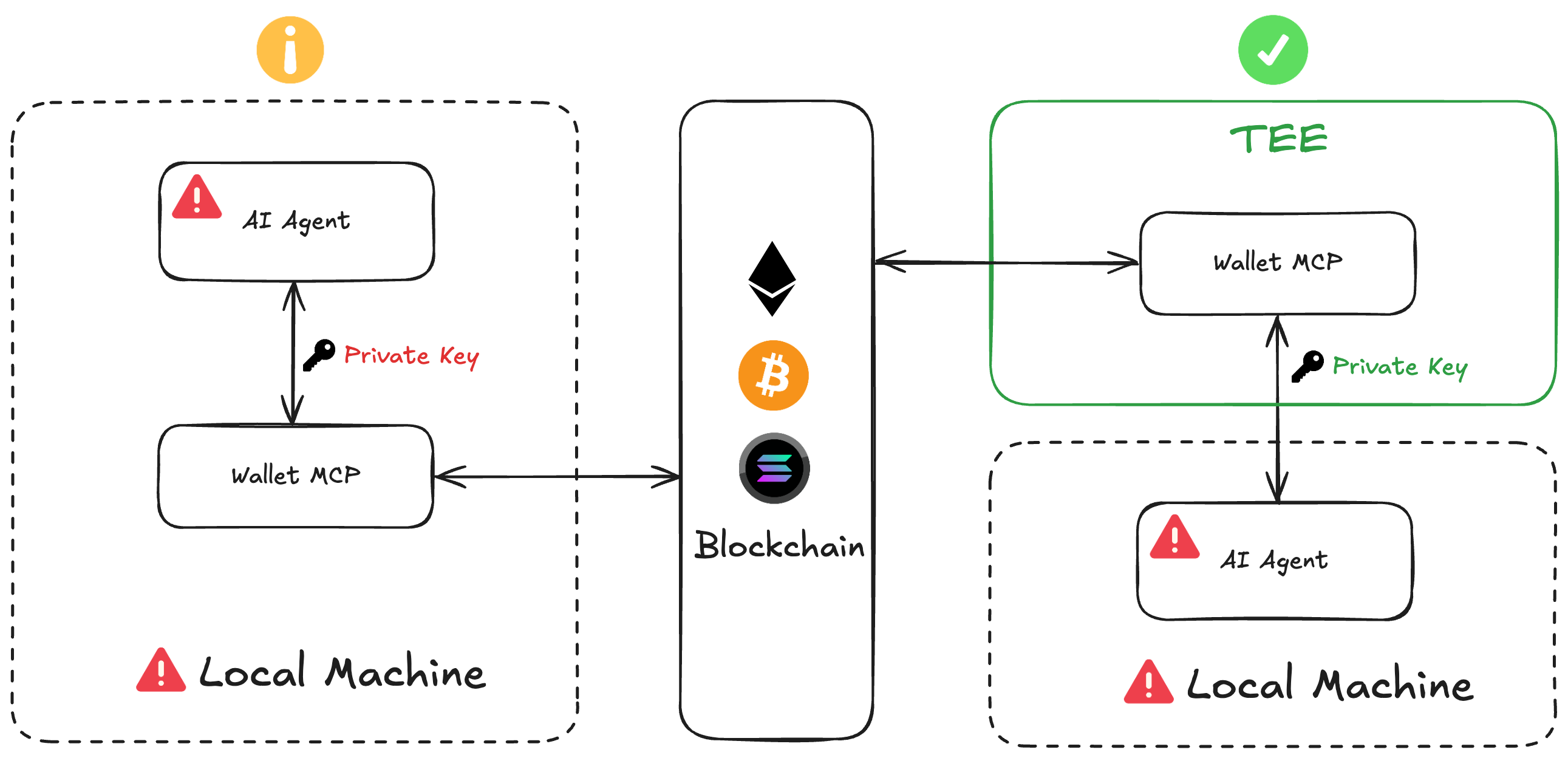
Crypto Wallet MCP Security Diagram
- Left Side (Insecure): On a local machine, the AI agent and Wallet MCP both have access to the private key. If the machine is compromised—via malware, memory leaks, or hacks—attackers can steal the key, gaining full control over your wallet and assets.
- Right Side (Secure): By putting the MCP server into TEE, the Wallet MCP runs in an isolated environment. The private key never leaves the TEE, and even the AI agent, running separately, can’t access it directly. The TEE ensures secure communication with the blockchain, protecting your assets.
Phala Cloud’s TEE-powered hosting addresses these risks by isolating your Crypto Wallet MCP server in a secure enclave. TEEs, backed by Intel TDX or AMD SEV, encrypt your private keys and computations, preventing unauthorized access even if the host system is compromised. Remote attestation verifies that your server is running in a genuine TEE, building trust with users or auditors. Plus, Phala Cloud’s fast deployment (1-day launches) and affordable pricing make it practical for developers working on NEAR, Ethereum, or other blockchains.
Key Security Considerations for Crypto Wallets
Before diving into deployment, let’s explore the risks of running a Crypto Wallet MCP server without a TEE, focusing on memory leaks and hacks:
- Memory Leaks: On a local machine, private keys stored in memory can be exposed through vulnerabilities like buffer overflows or side-channel attacks. Tools like memory scanners can extract keys if the system lacks proper isolation, leading to asset theft.
- Hacks and Malware: A compromised local machine—via phishing, malicious browser extensions, or unpatched software—can allow attackers to steal private keys. For example, clipboard hijacking malware can replace wallet addresses during transactions, redirecting funds to attackers.
- MCP-Specific Risks: As noted in Phala’s MCP security blog, MCP servers are prone to command injection and SSRF attacks which can bypass user approval and expose sensitive data.
Phala Cloud mitigates these risks:
- TEE Isolation: Private keys stay encrypted within the TEE, inaccessible to the host OS or external processes, preventing memory leaks.
- Attack Prevention: TEEs block command injection and SSRF by isolating the Crypto Wallet MCP server, ensuring only authorized interactions with the blockchain.
- Verifiable Trust: Remote attestation proves your server’s integrity, addressing trust issues common with MCP deployments.
- Privacy Protection: Phala’s on-chain Key Management System (KMS) securely manages keys (KMS Docs), reducing the risk of exposure.
By deploying your Crypto Wallet MCP server on Phala Cloud, you can safely integrate with AI tools while protecting your assets, making it ideal for developers working with NEAR or other blockchains.
Step-by-Step Guide: Deploying a Crypto Wallet MCP Server with NEAR AI on Phala Cloud
Let’s deploy a Crypto Wallet using the NEAR AI MCP server as an example. This demo uses a forked repository from NEAR AI (PR already sent to upstream), add Docker Compose and SSE transport support for Phala Cloud deployment.
We’ll use a test account on NEAR testnet to demonstrate the setup.
Follow these steps to get your secure wallet server up and running:
Step 1: Sign Up for Phala Cloud
Head to cloud.phala.network and create an account. You’ll receive $20 in free credits to deploy your Crypto Wallet MCP server and test it out—no upfront costs.
Step 2: Deploy a Confidential VM (CVM)
- Log into your Phala Cloud account and navigate to the dashboard.
- Click “Deploy” to start setting up your Confidential VM (CVM), which will run in a TEE for enhanced security.
- Under “Pick How to Deploy,” select the first option: “docker-compose.yml.”
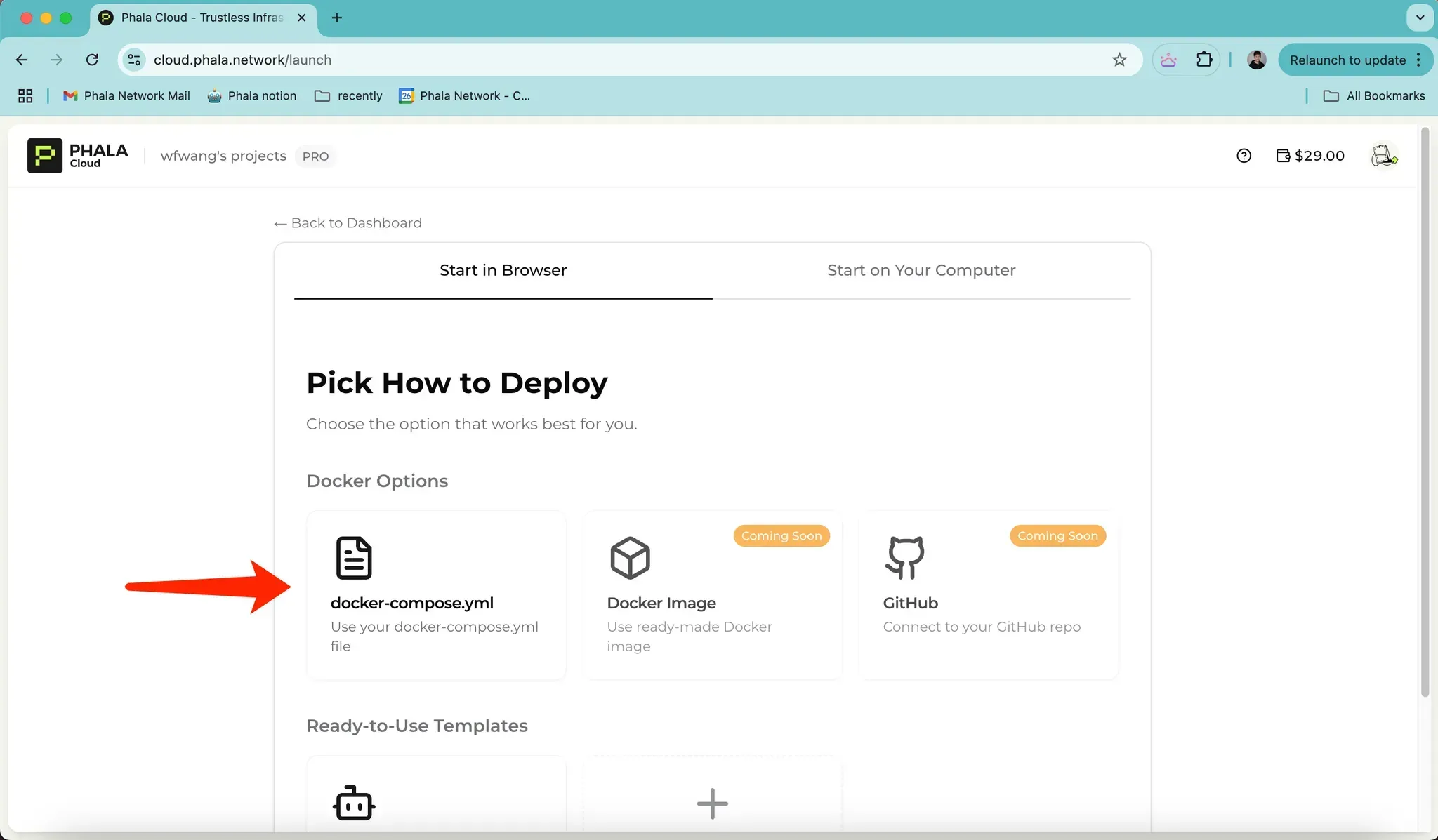
Step 3: Configure the NEAR AI MCP Server
- Grab the Docker Compose file for the NEAR AI MCP server from this GitHub link: NEAR-MCP Docker Compose. Copy the .yml code.
- On the deploy page, go to the “Advanced” section next to “Quick Start.”
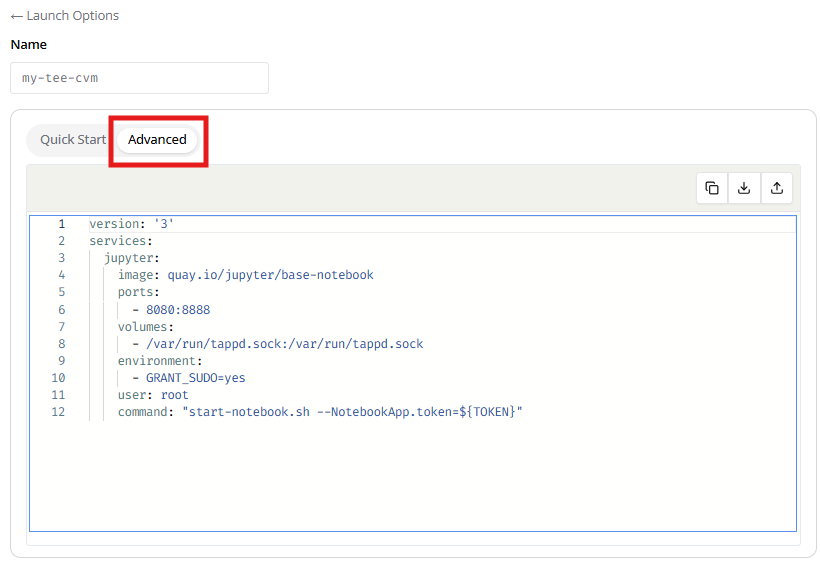
- Remove the existing .yml code and paste the copied code from GitHub.
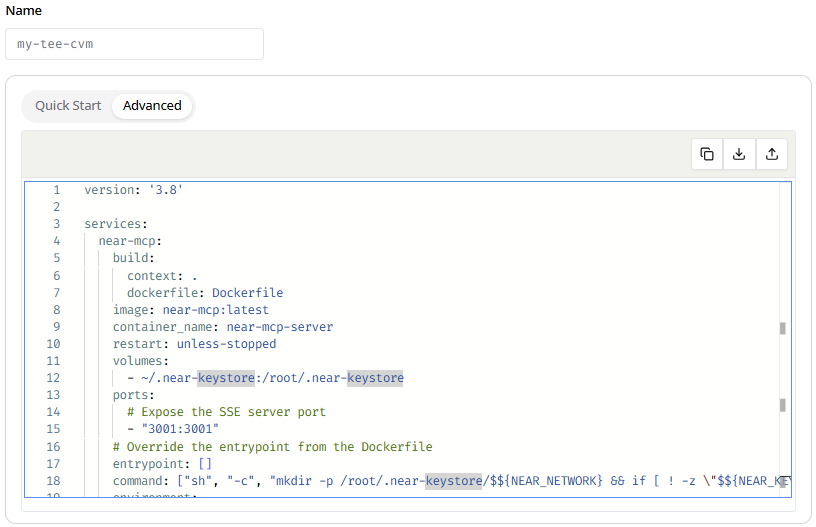
- Important Tweak: Phala Cloud doesn’t support building Docker images from source in the .yml file.
Delete the build command.
build: context: . dockerfile: Dockerfile - Specify a Docker image from Docker Hub or another registry by adding or updating the image field.
For this example, we use a pre-built image (you’ll need to find or build one; for demo purposes, assume tolak/near-mcp-server)
image: tolak/near-mcp-server - Give your CVM a name, like “near-mcp-server.”
Step 4: Set Up Compute Resources and Secrets
- Choose the compute resources for your CVM.
- Scroll down to the “Encrypted Secrets” dropdown.
Add the following environment variables
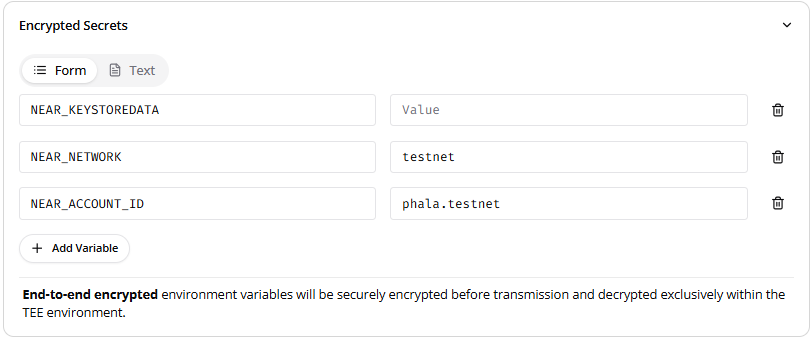
- NEAR_KEYSTOREDATA: Use the NEAR CLI to access your account’s keystore data (stored locally if using the legacy approach). Encode the JSON keystore data in base64 see the example below, then paste the encoded value here.
base64 -i cat ~/.near-credentialstestnet/phala.testnet/ed25519_FrWgBmDnbEERntvSVGizpUxk64LXNbaF3U77Du6VQDFR.json - NEAR_NETWORK: Set to testnet (or mainnet for production).
- NEAR_ACCOUNT_ID: Set to phala.testnet (or your account ID).
Example:
NEAR_KEYSTOREDATA=ewogICAgImFjY291bnRfaWQiOiAiUGhhbGFD...== NEAR_NETWORK=testnet NEAR_ACCOUNT_ID=phala.testnet
- NEAR_KEYSTOREDATA: Use the NEAR CLI to access your account’s keystore data (stored locally if using the legacy approach). Encode the JSON keystore data in base64 see the example below, then paste the encoded value here.
- Click “Create” to launch your CVM. Once it’s online, the container will start.
Step 5: Verify the Container and Access Logs
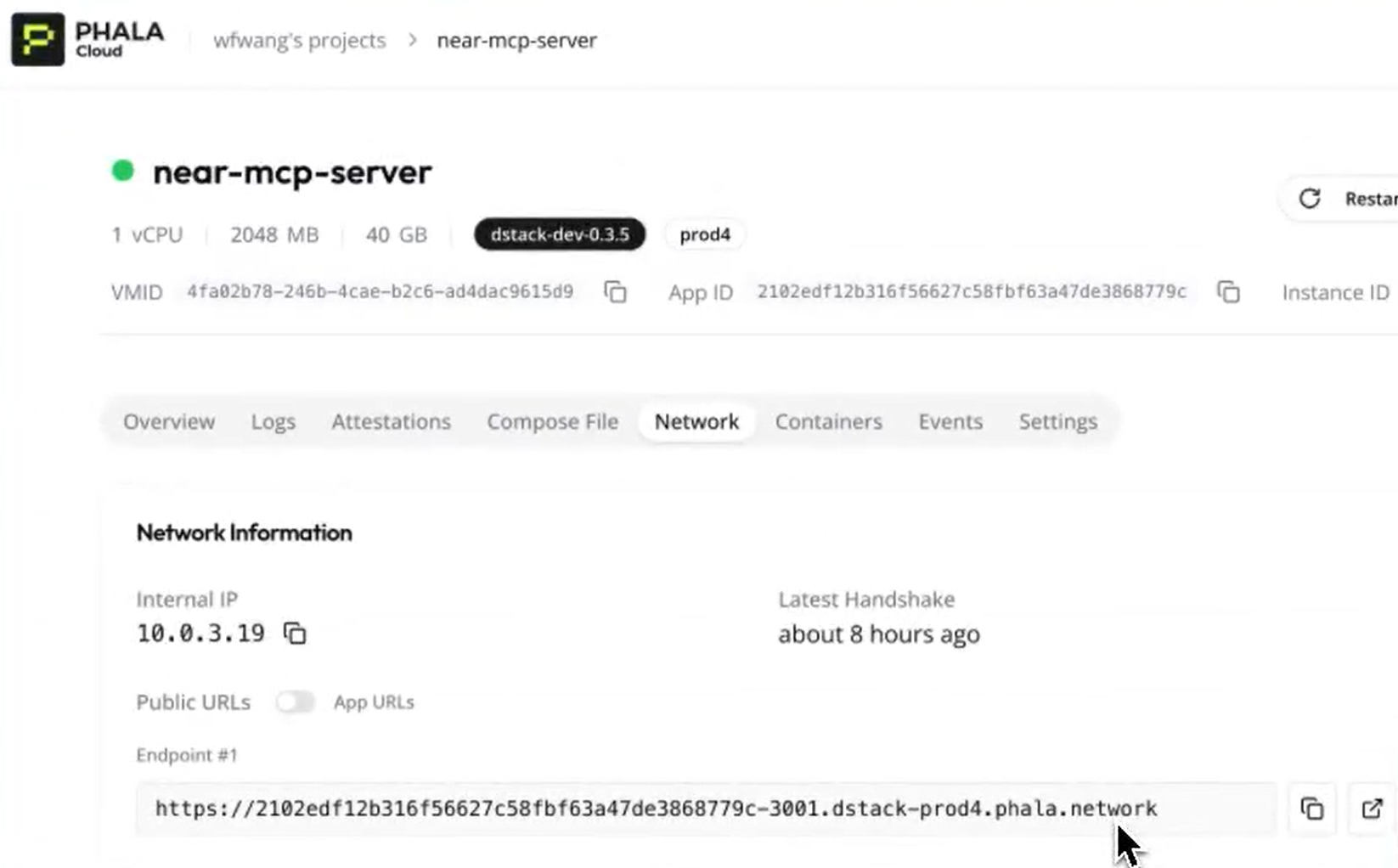
- Switch to the “Containers” tab in the Phala Cloud dashboard.
- Find your container (e.g., near-mcp-server) and check the logs. You’ll see the SSE endpoint listed on port 3001, indicating the server is running.
- To access the Crypto Wallet MCP server, you’ll need the public endpoint generated by Phala Cloud. Go to the “Network” tab, copy the public endpoint URL, and append `/sse` (e.g., https://your-endpoint/sse).
Step 6: Connect to AI Tools (Cherry Studio or Cursor)
- Open your AI tool of choice:
- Cherry Studio or Cursor: Add the MCP server by configuring the SSE endpoint you copied (e.g., https://your-endpoint/sse). In Cursor, go to Settings → MCP page to set it up.
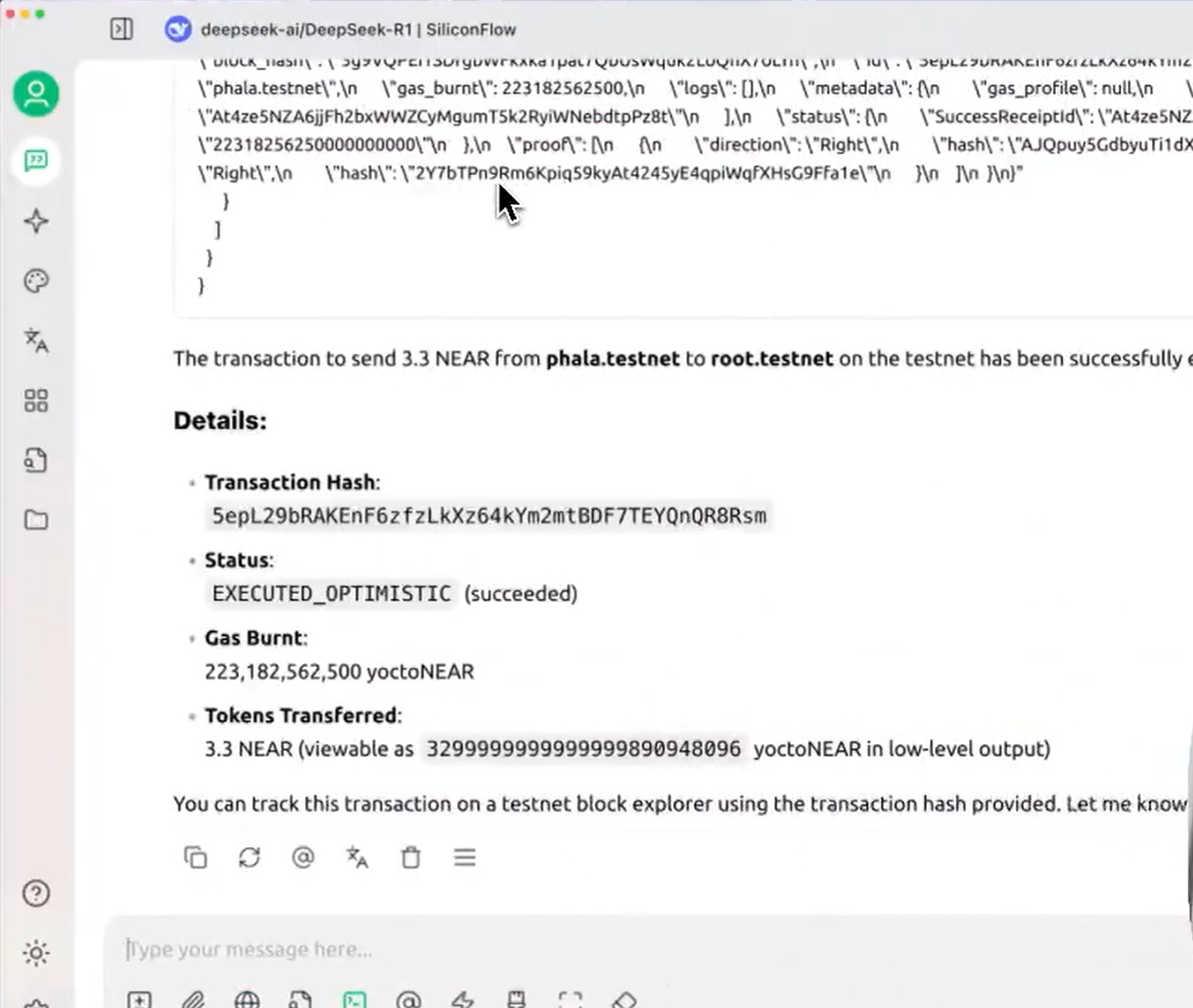
- Start interacting in the chat window. For example, you can prompt the AI to check your wallet balance or sign a transaction on the NEAR testnet. Check out this demo to see how Cursor interacts with the NEAR AI MCP server, showcasing secure wallet operations.
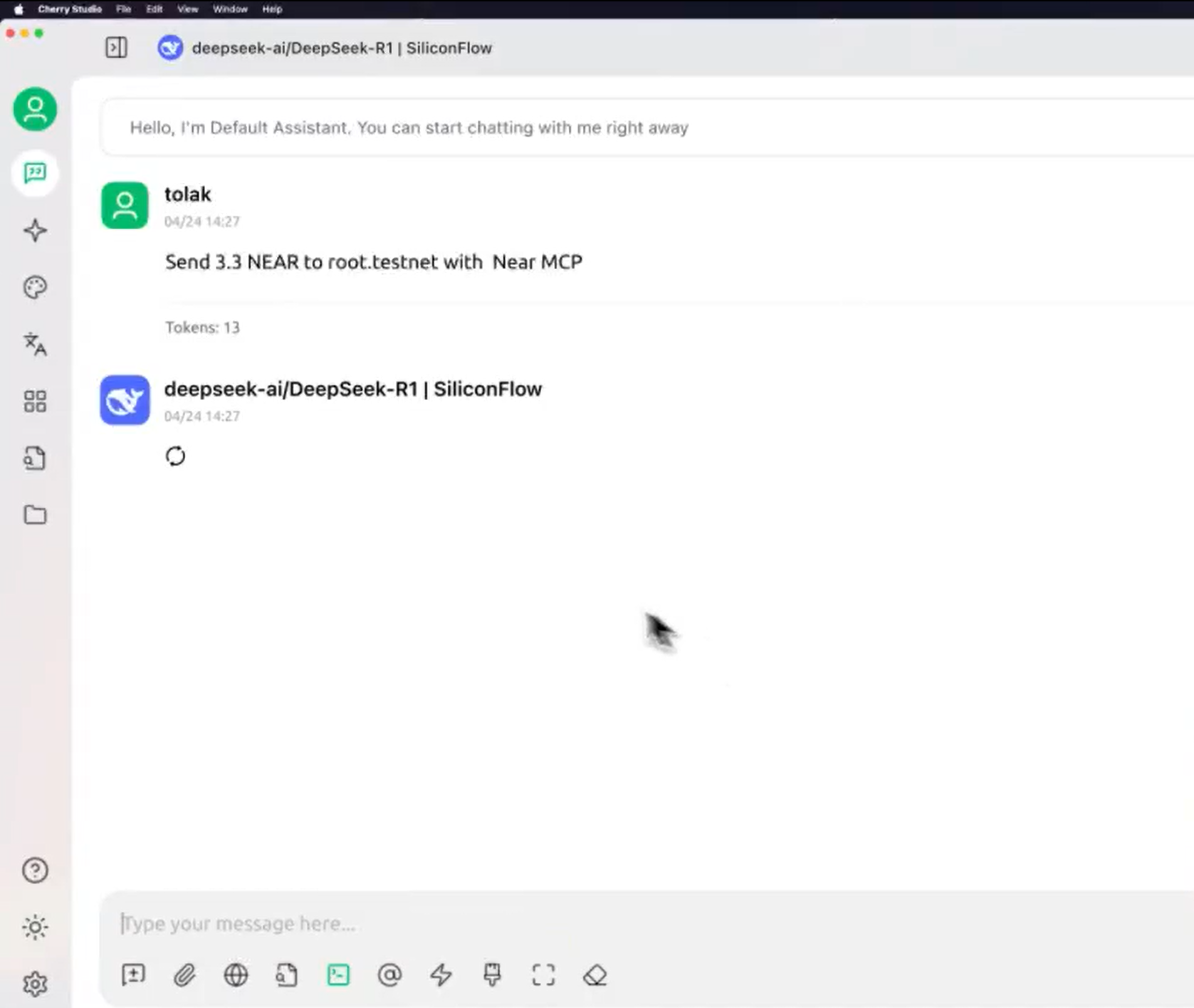
- Your AI tool can now securely communicate with the Crypto Wallet MCP server, with all private key operations protected by the TEE.
Step 7: Verify Your Crypto Wallet MCP Server’s Security
Security is critical for crypto wallets, and Phala Cloud makes verification simple:
- Navigate to the “Attestation” tab in your CVM dashboard.
- You’ll see the attestation report—proof that your Crypto Wallet MCP server is running in a TEE. Click “Check Attestation” to verify it on the explorer.
This ensures your server is secure, protecting your private keys from leaks and hacks while building trust with users.
What You Can Build: Secure Crypto Wallet Use Cases
With your Crypto Wallet MCP server live on Phala Cloud, here are some ideas to explore, all secured by TEEs:
- Automated Trading Bot : Build a bot that uses AI to monitor market conditions with on-chain data and execute trades, with private keys safely isolated in the TEE.
- Portfolio Management: Create a tool that tracks your crypto wallet balance and suggests rebalancing strategies, ensuring secure blockchain interactions.
- Secure Transaction Signing: Develop a web app with React that lets users sign transactions on Bitcoin, Ethereum, or any other blockchains, with the Crypto Wallet MCP server handling key operations securely.
- Decentralized Finance (DeFi) Integration: Build a DeFi dashboard that interacts with on-chain data, using the MCP server to manage wallet operations without exposing keys to local machines.
These use cases show how Phala Cloud’s secure hosting can enhance your crypto wallet projects, ensuring safety and efficiency.
Why Phala Cloud Matters for Developers
Phala Cloud simplifies MCP server deployments while prioritizing security. TEEs prevent attacks like memory leaks and hacks, attestation builds trust, and our open-source Dstack SDK lets you verify every step—no hidden risks, no vendor lock-in. You’re launching in days, not weeks, with affordable scaling. This efficiency means faster builds, safer apps, and more confident users, whether you’re working on NEAR, Ethereum, or other blockchains.
Get Started with Phala Cloud Today
Ready to secure your crypto wallet with a Crypto Wallet MCP server on Phala Cloud?
Sign up for Phala Cloud, claim your $20 in free credits, and deploy your server today.
Need more help? Explore the Phala Cloud Blog for insights, or join our Telegram chat for support. Dive deeper with our documentation.
Phala Cloud is your partner for secure, scalable crypto wallet development.